Have you ever been asked to look for a new type of threat or investigate a security alert, only to be presented with a blinking prompt in a search box and no idea where to start?
With Cribl Copilot and Cribl Search, your life is about to change. With Copilot, you have a collaborator at your fingertips to not only help you craft queries, but more importantly, a partner to help you define the questions to ask. Think of it as a junior SOC analyst who lives inside your browser. Cribl Copilot can help propose relevant questions and write the Cribl Search syntax to answer them. Because it’s embedded directly in the product, every suggestion is context-aware, explainable, and always keeps you (the human) in charge.
Cribl’s AI Playbook: Human-in-the-Loop, Always
Cribl doesn’t limit itself to bolting a generic chatbot onto enterprise telemetry. Instead, our AI strategy follows core tenets:
Steerable – You are always in control.
Strategic placement – Copilot is integrated thoughtfully to help engineers accomplish tasks, where they work, not as a separate silo.
Explainable outputs – Outputs provide plain-language context so you know why it matters.
The result: Faster insights without blind trust in black-box AI.
Copilot for Search Addresses the Pain Points of Log Analytics?
Copilot in Action: Threat Hunting in AWS VPC Flow Logs
The following is an excerpt from a live demonstration. The demo leverages a dataset named “cribl_search_sample” containing AWS VPC Flow logs (Hint: this sample dataset is loaded by default in all Cribl Search instances). The scenario assumes that I am a junior analyst who has been tasked to build queries to search the dataset for potential security threats. That is a pretty generic request. In this scenario, we’ll show how Copilot can collaborate with this analyst to begin deriving security threat-related insights…
Step 1 – Find potential threats by
Determine the types of threats that can be identified in the logs.
Outline the query criteria required to find the events.
Write a structured query to find the events (Docs),
Alternatively, I ask Cribl Copilot for some help. That’s what we’ll do…
Cribl Copilot Prompt:
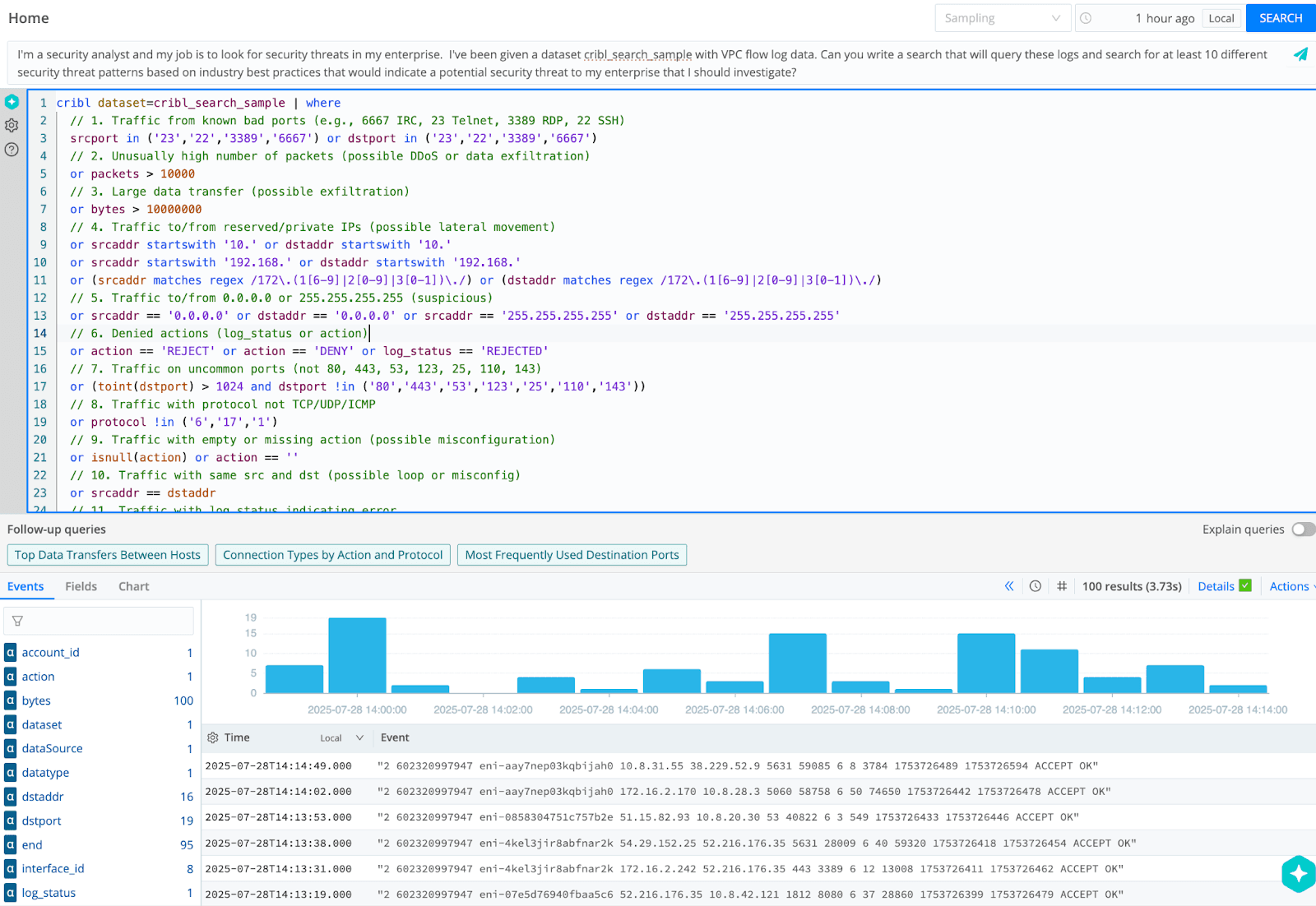
I'm a security analyst, and my job is to look for security threats in my enterprise. I've been given a dataset cribl_search_sample with VPC flow log data. Can you write a search that will query these logs and search for at least 10 different security threat patterns based on industry best practices that would indicate a potential security threat to my enterprise that I should investigate?
Can you also format the query so it is easy to read with comments?
Copilot’s search query and results:
Step 2 – Explain the results
Copilot was kind enough to add comments to the query, but that doesn’t help me or my peers interpret the individual results or take action on them, so now we need to add context to each result. Not to worry, Copilot can help with that too…
Cribl Copilot Prompt:
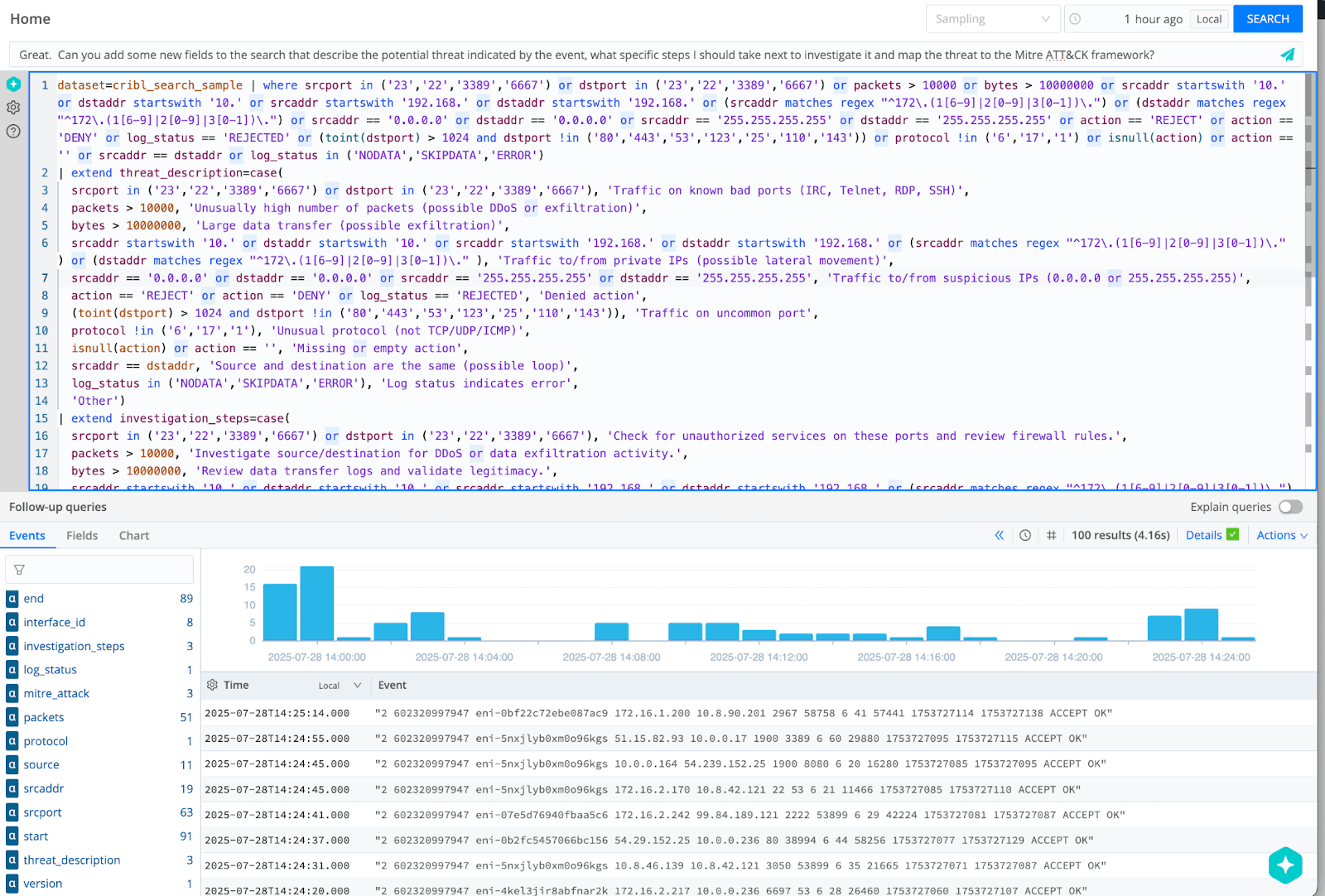
Great. Can you add some new fields to the search that describe the potential threat indicated by the event, what specific steps I should take next to investigate it and map the threat to the Mitre ATT&CK framework?
Copilot’s search query and results:
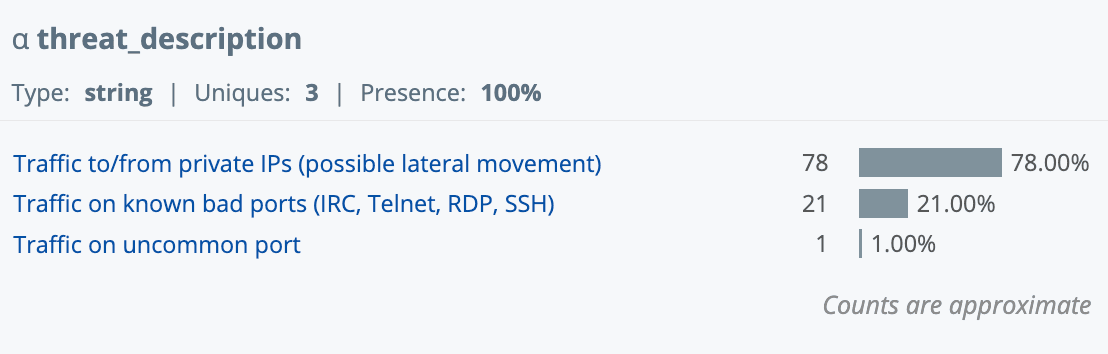
Copilot updates the search to include three new fields for each returned event: threat_description, investigation_steps, and mitre_attack.
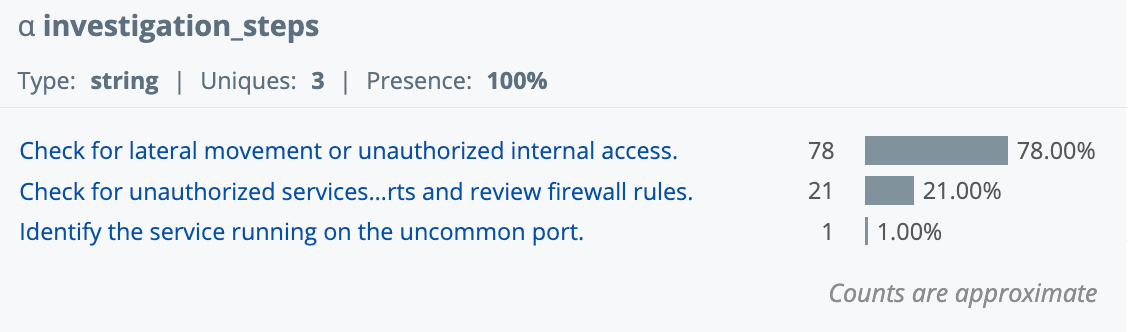
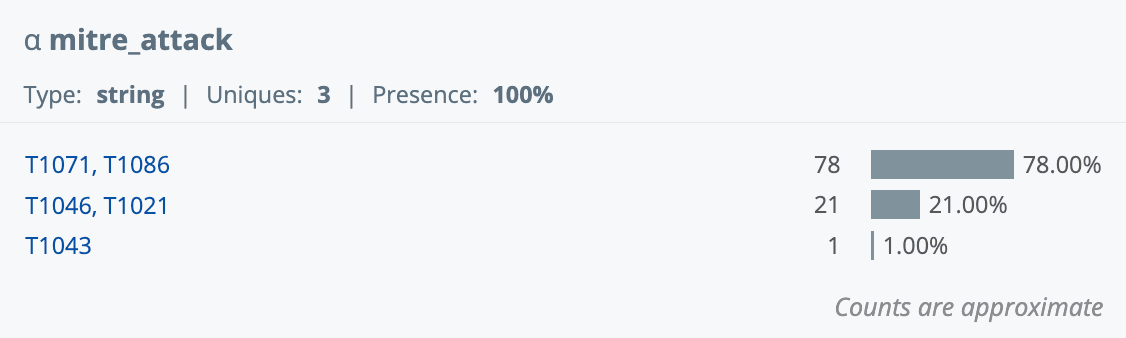
Step 3 – Format the results so they are more readable
Cribl Copilot Prompt:
Can you format the relevant fields from the events into a table and use the new fields you created as the first 3 columns?
Copilot’s search query and results:
Copilot adds commands to output the results as a table and automatically only includes the most relevant fields so they are useful as an alert, on a dashboard or to be shared as an export for use in some other context.
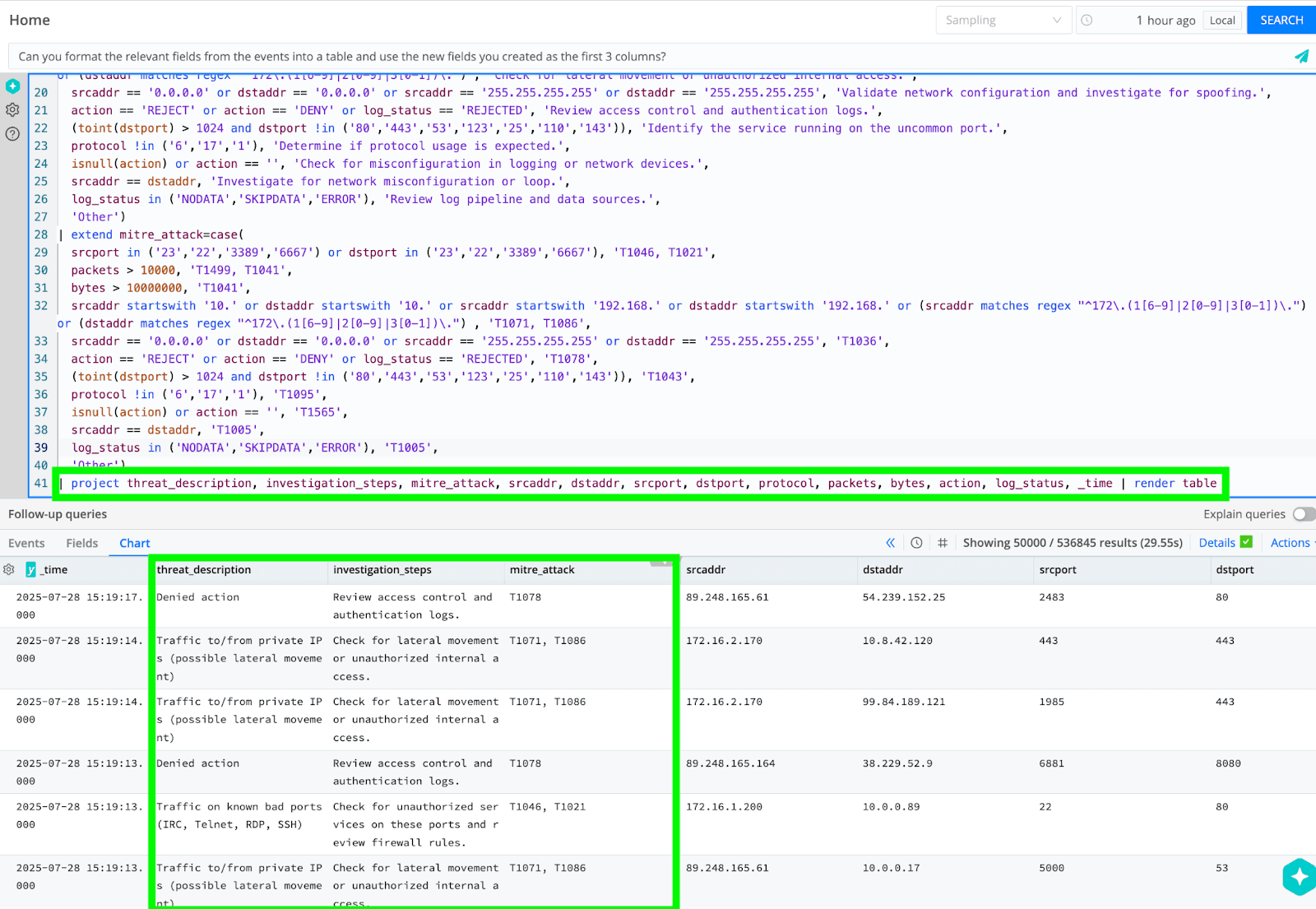
Why This Matters for Security & Observability Teams
Ask Better Questions, Faster – Copilot surfaces blind spots you may not have considered.
Junior Talent Multiplier – New analysts learn by example, seasoned pros offload grunt work
Consistent Frameworks – Reference industry best practice
Continuous Improvement – Every prompt-response cycle sharpens Copilot’s contextual awareness.
Ready to Put a New Analyst in Your Browser?
Spin up a free Cribl Cloud account or sandbox (or update your on-prem deployment).
Open Cribl Search and click the Copilot icon.
Feed it any dataset - firewall, EDR, Kubernetes, you name it.
Type a natural-language request like: “Show signs of lateral movement in my Windows Event logs.”
Iterate, refine, schedule, and share.