Security teams today face constant pressure to move faster, maintain compliance, and handle more telemetry data with fewer resources. With a new integration between Cribl Stream and the Google Chronicle Ingestion API, teams can enrich and route high-volume workloads into Google Security Operations with up to 4x higher throughput. This integration makes it easier to label individual events with precise context before they reach Google Security Operations – helping analysts cut through noise and get to insights faster.
Key benefits for security teams
Add precise context at the event level: Use expression-driven values to add event-level labels for Google Security Operations-bound data. This enables faster pivoting, clearer attribution, and deeper analytics without expanding your parser or rule complexity.
Handle mixed data types with confidence: Apply per-event log type overrides using the
__logTypefield, so you can route multiple source types through a single destination while ensuring the right parser is applied every time.Accelerate throughput at scale: Send larger batches—up to 4 MB per batch—for high-volume data streams to reduce ingestion overhead and speed up processing.
Enhance visibility: By enriching events in-flight before they reach Google Security Operations, teams maintain consistent visibility across mixed data sources without rewriting parsers or restructuring pipelines.
Why this matters
Modern security operations are built on context. Analysts can’t afford to waste time deciphering which system, user, or application a log belongs to. By combining Stream’s enrichment and routing capabilities with Google’s Chronicle Ingestion API, teams gain precise control over how security data is prepared and delivered—making every event more searchable, actionable, and trustworthy.
The result is a data pipeline that performs at the same speed as your investigations. You spend less time fixing ingestion bottlenecks and more time uncovering threats that matter.
Get Started: Prerequisites
Before beginning, ensure you have:
Access to Cribl Stream (admin privileges)
Access to an instance in Google Security Operations
A GCP project ID and customer UUID
A service account key (JSON) with Security Operations write permissions
Please be aware that this integration leverages the unstructured ImportLogs endpoint. The unstructured endpoint relies on Google parsers to land data in Security Operations. More information can be found in Cribl Stream docs.
Step-by-Step Integration Guide
Create a Google Cloud Chronicle API Destination in Cribl Stream
Log in to Cribl. Navigate to Stream and a worker group. Select Data → Destinations

Search or scroll to the Google Cloud Chronicle API tile. Select the tile and select Add Destination.
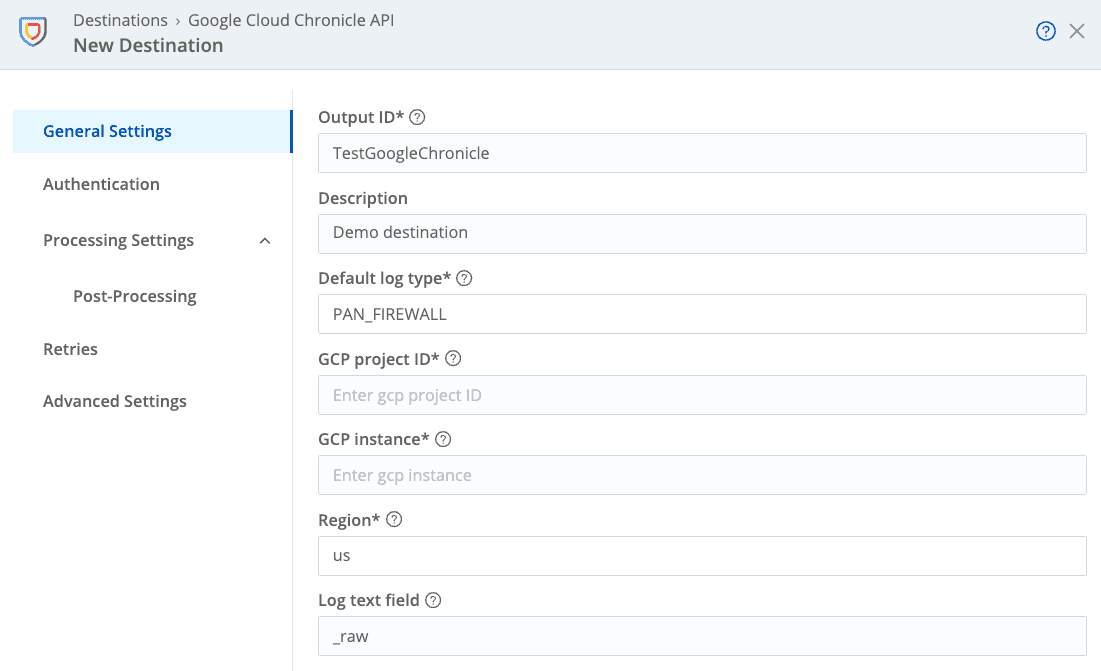
Name the Destination by entering an OutputID. Optionally add a Description.
Select a Default log type from the drop-down menu. This field can be overwritten in Cribl pipelines using the
__logTypefield.
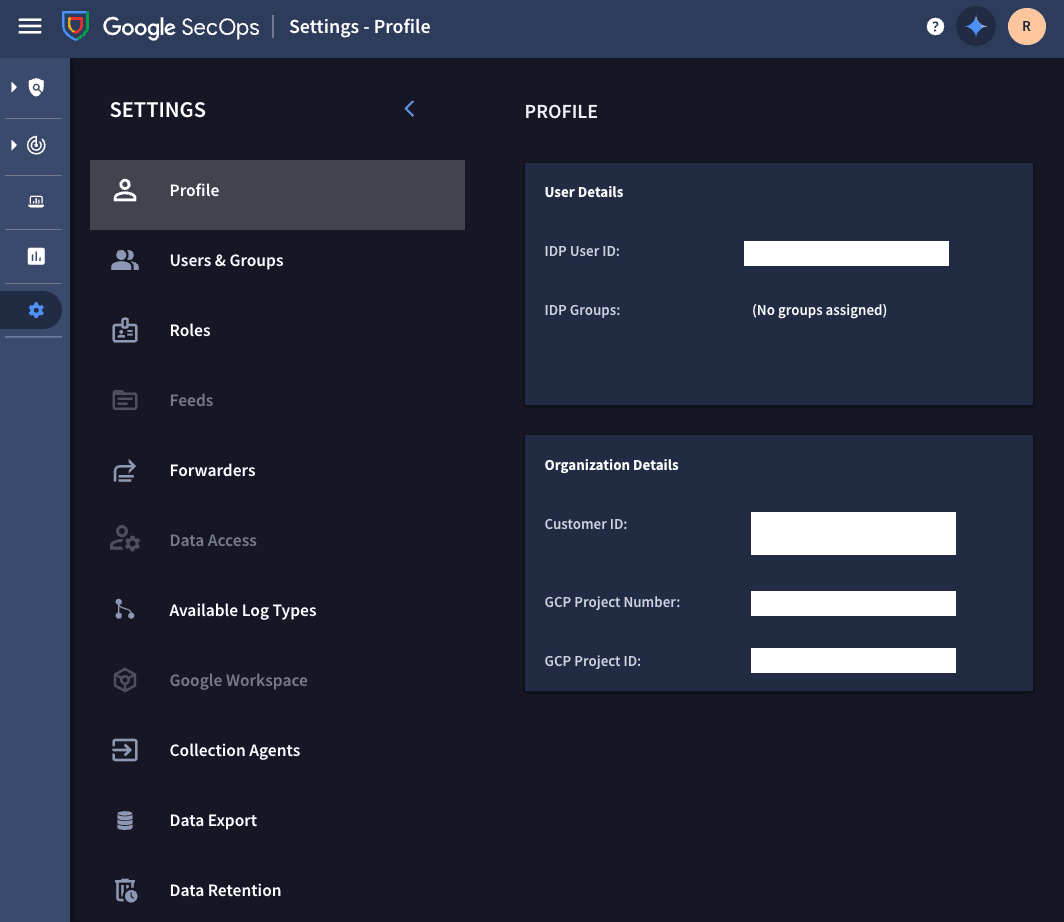
Enter the GCP project ID. This is found in Google Security Operations in Settings → Profile.
Enter the GCP instance. The GCP instance is the Customer ID under Organization Details.
Select a Region
Optionally enter the Log text field. This is the field in the event that contains the log message to parse in Security Operations. If the field is blank, Cribl Stream will send the whole event as a JSON object.
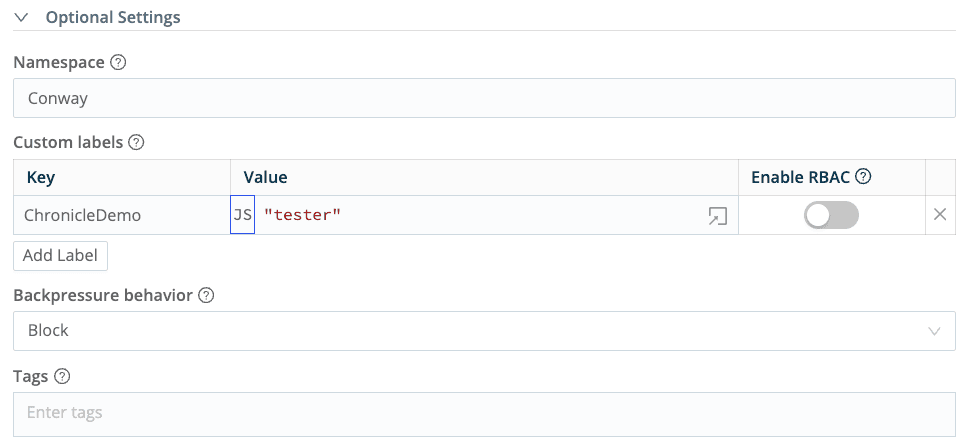
In the Optional Settings, users have the choice to add a Namespace. This can be used to identify events by their domain. The Namespace field will be indexed in Google Security Operations for query optimization.
Custom labels may be added to help tag events as needed. Custom labels are added to individual events based on the Javascript expression in Value.
Optionally select a Backpressure behavior for how to handle events when the destination is experiencing issues and backpressure occurs.
Optionally add Tags.
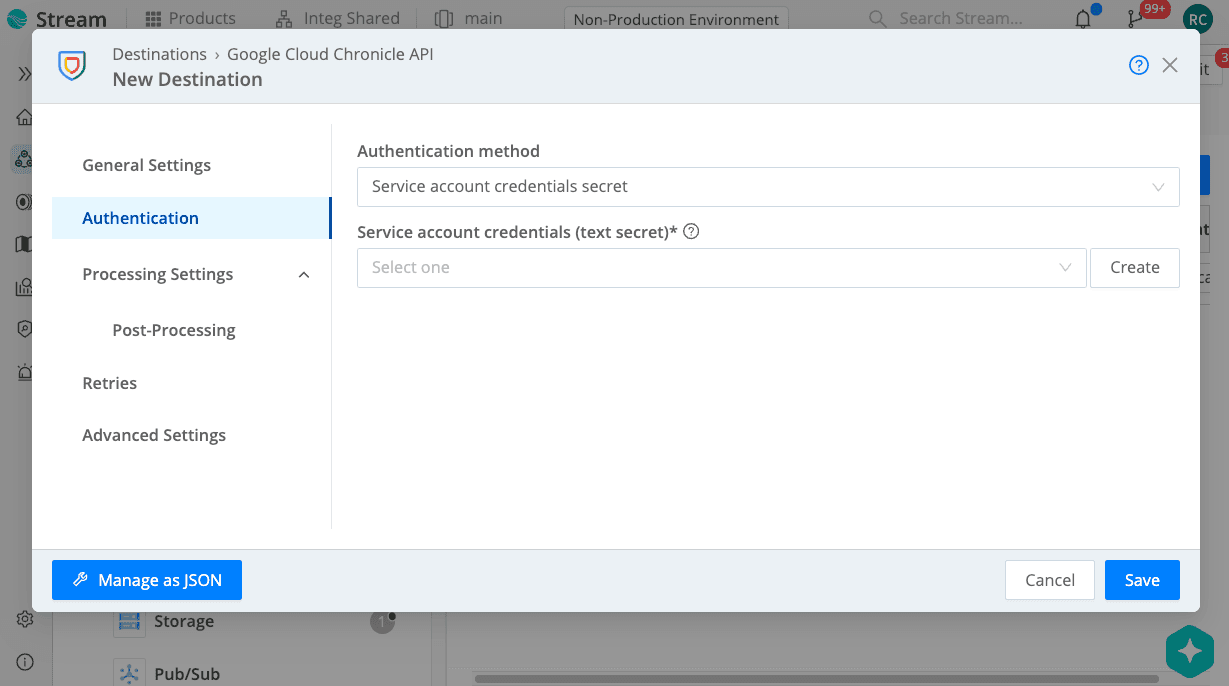
In the Authentication section, select an Authentication method. In selecting Service account credentials secret, select from an existing text secret from the dropdown menu or Create a new one.
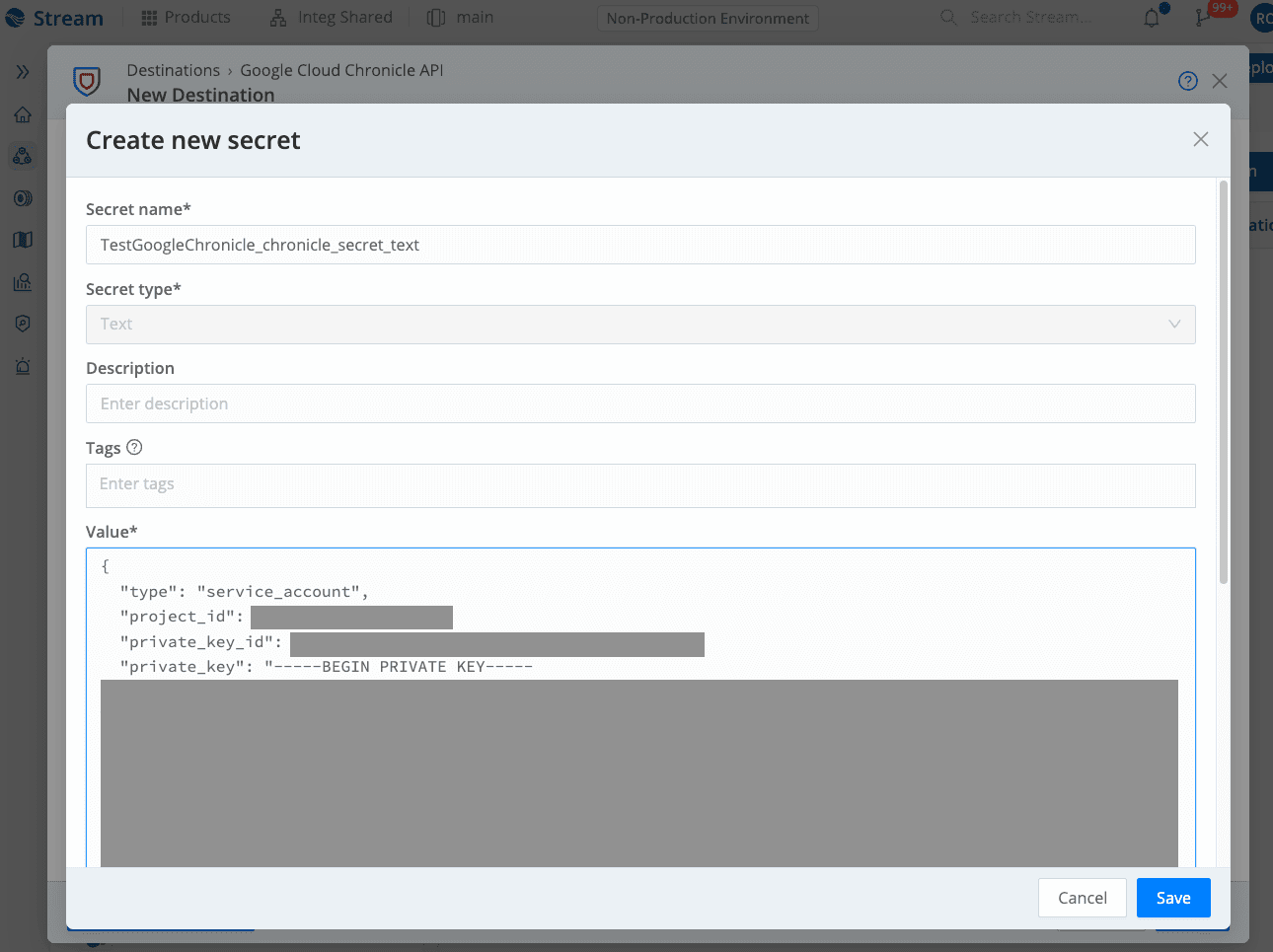
After selecting Create, enter a Secret name, optional Description and Tags. Add the service account credentials as JSON.
Then, Commit & Deploy.
Send a Test Event
From the destination panel, click Test.
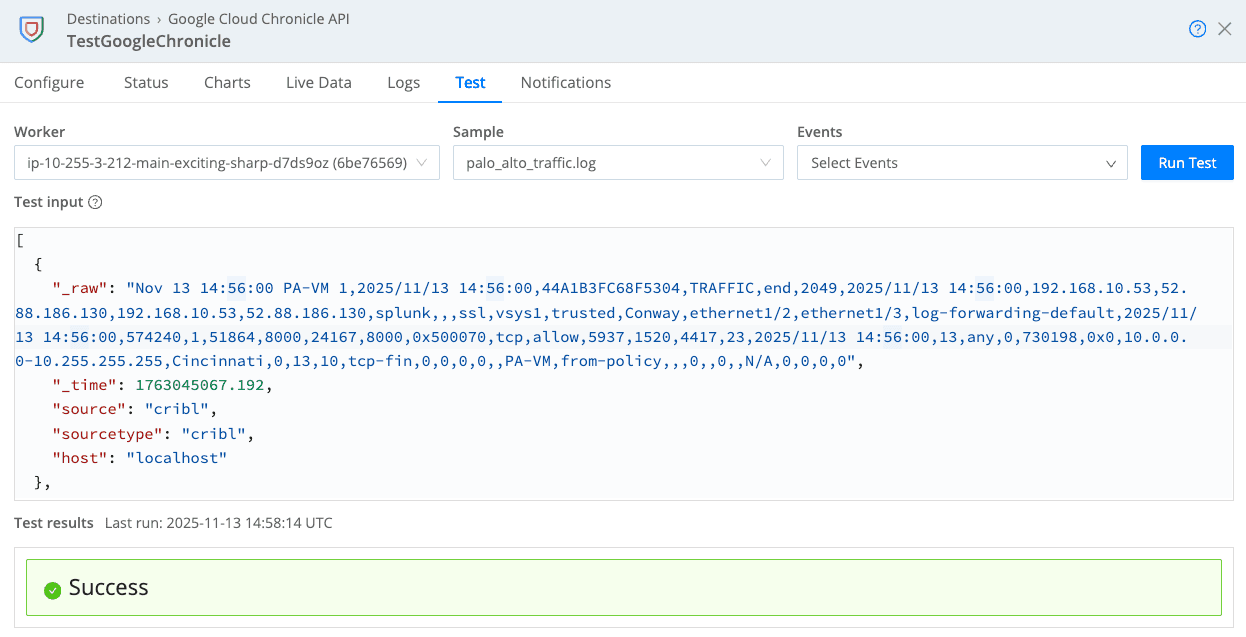
Choose a sample file or paste your own and select “Run Test”
Validate in Google Security Operations
Log in to Google Security Operations.
Open the Search view.
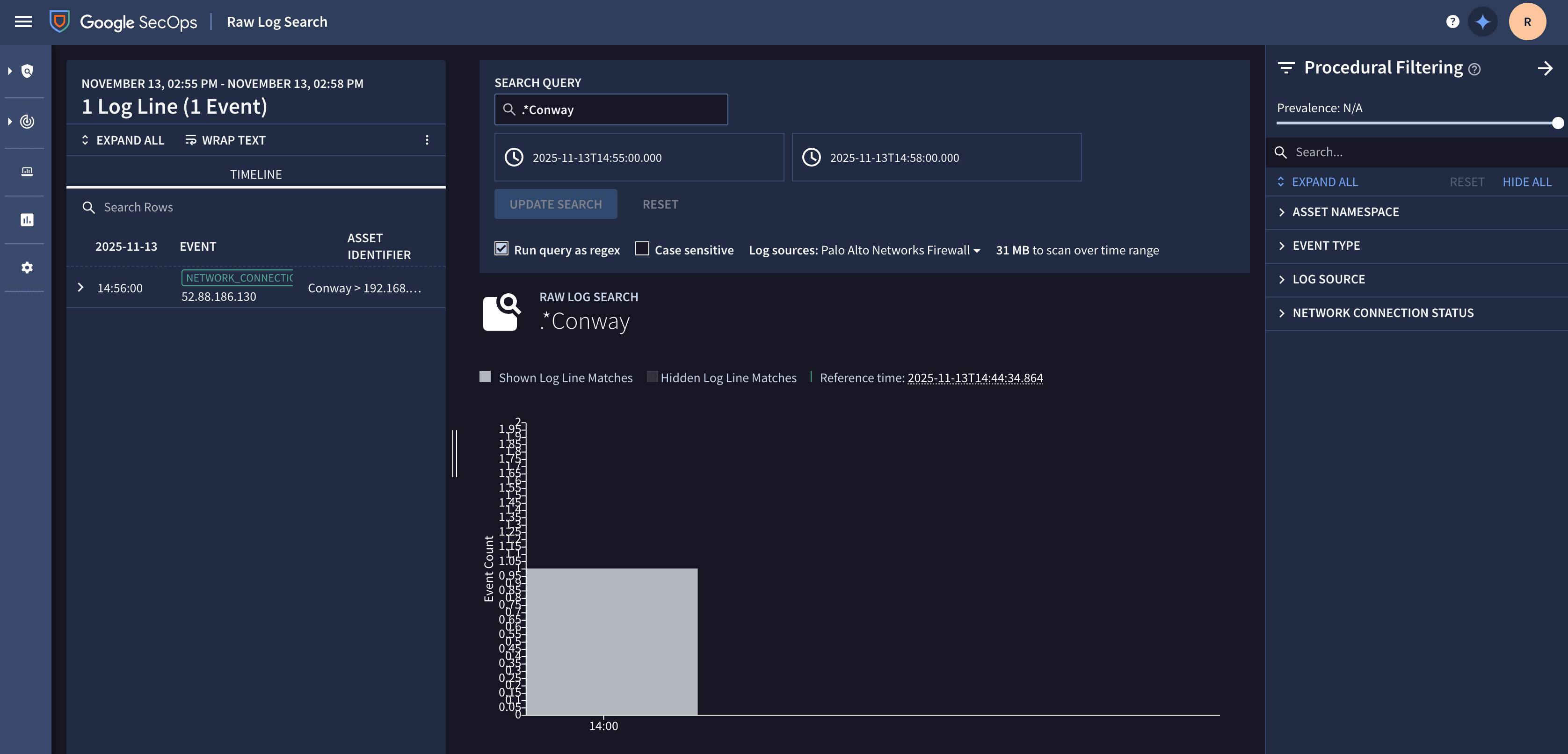
Search by an attribute you configured (i.e. namespace) or by timestamp using the time range selectors.
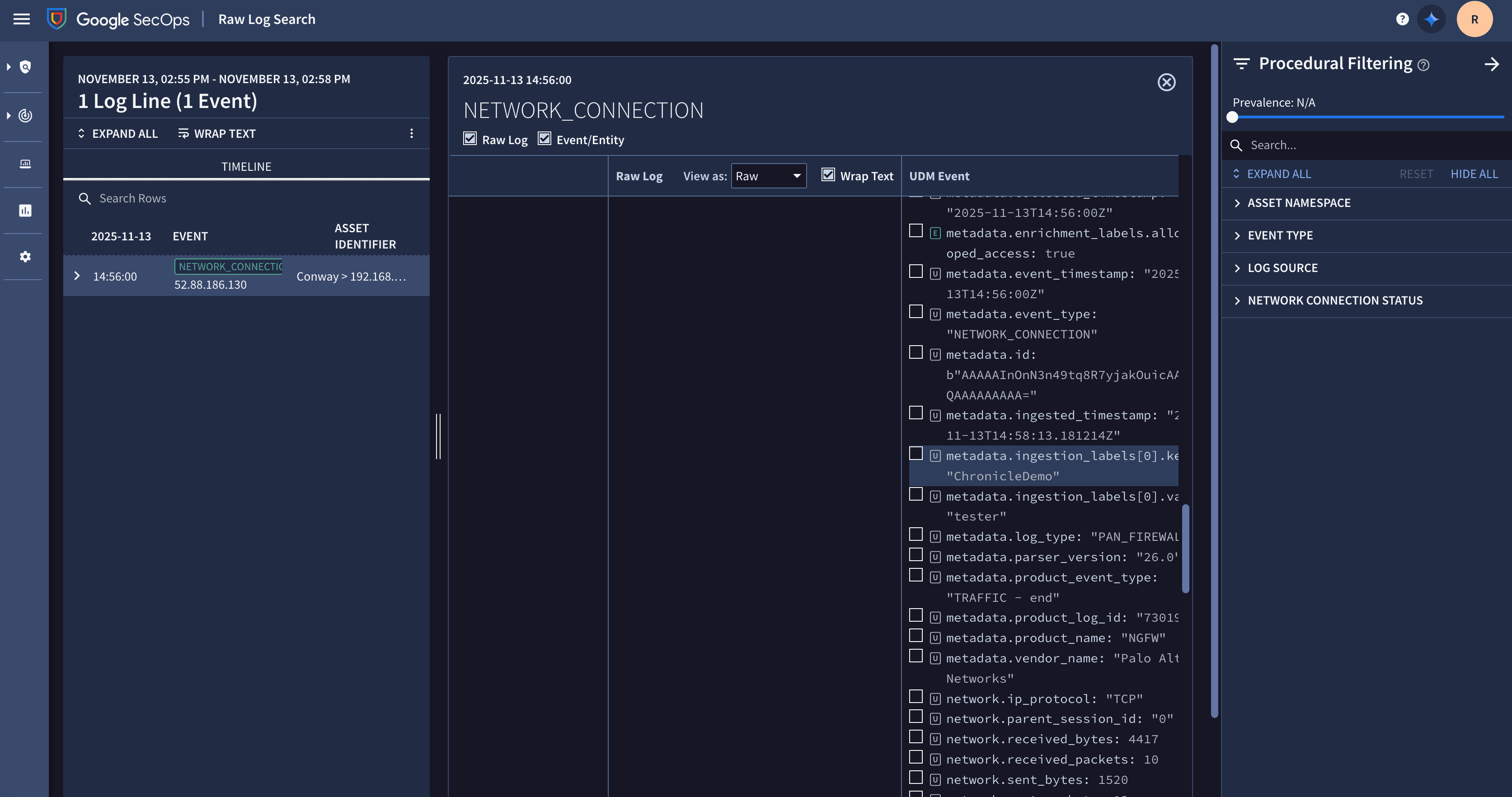
Check that your sample event and labels appear as expected. In the screenshot, notice the ingestion labels applied per event as configured within the Cribl Stream destination.
Troubleshooting Tips
Authentication Errors: Verify your service account key and permissions.
No Events Visible in Google Security Operations: Confirm your project ID and customer UUID are correct. Confirm the timestamp of the data sent.
Pipeline Failures: Check Cribl’s worker logs for Chronicle API response codes.
Access Issues: Work with your IT or IAM team to ensure Chronicle write access for your service account.
Summary
Integrating Cribl Stream with Google Security Operations (Chronicle API) provides a scalable and efficient way to manage security data pipelines. You can shape, enrich, and route telemetry from any source into Security Operations with full visibility and control.
By combining Cribl Stream’s data transformation capabilities with Google’s security analytics, organizations can gain faster insights, data control, and stronger operational visibility across the data security stack.