Your security teams face escalating data volumes, vendor changes, and cost pressures when they migrate between SIEM platforms. Cribl simplifies these migrations by giving you flexible data routing, reducing storage costs, and accelerating time-to-value. How? Let’s look at how a global customer used Cribl Stream to migrate CrowdStrike FDR logs from Splunk to Microsoft Sentinel efficiently and cost-effectively.
The SIEM migration challenge
Security incident and event management (SIEM) platforms are used by Security teams to proactively prevent security breaches within any organization. These SIEM solutions give you visibility into the security health of your organization. Together with various security tools, such as firewalls, EDR, threat intelligence, and DLP, they form the eyes of any SOC team.
The challenge with SIEM or security analytics platforms is the growth in data from your organization’s systems. The move to containers/cloud computing has exacerbated the rate of growth. And that growth is just going to accelerate further every year.
To add to this complexity, next generation security tools, like extended detection and response (XDR), are incorporating artificial intelligence into their capabilities. The dynamic and changing landscape in this space ensures both security practitioners and their contemporaries must stay on their toes figuring out how to protect their environment or even to look for vulnerabilities in their network, such as penetration testing.
Constant mergers and acquisitions in the security vendor space add still more change. Customers need to be agile with the best tool for their requirements. At the same time, they need to keep their networks secure against malicious attacks (both internal and external). And they have to be smarter with their TCO as the amount of data keeps increasing.
How to crack the code
This means security professionals need to decouple the logs into the right destination without losing fidelity. One of the biggest challenges with the logs here is that the key information can be parsed before reaching its destination in real time. Cribl has the capability to integrate with all data sources (for example, Sailpoint API, Palo Alto Firewalls, CrowdStrike FDR) and extract the key value pairs from the raw fields. Now you can also drop null values, non-CIM fields, syslog headers, and duplicates before routing to the right SIEM.
You can also route a copy to your own blob storage, such as Azure Blob, AWS S3, and Google Blob. This ensures that your compliance requirements are met and, if required, logs can be replayed (rehydrated) back to the SIEM for investigations.
You can reduce costs just by using this method to avoid paying extra for high-performance disks, like Splunk Cloud Dynamic Data Active Archive (DDAA) or additional storage in Microsoft Sentinel’s active storage beyond 90 days.
How a customer migrated CrowdStrike FDR from Splunk to Microsoft Sentinel
Additionally, the Swiss-Army-Knife flexibility of Cribl is validated further by parsing the raw fields and routing only the fields that are required by the Destination of choice. Here’s an example where the customer had CrowdStrike FDR which routed first to Splunk and then migrated to Azure Sentinel. Cribl was able to pull the right logs from CrowdStrike’s FDR and parse the fields before routing the key fields to the CrowdStrike table (CrowdStrike_Additional_Events_CL) in Microsoft Sentinel.
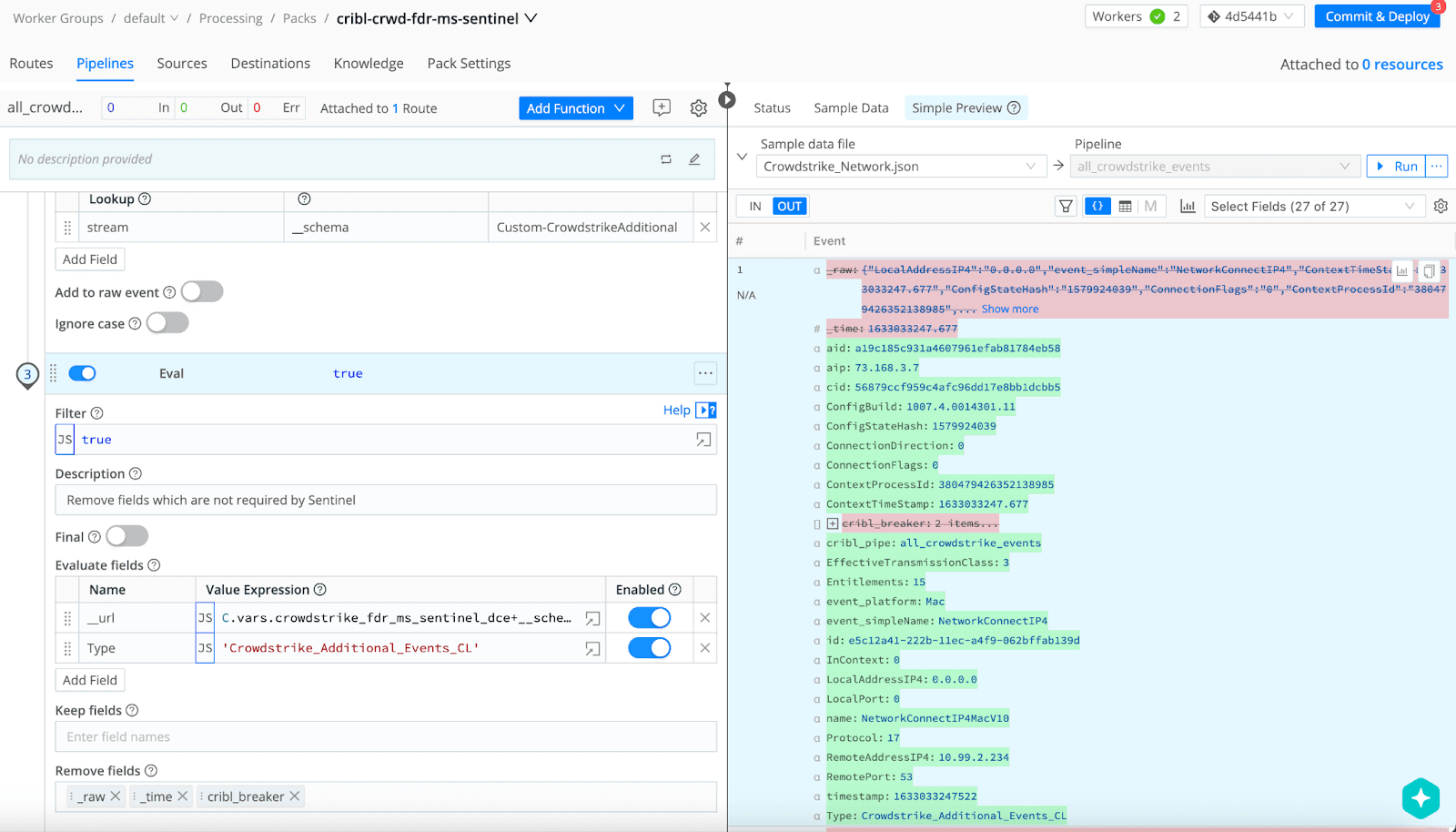
This ensured the analytics in Microsoft Sentinel for CrowdStrike FDR ran even after they were parsed through Cribl. Similarly, customers have used the Cribl Pack for Microsoft Sentinel to help them optimize and parse the right fields to the respective Microsoft Sentinel tables.
Operational, cost, and compliance benefits with Cribl Stream and Cribl Search
We were also able to optimize the raw data ingested into Microsoft Sentinel and gain more value from their security investment by sending more data without increasing their licensing costs. This helped the customer be on top of their TCO. And they were able to save on professional services costs as they could make the migration move faster in a short period of time.
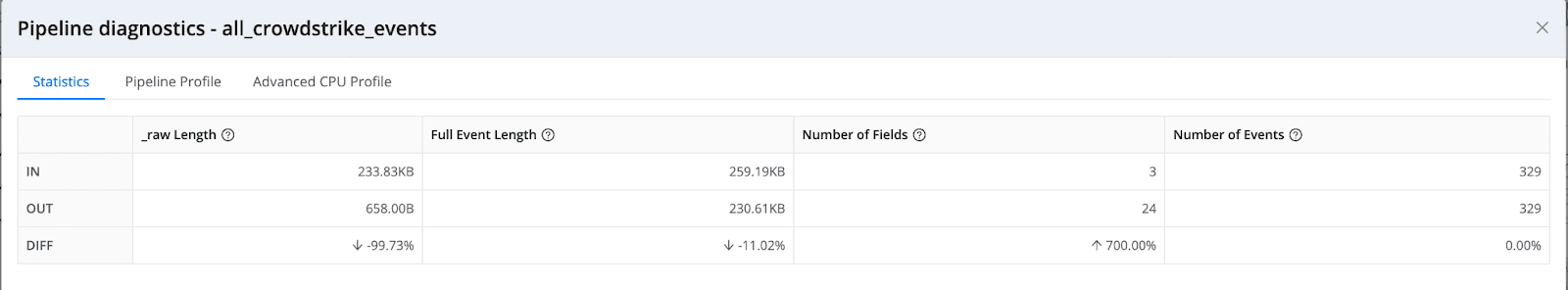
Similarly, Proofpoint and Auth0 logs were routed via Cribl to Microsoft Sentinel and immediately the respective tables in Sentinel were populated with the right fields for the analytics to work.
The other advantage of routing via Cribl was the choice of routing a copy of full fidelity logs (unaltered) to cheaper storage for compliance and security investigations. This way the customer was able to pay only for the default 90 days storage (hot) and not pay for additional hot storage. They had a copy of full fidelity logs already routed to Azure Blob Storage where they can easily rehydrate via Cribl stream.
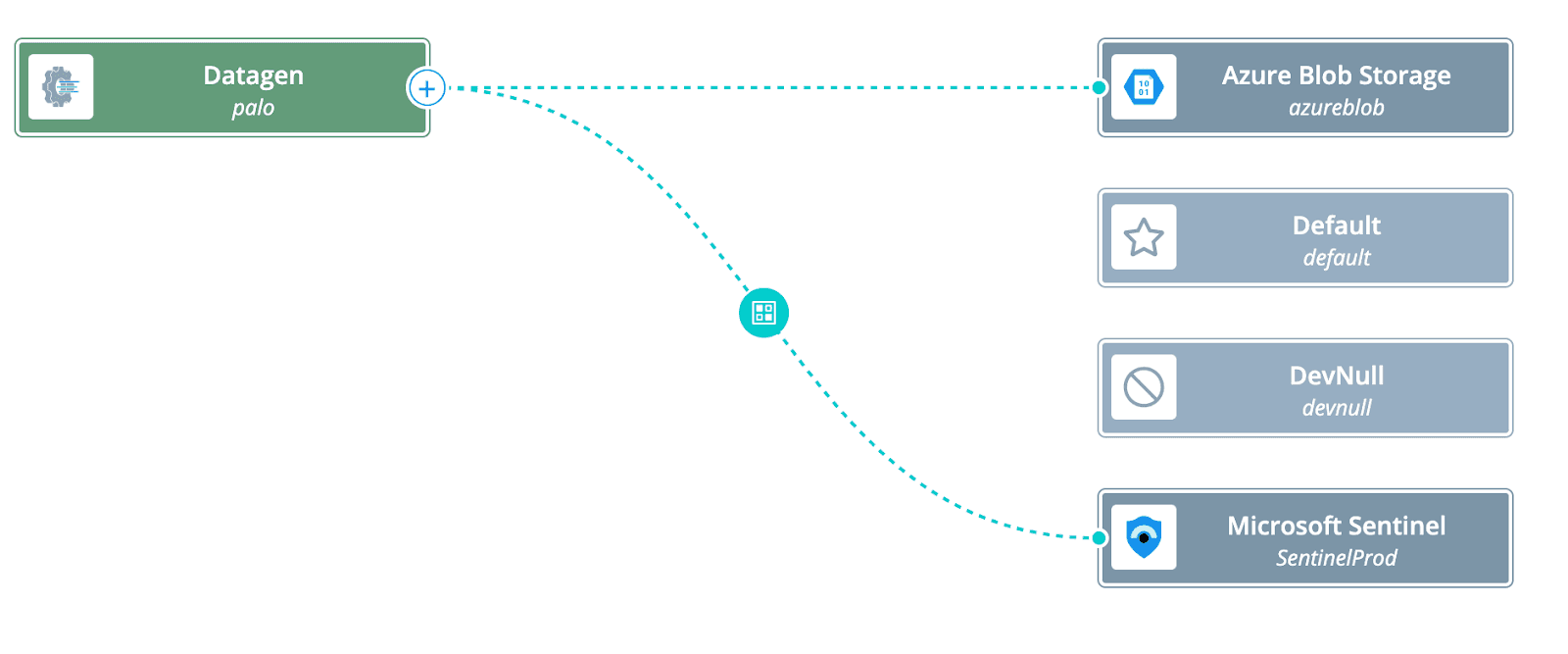
They were also able to use Cribl Search to search their blob storage when required, ensuring their compliance requirements were met. Cribl Search uses Kusto Query Language (KQL) as its searching language.
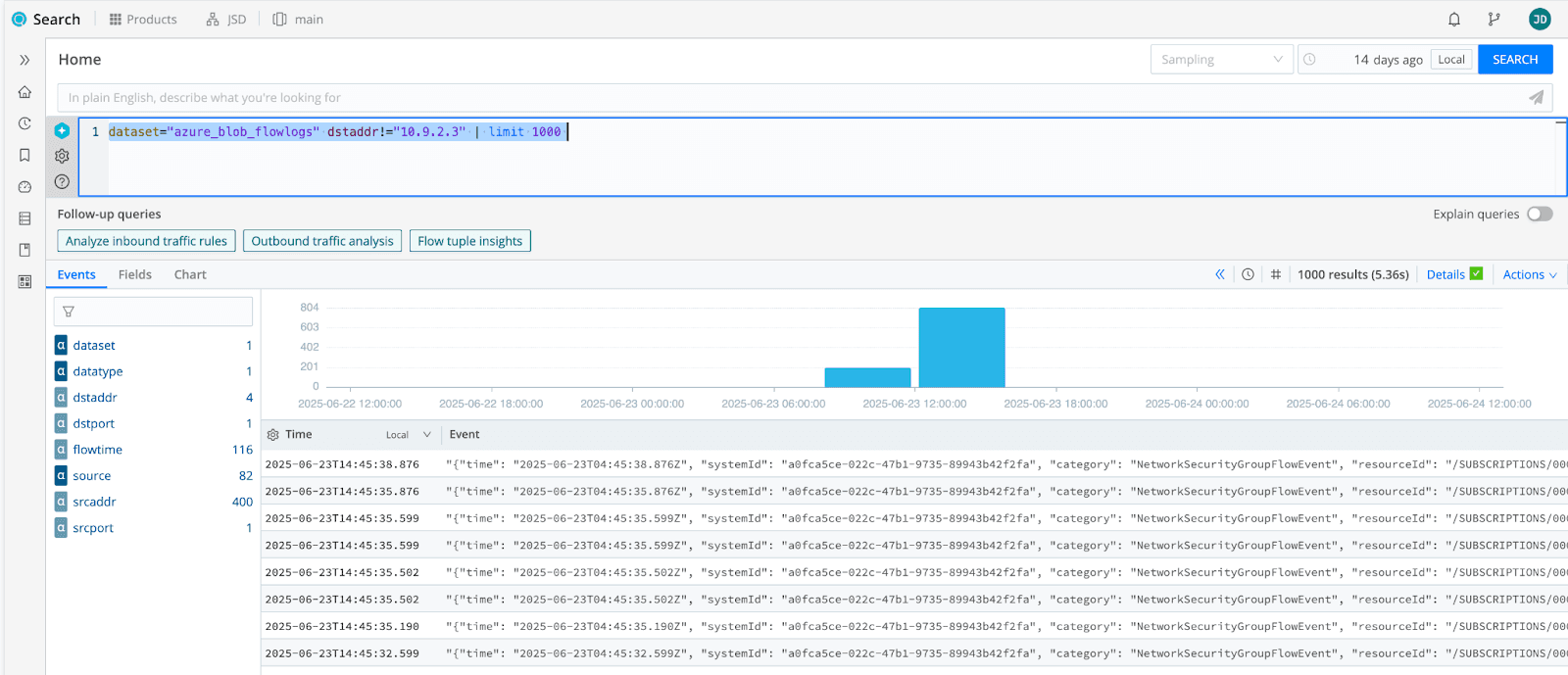
The speed of getting data sources into Microsoft Sentinel via Cribl helped the customer meet their migration deadline and saved them a substantial amount in their contract negotiations with their previous supplier. And in the future, if they decide to test a new SIEM/security analytics solution, they can move with ease as Cribl is already in their data pipeline and allows them to work with any destination of their choice.








