Organizations deploy Microsoft Sentinel as a foundational layer in their multi-tiered security architecture. This cloud-native Security Information and Event Management (SIEM) platform enables real-time threat detection, incident response, and compliance enforcement while integrating seamlessly with the Microsoft ecosystem.
The cybersecurity landscape is changing. Evolving regulations, increasing telemetry, aggressive threats, and staff shortages are prompting security teams to rethink their SIEM architectures. Although a SIEM is central to detection and response, its implementation and management can overwhelm Security Operations Centers (SOCs), taking up valuable analyst time and risking missed breach indicators. As on-premises or legacy SIEM solutions struggle to keep pace, security teams want to migrate, but few know how to do so efficiently, effectively, and without the risk of degrading the enterprise’s security posture.
This whitepaper provides eight strategic steps to guide a migration to Microsoft Sentinel, setting your organization on the course for an effective and efficient detection, response, and research program. It highlights the advantage of using Cribl to:
De-risk and accelerate your Sentinel migration
Modernize your security data strategy
Maintain and improve data quality
Successful migrations require a substantial time investment. However, several of the major steps outlined here can proceed in parallel.
This guidance is tailored for leaders and key technical stakeholders to ensure the successful execution of a Microsoft Sentinel migration project and to contribute to the long-term success of an organization’s entire cybersecurity detection, response, and research program. This may include your data lake, threat hunting, UEBA (User and Entity Behavior Analytics) data platforms, and more.
Why migrate to Microsoft Sentinel?
Cyberattacks are on the rise, but there aren’t enough skilled security analysts to keep up. Telemetry data is also growing at a staggering rate of 30% CAGR, creating massive implications for storage and analysis. This exponential growth in data volume challenges organizations to find cost-effective ways to store, process, and derive value from their security telemetry.
At the same time, organizations are dealing with more security events and devices than ever before, putting a heavy strain on their legacy SIEM systems. This further challenges security teams, who often waste valuable time responding to false alarms or irrelevant alerts. Many of these issues stem from outdated SIEM technology.
According to a recent IDC Survey Spotlight, companies want to replace their SIEM for cost, functionality, ease of use and better data management.
Source: Worldwide Views on SIEM Survey 2024, IDC, January 2024
Even though organizations invest heavily in these systems, they often feel stuck with their existing tools due to budget constraints, data gravity, and concerns around operational disruption. But older SIEMs come with several significant drawbacks:
High storage costs: As businesses adopt modern security approaches like zero-trust policies and cloud-based services, they generate massive amounts of security data. Older SIEMs store logs indiscriminately, leading to rising storage costs without adding meaningful security benefits.
Failure to detect new threats: Many traditional SIEMs depend on basic rules and third-party alerts to identify risks. However, these outdated methods struggle to detect new and evolving cyber threats, making organizations more vulnerable.
Inability to track complex attacks: Legacy SIEMs often fail to connect the dots when attackers move across different systems. Hackers might use stolen credentials to access networks in unrelated ways, making it harder for security teams to see the full picture. This fragmented approach increases the chances of missing serious threats.
Slow, manual investigations: Older SIEMs lack automation for critical security tasks. As a result, security teams must manually piece together attack timelines and incident reports, which is time-consuming and inefficient. This slows down response times and increases the need for skilled analysts — who are already in short supply.
On-prem overhead and rigidity: Running a SIEM on-premises requires ongoing investment in infrastructure and staff time to maintain and tune the system. Many legacy deployments also lock organizations into fixed license costs, limiting flexibility and adding unnecessary expense.
Before: The reality of data growth
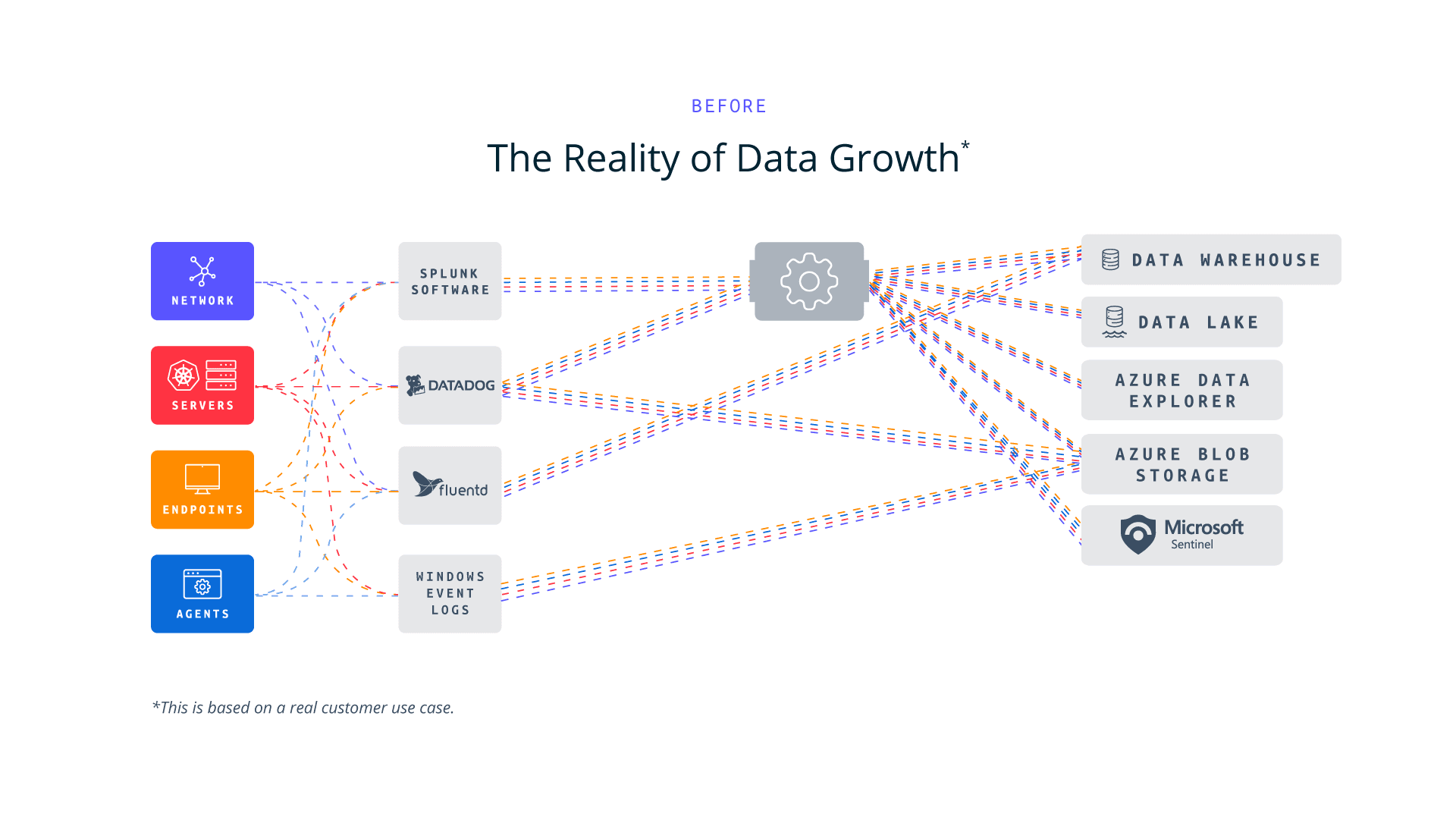
With these drawbacks, it is easy to see why enterprises are looking for better options, such as Microsoft Sentinel. Sentinel offers scalable performance, advanced threat detection, built-in AI, cloud hosting with simplified configuration, pay-as-you-go pricing, and native integrations with the Microsoft ecosystem — including other Microsoft security tools, such as Microsoft 365 Defender. While the desire to migrate is strong, organizations cannot simply hit a switch to move from one product to another. The business must still be protected. By using a telemetry pipeline, like Cribl Stream, security teams can migrate to Microsoft Sentinel while maintaining three core requirements:
Preserving full security posture during the migration process
Porting only optimized data to Microsoft Sentinel, in the required formats
Maintaining control over data ingest and data quality after your migration to Microsoft Sentinel
Before switching, stakeholders must consider how these changes impact existing workloads and plan accordingly. The following sections explore these factors in more detail.

Customer Success
The University of Pittsburgh’s IT Security team was struggling to manage massive volumes of unstructured security data, making it difficult to normalize logs and fully realize the value of their SIEM. To modernize their operations, they chose to migrate to Microsoft Sentinel and used Cribl Stream and Cribl Edge to accelerate the process. By building pre-processing pipelines that parsed, normalized, and enriched log data in real time, the team completed the migration in just 68 days. The result was a streamlined SIEM environment with unified and searchable logs, reduced ingest costs, and simpler management across more than 1,000 servers.
Cribl has significantly improved our data management, making operations smoother. For a small team with extensive responsibilities, Cribl has been an invaluable asset.
— Richard McIver, Senior Security Engineer // University of Pittsburgh
Leveraging a telemetry pipeline during the migration process
According to a recent IDC Survey, a top SIEM challenge is that data ingestion is too complex and expensive.
Source: IDC’s Worldwide Views on SIEM Survey, January 2024.
Any SIEM migration is a complex process. The data is often intricate, and SIEM content is often vendor-specific, meaning that transitioning to a new platform requires time and training. Furthermore, security teams might not be the only users of your existing SIEM’s capabilities. Years of effort have gone into legacy SIEM platforms, and it’s not unusual for the scope to extend to non-security teams that use the data for operational purposes. Organizations need to consider these non-security workloads and determine where they will exist post-migration.
As with any migration, migrating to Microsoft Sentinel can involve business, technical, and operational challenges. Extensive planning and careful strategy are essential to ensuring that your migration proceeds correctly the first time, and to minimize rework.
Migration challenges: Which is yours?
Business challenges might include:
Migration risks (downtime, overruns, or poor adoption) can derail ROI.
Compliance obligations add to migration cost and complexity.
Technical challenges might include:
Integration with existing tools and workflows is often complex.
Data gravity (diverse formats must be normalized to new schemas).
New SIEM must prove equal or superior accuracy before cutover.
Operational challenges might include:
Migration must minimize disruption and prevent data loss.
Non-security workloads must remain supported through and after migration.
Analyst retraining (ideally, streamlined through new SIEM’s automation, natural-language querying, and intuitive reporting features).
Incorporating a telemetry pipeline into migration can address and streamline many of these concerns.
Enhancing performance with a flexible data pipeline
As organizations strive for greater agility and efficiency in their security operations, a modern data architecture provides a flexible and scalable foundation. A telemetry pipeline allows teams to optimize their existing SIEM deployments, accelerate the adoption of new security tools, and seamlessly transition between platforms as their needs evolve. By decoupling data ingestion from a specific SIEM solution, security teams gain the freedom to adapt quickly to changing threats, improve resource utilization, and enhance overall system performance, regardless of their current SIEM infrastructure or future technology choices.
Parallel routing facilitates comparison, reducing risk
A telemetry pipeline accelerates and de-risks a Sentinel migration because it sits between an organization’s sources and destinations to support feeding both the legacy SIEM and Sentinel simultaneously. This enables the business to maintain its security posture in the legacy SIEM while cloning the full production dataset to Sentinel. This powerful capability enables the migration team to build content in Sentinel and thoroughly test everything without risk to its security posture. No ugly hacks or hard cutovers are required. No testing with sample data. The team validates that new content will work, materially lowering risk when the SOC cuts over to Sentinel. Moreover, modern telemetry pipelines like Cribl Stream accelerate every aspect of collecting and managing data, so less time is spent on collection and more time on deriving value.
The eight steps of a SIEM migration
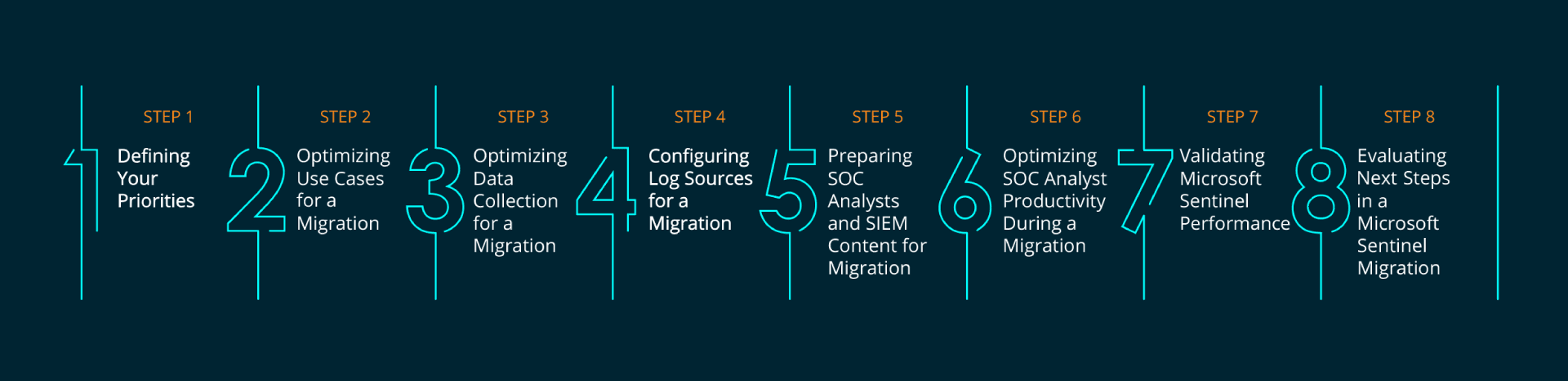
Step 1 - Defining your priorities
Setting clear priorities for Microsoft Sentinel is crucial for a successful migration. These priorities define success criteria and guide the migration strategy. As you may know, there are some important steps to
address before you set your strategy:
Collaboration and stakeholders: Since Sentinel migration impacts multiple areas of an enterprise, collaboration with all impacted stakeholders is essential to identifying critical data, systems, and security assets — such as intellectual property, customer records, financial data, personnel files, and network infrastructure. Recognizing the organization’s “risk assets” ensures protection against significant business risks.
Risk and compliance: Align Sentinel priorities with your risk management frameworks and regulatory requirements. Engaging executives early helps integrate business objectives with IT strategy, ensuring compliance and efficiency.
Existing use cases: Understand all the workloads your legacy SIEM supports, and if any non-security teams are involved. You will need to address these workloads to ensure that they are not orphaned post-migration.
Migration strategy
Define your migration approach. Will it be phased, modular, or a complete replacement? Some organizations enhance legacy SIEMs with new capabilities like behavioral analytics or automation, while others prefer a gradual transition. When planning decommissioning timelines, consider factors like legacy SIEM license renewals.
The best practice is a phased migration enabled by placing a telemetry pipeline, like Cribl Stream, between your sources and destinations. This will establish a common data plane that will give your Security Engineering team complete control over your data. Full data flow is maintained to your legacy SIEM with no changes. A second copy of your data is cloned to Sentinel, optimized and formatted in the required schemas. This pattern enables a phased cutover and thorough testing of your content as it is rebuilt on Sentinel, while maintaining your security posture in your legacy SIEM. A telemetry pipeline also enables data to be shared outside of Sentinel to support non-security workloads, so these teams are not sidelined by the migration.
Migration strategy timeline
Identifying stakeholders and aligning on priorities typically takes four to six weeks. This phase includes determining workloads and establishing change controls to effectively manage upcoming transitions.
Step 2 - Optimizing use cases for a migration
Legacy SIEMs might support dozens or even hundreds of use cases, but not all need replication in Microsoft Sentinel. Sentinel can enhance efficiency by reducing reliance on complex correlation rules and by enhancing automation. When deciding which use cases to carry over, prioritize those that align with the business’s security objectives and address key threats. Do not carry over the technical debt of your legacy SIEM to Sentinel.
Selecting use cases
Prioritize use cases based on business impact, event frequency, and potential consequences. Ignoring business relevance can lead to ineffective outcomes. Common use cases — those you are likely already foregrounding — include insider threats, compromised credentials, account activity, high-risk employee monitoring, endpoint analytics, and alert prioritization. In Sentinel, you can address these priorities by using built-in analytics rules, Microsoft Threat Intelligence, and connectors to Microsoft 365 Defender, Azure resources, and third-party data sources. Framing these within broader risk management initiatives — such as threat detection, process control, and asset protection — can engage executives who might not be familiar with technical specifics. The MITRE ATT&CK® framework is a valuable resource and reference point for mapping adversary tactics and techniques.
Strategic implementation
Technical teams can maximize their impact by focusing on protecting critical business functions and sensitive data, rather than replicating every previous use case. A phased approach starts with high-priority use cases, integrating others over time as the team gains experience with Sentinel. Giving engineering time to master Sentinel is critical to the migration process.
Evaluating how Sentinel supports each use case ensures a smoother transition. Remember that this work can be done in isolation from your existing data stream, maintaining your security posture. A telemetry pipeline can clone your production data to Sentinel, allowing engineering to fully test it for functionality, optimization, and scalability. Meanwhile, your current SIEM continues to receive and process the same full production data stream.
Use case timeline
Depending on alignment with business and security needs, selecting relevant use cases typically takes two to four weeks. While security teams generally understand existing use cases, this period is crucial for assessing new capabilities that the legacy system may not have addressed. Please note that this evaluation can proceed in parallel with Step 3: Optimizing data collection.
Step 3 - Optimizing data collection for a migration
Optimizing data collection requires addressing and correlating data from multiple sources, including:
Infrastructure
Servers, network devices, firewalls, endpoints, operating systemsApplications
Databases, directory services, cloud environments (public, private, hybrid)Contextual Sources
HR systems, configuration management databasesSecurity tooling
EDR, WAF, CNAPP, XEM (converged endpoint management), DLP
Phase A: Assess and integrate log data
Start by evaluating your current log access, aligning available data with key Microsoft Sentinel use cases:
Insider threats: Logs from DLP, email management, database activity, PAM, IAM
Compromised credentials: Logs from authentication, IAM, CASB (cloud access security broker)
Account creation and management: Logs from PAM, IAM
Endpoint anomalies: Logs from EDR, MDM, endpoint monitoring
Security alerts: Logs from firewalls, cloud infrastructure, malware scanning, sandboxing, threat intelligence, VPNs, physical access systems
While some logs might contain overlapping data, a telemetry pipeline like Cribl Stream can handle data quality, so Sentinel is not flooded with confusing or duplicate data. This approach will lead to better outcomes and cost savings. Evaluating how Sentinel supports each use case ensures a smoother transition. As mentioned previously, a telemetry pipeline enables you to send the same data to both Sentinel and your existing SIEM, for comparison.
Phase B: Engage stakeholders and secure access
Since SOC analysts might not control all forms of machine data or telemetry, collaboration with system owners is essential. Standards and business priorities are vital so that all teams will work with security to accomplish complex assessment tasks with as little friction as possible. Ideally, priorities will be supported by a mandate from leadership.
Phase C: Optimize storage and retention with data tiering
A telemetry pipeline enables engineering teams to align data costs with value by tiering data where it makes the most sense. High-frequency, critical data needed for detections flows to Sentinel for analysis. Less-frequently accessed bulk data is routed to tiered storage in a data lake, cost-effectively meeting retention requirements. The telemetry pipeline enables engineering teams to retrieve data from the data lake back into Sentinel as needed.
Microsoft’s announcement of Sentinel Data Lake affirms the importance of smart data tiering in a modern telemetry management strategy. Microsoft’s latest innovations hammer home why our migration framework includes a tiered-storage step so that organizations can benefit from rapid analytics, long-term retention, and cost-effective operations all at once.
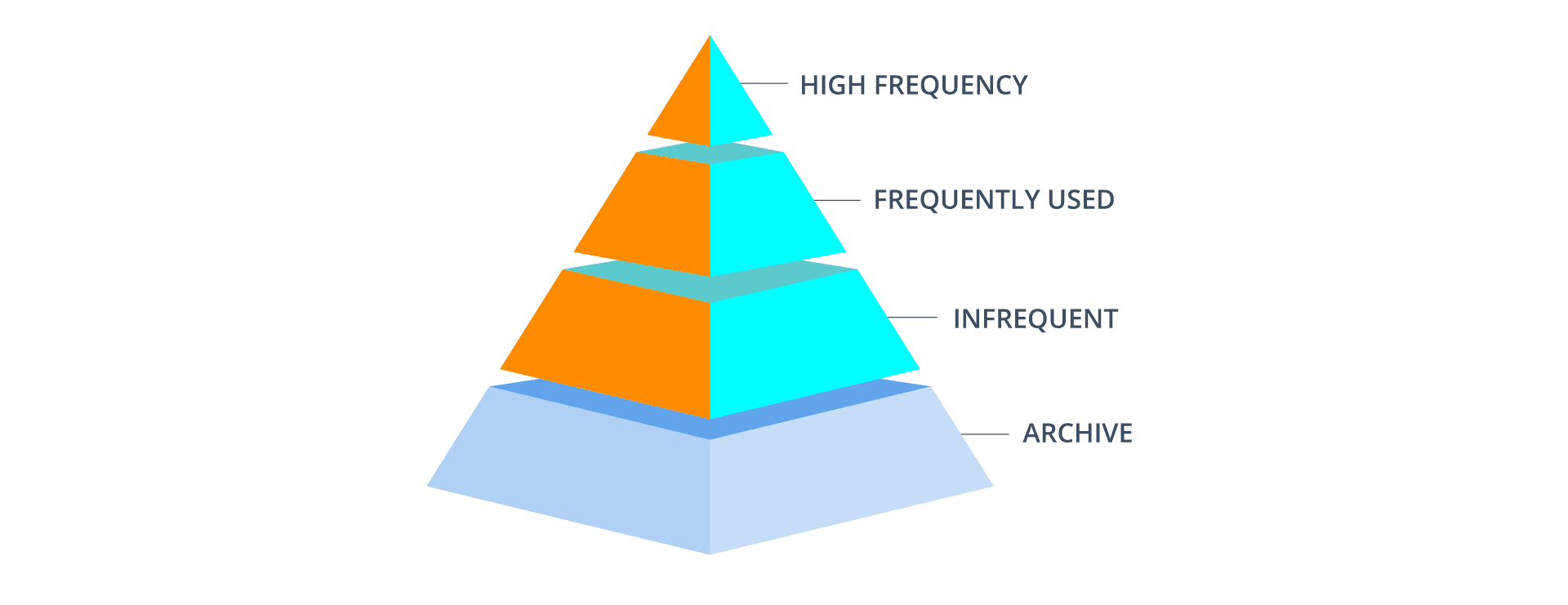
Phase D: Data collection agents
A key question often forgotten is which agent will collect endpoint data. It’s a nuanced question worth some thought. Usually, the legacy SIEM comes with an agent, but that agent won’t let you send data to Microsoft Sentinel. This is where a modern telemetry pipeline gives teams both choice and control over their data.
A vendor-agnostic telemetry pipeline like Cribl Stream can work with the agent you have in place, sending data to both your legacy SIEM and Sentinel simultaneously. Point the legacy agent at Stream and fork the data to Sentinel with minimal complexity, accelerating your migration. An issue to keep in mind is that SIEM decommissioning might require removing the agent. Check your license agreement — you do not want to be forced to pay a settlement because of an oversight.
To accommodate or replace agents on upstream systems, your team has several options.
Cribl Stream supports almost every available data collection agent. Stream also supports an agentless architecture, enabling direct data ingestion from sources like syslog senders and Windows Event Collectors.
As an alternative, Cribl offers its own agent, called Cribl Edge. Edge is a flexible endpoint telemetry agent that is easy to use and provides a robust user experience. It enables admins to configure essentials like log and metrics collection and to install pipelines that manage data at the source. Teams love to explore and build on Edge’s flexibility. One last piece of advice: Consider staging the agent replacement after implementing Cribl Stream (with or without Edge). Teams that try to replace agents and implement Cribl at the same time often get bogged down in too much complexity. Make one change at a time to manage the rate of change.
Data collection timeline
Mapping log sources to use cases typically takes four to eight weeks, depending on:
Availability of pre-built integrations
Changes in use cases during migration
Updates to other security tools as part of broader security transformation
Keeping your existing agent or replace it
This assessment can also be carried out in tandem with Step 2: Optimizing Use Cases. A well-planned data collection strategy ensures a smooth Microsoft Sentinel migration, enhancing threat visibility and security operations
Step 4 - Configuring log sources for a migration
Log source configuration is a critical and often time-consuming aspect of a Microsoft Sentinel migration. This involves carefully routing and optimizing the various data sources that feed your current SIEM to ensure that Sentinel receives all the necessary data in the correct format for effective threat detection and analysis. Careful planning and collaboration help streamline this process, ensuring seamless data integration and reliable security monitoring while getting Sentinel ready for cutover.
Let’s dive into the specific steps for ingesting security-relevant log sources into a telemetry pipeline:
Phase A: Onboard required data sources
Ensure that relevant telemetry is properly integrated into the pipeline. Cribl Stream supports many common data sources out of the box and offers extensive flexibility for integrating custom sources.
Infrastructure may need to expand to support log ingestion at scale.
This process can sometimes be complex, so having a dedicated team helps maintain focus and consistency.
Phase B: Apply parsers
Log parsing is essential for accurate threat detection and requires field-specific parsers to interpret log data. This ensures data is properly aligned with and optimized for Sentinel.
Logs often have inconsistent or unclear naming conventions, making parser development a challenge.
Cribl Stream provides built-in parsers for common data sources and allows teams to easily adapt or create custom parsers as needed. Its intuitive interface helps engineering teams normalize data more quickly.
Phase C: Clone and synchronize Log Data
Clone telemetry data to Sentinel, coordinating with storage, backup, IT operations, and compliance teams.
Validate that all data is in scope and is optimized for Sentinel. Engage Microsoft partner support, as needed, to validate that data is being parsed as expected.
Ensure that a tiered data storage strategy is implemented, and that no extraneous data is forwarded to Sentinel.
Phase D: Replace telemetry agents
Roll out new agents in stages, using Cribl Stream as the destination.
Minimize change by keeping collection patterns and formats as close as possible to a one-for-one replacement.
Validate formats and adjust Stream configs as required.
Remove each old agent and enable its replacement.
Validate Sentinel content and test detections.
Log configuration timeline
Configuring log sources is one of the most time-intensive aspects of SIEM migration, typically taking two weeks to six months. The duration depends on:
The number of log sources and their complexity.
Coordination with IT and security teams across multiple locations.
Setting up local collectors for geographically distributed environments.
Replacing existing telemetry agents.
Teams can work on configuring log sources in parallel with Step 5: Preparing analysts and content.
Step 5 - Preparing SOC analysts and SIEM content for migration
Your SOC analysts must familiarize themselves with Microsoft Sentinel’s capabilities. For example, Sentinel can:
Prioritize critical security events that require investigation.
Correlate low-fidelity alerts from multiple sources into high-fidelity security incidents, reducing alert fatigue and false positives.
With integrated Microsoft Security Copilot, translate natural-language queries, investigate incidents, summarize alerts, and recommend incident responses.
Integrate with Microsoft 365 Defender and other Microsoft products for coordinated threat visibility across endpoints, identities, emails, and applications.
Faster, realistic training
Analyst training is essential when transitioning from a legacy rule-based alert system to one leveraging behavioral analytics, AI, and machine learning. To take full advantage of Sentinel’s expanded capabilities, teams should practice with realistic data and processes. Cloning your production dataset through a telemetry pipeline, such as Cribl Stream, supports this by enabling more effective training and validation. Allocating time to learn the pipeline’s features will further enhance readiness, but the core investment in training ensures a successful Sentinel migration without compromising security posture.
Configuring Microsoft Sentinel content
To ensure effective migration, the SIEM content must support selected use cases, including:
Dashboards and reports: Customizable for visibility into security trends and compliance
Correlation rules and anomaly detection: Aligning automated threat detection with security objectives
Case management and alerts: Ensuring timely and relevant notifications
Compliance considerations
Your GRC team must confirm that your Sentinel configuration meets your industry-specific compliance requirements. Risk managers should define these criteria and dashboards should be sortable by compliance categories to streamline audits.
Content preparation timeline
Configuring Sentinel content typically takes four to ten weeks depending on the complexity of the use cases. This work can be done in parallel with Step 4: Configuring Log Sources.

Customer Success
Yale New Haven Health, Connecticut’s largest healthcare system, faced soaring SIEM costs after a firewall update unexpectedly inflated log volumes with dozens of unnecessary fields. To regain control, the team adopted Cribl Stream to strip out noise and reduce ingest by 40%. This immediately brought their usage back in line. Even so, escalating licensing costs drove a full migration to Microsoft Sentinel, with cutover performed in just 2 weeks. With Sentinel in place and Cribl powering data normalization and routing, Yale New Haven centralized collection from more than 30,000 endpoints, onboarded diverse log sources, and gained a more scalable, flexible foundation for its security infrastructure.
Cribl Stream made it easy to strip the extra fields out and get those logs right back under control. We didn’t lose any log fidelity or important data — we just took out some of the garbage.
— Yale New Haven Health
Step 6 - Optimizing SOC analyst productivity during a migration
Transitioning to Microsoft Sentinel requires adjusting productivity expectations for SOC analysts. This includes training on the new toolset (addressed in Step 5: Preparing SOC Analysts and SIEM Content for Migration), refining workflows, and updating operational playbooks to align with Sentinel’s expanded capabilities.
Boosting productivity with faster search and automation
Legacy SIEMs often take hours to return search results, while Microsoft Sentinel can deliver results in minutes. With automated response playbooks, real-time threat timelines, and integrated AI, analysts can focus on high-priority security incidents instead of manual investigations.
Adapting to new operational processes
Migrating to Sentinel introduces changes in daily SOC workflows, leading to common questions such as:
Will analysts need to learn a new query language?
Sentinel offers intuitive point-and-click interfaces, reducing reliance on command-line queries. Sentinel uses Kusto Query Language (KQL) and natural-language queries for searching and analytics, consistent with KQL support across other Microsoft security and compliance tools. Many teams find the transition easier than expected because of KQL’s structured syntax and strong documentation. Sentinel also supports Jupyter notebooks for exploration, threat hunting, and analysis.How does Sentinel’s alerting system compare to the old SIEM?
Sentinel reduces false alarms, allowing analysts to focus on genuine threats rather than unnecessary alerts.
Enhancing analyst capabilities
Microsoft Sentinel is easier to use, enabling Tier 1 analysts to handle tasks previously reserved for Tier 2 analysts, such as advanced query writing and rule creation. By minimizing noise and automating repetitive tasks, Sentinel boosts efficiency across all analyst levels, leading to a more proactive security approach.
Refining playbooks and automating response
During migration, the team must review and refine SOC workflows and incident response playbooks. Sentinel supports automating key response actions, including integrations with third-party vendors, ticketing systems, and IT teams. Seizing these automation opportunities can significantly improve Mean Time to Respond (MTTR).
Documenting processes
Comprehensive documentation ensures smooth post-migration operations. While not the most exciting task, documenting new processes for SOC analysts, auditors, and stakeholders is essential for maintaining operational continuity.
Training and process adoption timeline
Basic SIEM training: As little as two weeks
Full adoption of new workflows: Up to four months, depending on how quickly teams adjust to new processes
Migrating to Sentinel improves efficiency, accuracy, and automation, leading to a more agile and effective SOC. You can validate these efficiency improvements through metrics on false-alarm reduction and overall analyst productivity.
Step 7 - Validating Microsoft Sentinel performance
Setting benchmark criteria for Microsoft Sentinel ensures measurable and effective performance evaluation. These benchmarks should align with existing frameworks such as:
ISO (compliance standards)
PCI DSS (payment security)
Operational metrics like search times, Mean Time to Detect (MTTD), and Mean Time to Respond (MTTR)
Measuring performance
By visually representing benchmark criteria in a heat map to score use cases, typically against the MITRE ATT&CK® framework, SOC managers can quickly identify areas of weakness. Early on, these areas may appear in red, highlighting gaps that need improvement. Over time, as teams build skills, telemetry pipelines improve data quality, and ML models adapt, the red areas shift to yellow, reflecting gradual progress. Eventually, as analytics mature and deliver effective security coverage, they turn green, indicating that Sentinel is successfully meeting business objectives.
Testing and tuning
Tuning plays a crucial role in benchmarking. The process includes Red Team attack simulations to test and refine the system. Regular tuning and testing help identify misconfigurations or weaknesses that could affect detection accuracy. Sentinel incorporates self-tuning analytics which optimize performance over time.
Benchmark timeline
Setup: Expect two to four weeks, as this process is fully within the security team’s control
Ongoing review: Evaluate use cases every few months to ensure effectiveness
Attack simulations: Test regularly to refine benchmarks to align with business objectives
If in-house Red Team capabilities are unavailable, consider engaging external security experts to conduct attack simulations, or adopt an automated penetration testing and attack simulation platform to maintain a robust security posture.
Step 8 - Validating Microsoft Sentinel performance
The final phase of a Microsoft Sentinel migration involves evaluating next steps to ensure continuous security improvements. Unlike legacy SIEMs, which require constant manual adjustments to thresholds and alerts, Sentinel leverages behavioral analytics and machine learning to automate threat detection, reducing the need for manual rule adjustments. This shift allows SOC teams to focus on developing new use cases, as business and security priorities evolve, as long as data quality is high and represents the environment.
Data quality makes these advanced processes work so it is crucial to leverage a telemetry pipeline, like Cribl Stream, to monitor data drift and quality and take immediate action if an issue occurs. This has to be a proactive, continuous process to prevent a degraded security posture.
Microsoft Sentinel management as an ongoing process
A Microsoft Sentinel migration should not be viewed as a one-time project, but rather as an ongoing process to maintain your security posture. Well-protected organizations continuously review and refine processes, ensuring that Sentinel adapts to emerging threats and business needs. Governance is important and cannot be forgotten.
Ongoing process: To continuously evaluate next steps, your organization’s level and breadth of involvement can vary based on changing security landscapes.
Post-migration improvements: Regularly assess opportunities for process enhancement, ensuring that Sentinel remains effective against evolving threats.
Organizations should view initiating a Sentinel migration project as a way to jumpstart a broader security data strategy. This approach will prevent past mistakes from happening again, allowing your organization to maintain optimal security operations and improve your overall cybersecurity investment. Effective cybersecurity starts and ends with your data, and data quality must be the focus of your program to ensure long-term success.
After: Driving security outcomes through better data
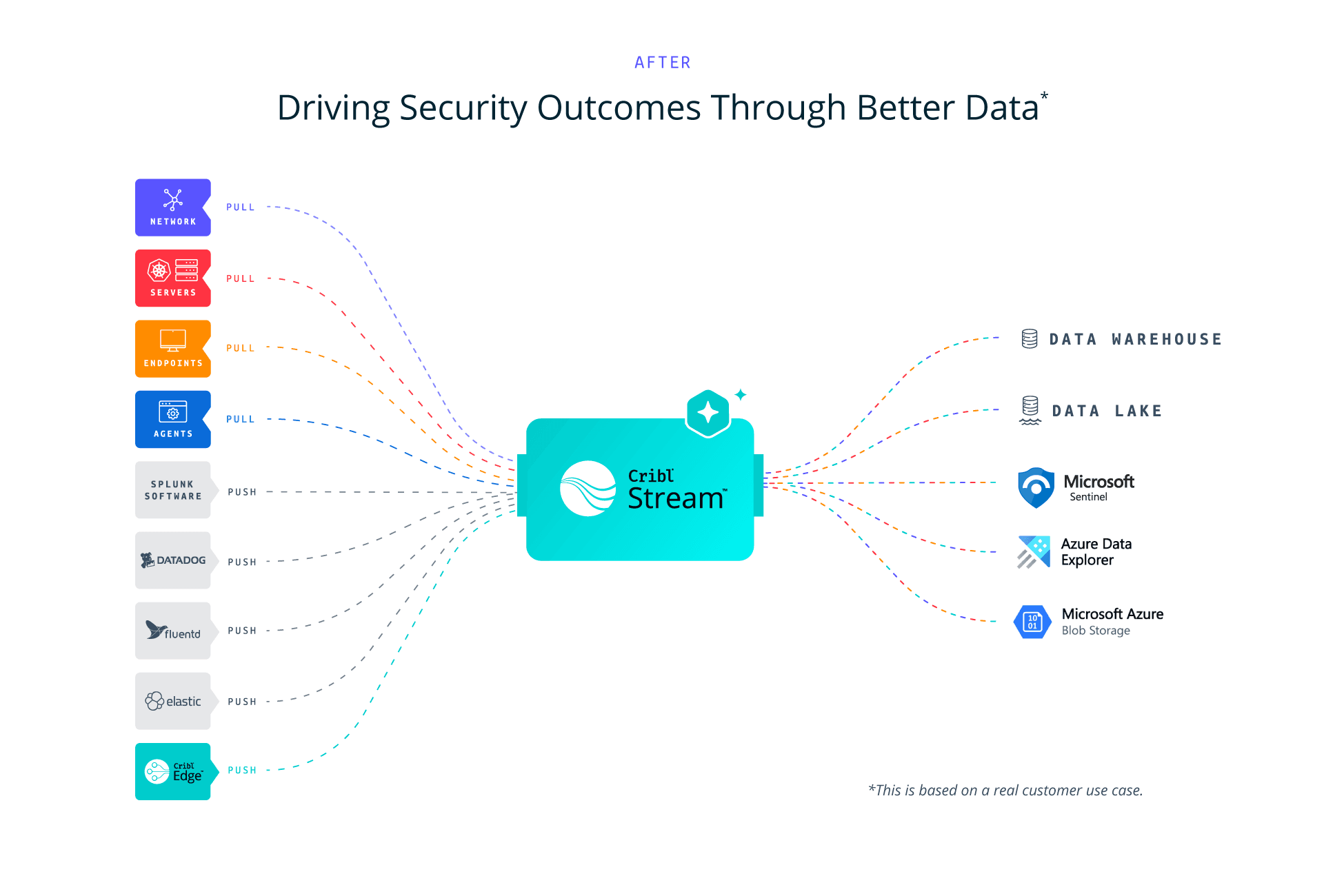
Conclusion
Migrating from a legacy SIEM is a significant decision that can potentially impact the entire enterprise. Instead of viewing a Microsoft Sentinel migration as just a technology shift, organizations should see a migration as an opportunity to unlock new efficiencies, enhance security, and streamline operations. The migration process offers tangible benefits including improved threat detection, increased automation, and better alignment with evolving business needs. It also positions the organization to avoid the pitfalls of the past by using a telemetry pipeline to optimize costs and derive more value from the organization’s data.
Better results begin with better data, which is why every organization should consider developing a security data strategy as part of a Microsoft Sentinel migration. Seize this opportunity to address your technical debt and set your team up for future success by using a telemetry pipeline like Cribl Stream. This will help ensure that your teams collect the right data, in the proper formats, allowing them to extract maximum value from Sentinel. This will also enable your teams to enhance data portability and realize substantial savings by tiering low-value data to low-cost storage. With a telemetry pipeline implemented, your teams will be able to onboard new data significantly faster and share information seamlessly across the enterprise.
The steps outlined above offer a framework for a successful migration, addressing the critical components of people, processes, and technology. A well-structured plan, combined with industry best practices — such as comprehensive documentation and a post-migration “lessons learned” review — ensures a smooth transition and long-term success.
Beyond technical implementation, your migration significantly impacts SOC teams and other key stakeholders whose daily workflows will evolve with Microsoft Sentinel’s expanded capabilities. By adopting Sentinel, organizations can strengthen security, ensure regulatory compliance, and boost SOC productivity, fostering a more proactive and stronger security environment.
Resources

Learn more about how Cribl and Microsoft Sentinel work together:
DOCS
BLOGS
RESOURCES
Cribl Signs Agreement with Microsoft to Streamline Data Management (Announcement)
Cribl Stream How-To: Configuring a Microsoft Sentinel Destination (Cribl University)
To get started with Microsoft Sentinel and Cribl, visit Azure Marketplace for a free trial today! The Cribl Slack Community is also a great place to connect with leaders from other teams leveraging both Microsoft Sentinel and Cribl.