Windows events provide a wealth of security-relevant information, especially when they are correlated and analyzed within a SIEM like IBM QRadar. Whether you rely on MITRE ATT&CK, NIST, or another security framework, Windows Events are likely one of your higher volumes (EPS – Events Per Second) and represent your largest-sized events (Gigs per day – Storage and Archive).
Maintaining a healthy security practice requires all events are available for Offences/Alerts Correlation, Threat Detection, and Threat Hunting. While Windows Events are undeniably valuable to security analysts and tools, they pose unique challenges for security teams to successfully manage Collection and Control volume while managing budgets, resources, and time.
🪣How to Collect Windows Events
There are many ways to collect Windows Events for QRadar. Popular methods include agents like WinCollect (IBM’s Agent), and Windows Event Collection/Forwarding (WEC/WEF), which is a feature built into Microsoft. Each method offers unique administrative challenges and tradeoffs and must be carefully evaluated.
Cribl Stream can integrate with your collection mechanism and sometimes displace Syslog deployments and Windows Event Collection/Forwarwarders (WEC/WEF).
🎯How to Control Which Events Are Collected

Windows Events are broken down into EvenetIDs and Subtypes. Thankfully, each event is well documented, and resources like ultimatewindowssecurity.com can provide insight into a given event’s value to a security team.
Not all EventIDs drive value for Security, yet they are frequently sent to the SIEM, driving up costs and consuming valuable Events Per Second (EPS) resources. Worst yet, some events may be sent to the SIEM to satisfy another team’s needs for compliance purposes only.
🤣 “That’s an expensive Archive you GOAT there!” ~ Cribl GOAT

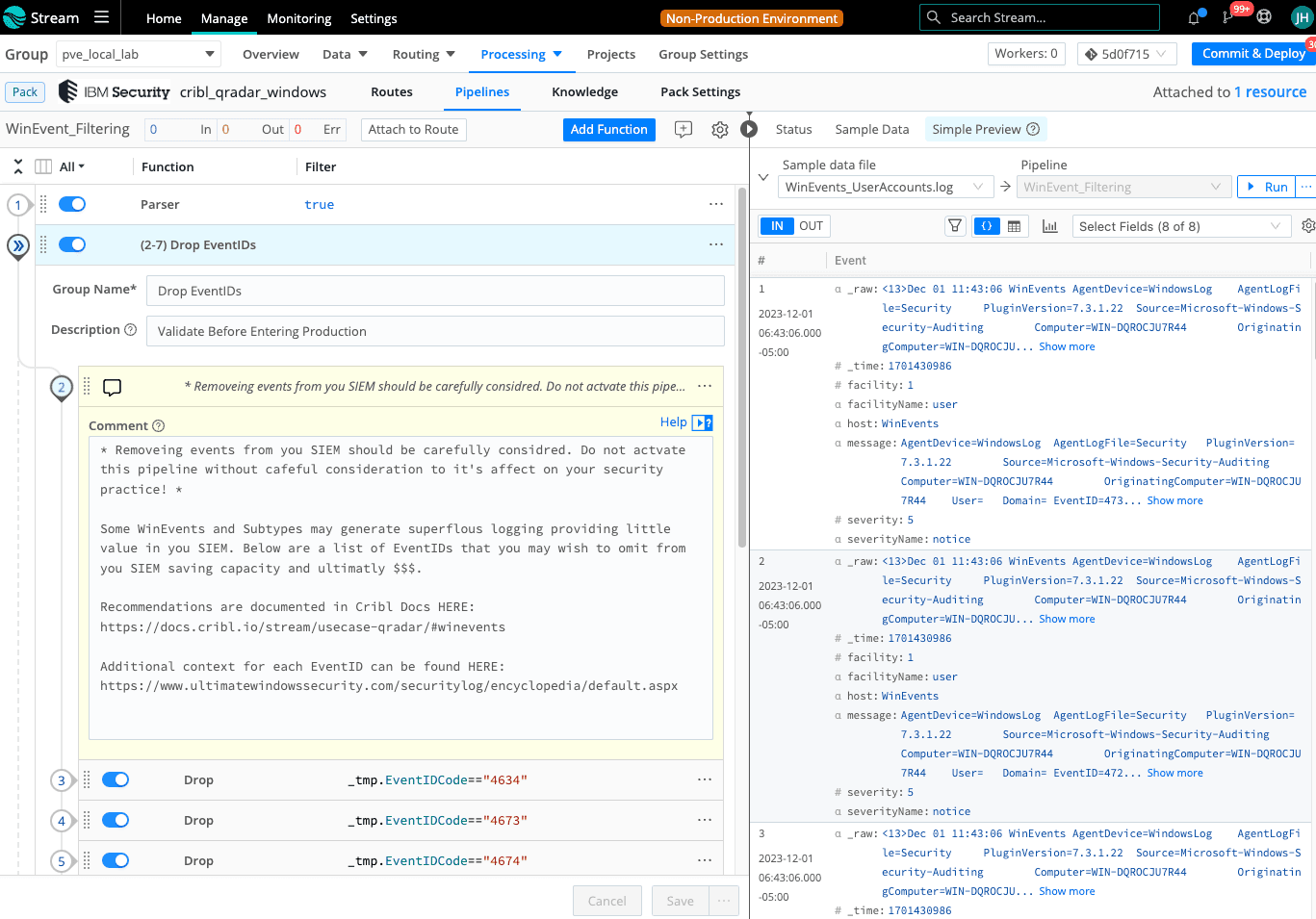
Cribl Stream enables administrators to selectively control the routing, suppression, and dropping of events before they reach QRadar. This allows teams to satisfy the needs of their security practice while routing nonsecurity events to another destination.
Let’s Put Cribl Stream to Work!
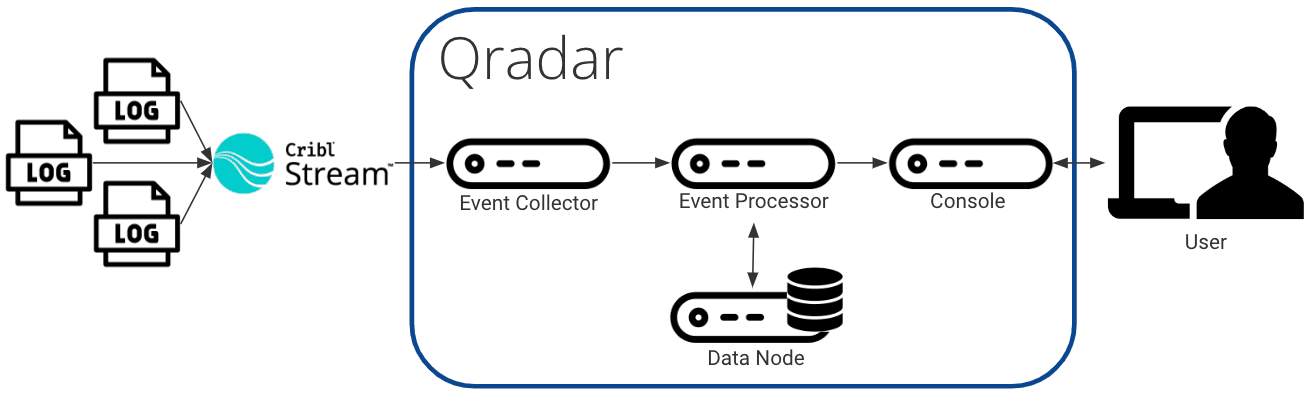
Microsoft Windows Security Events are natively supported by QRadar using the included DSM (Devise Support Module). This means parsing events and mapping them to threat models within QRadar are ready to go out of the box! We will use this to our advantage 😎.
For the guide below, we will use IBM’s WinCollect Agent to collect Windows events, and forward them to Cribl Stream to be sent to QRadar. Because Cribl Stream is in the middle, events can be evaluated, transformed, and routed selectively. We’ll also use the “QRadar Pack for Windows” to drop and suppress events that typically drive very little value for a security team.
NOTE: Carefully review which events you are dropping before deploying to production!
Getting Started
Set up your FREE Cribl.Cloud account. Click here
Download the “QRadar Pack for Windows”
Configure your Windows Event Source (WinCollect) and QRadar Destination
🧙Witness the Magic 🪄
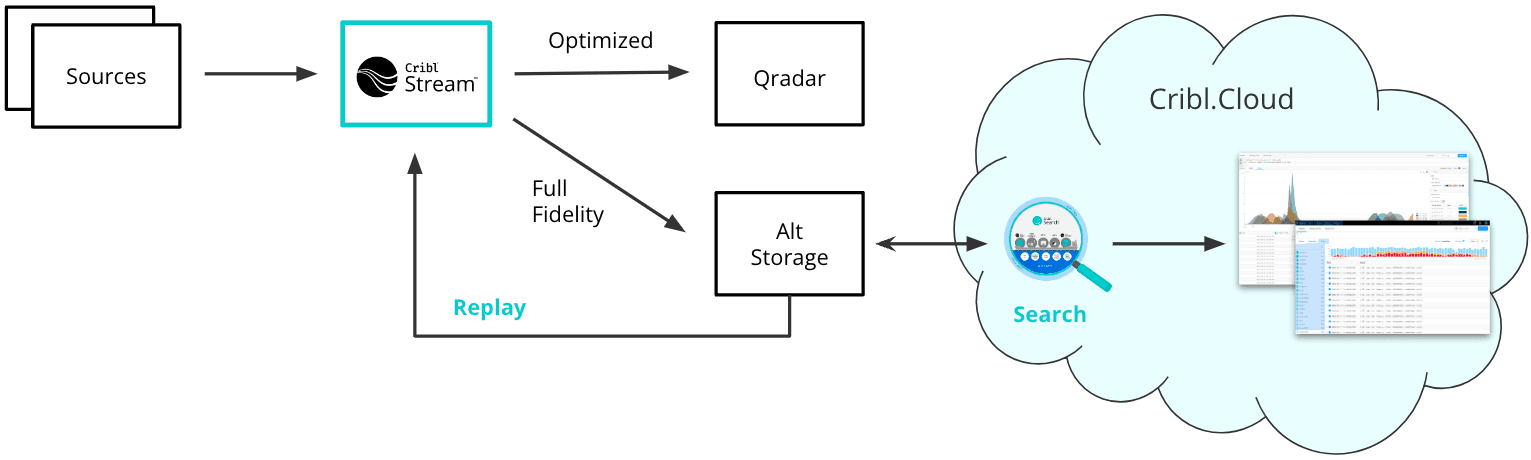
Architecture
Cribl Configuration
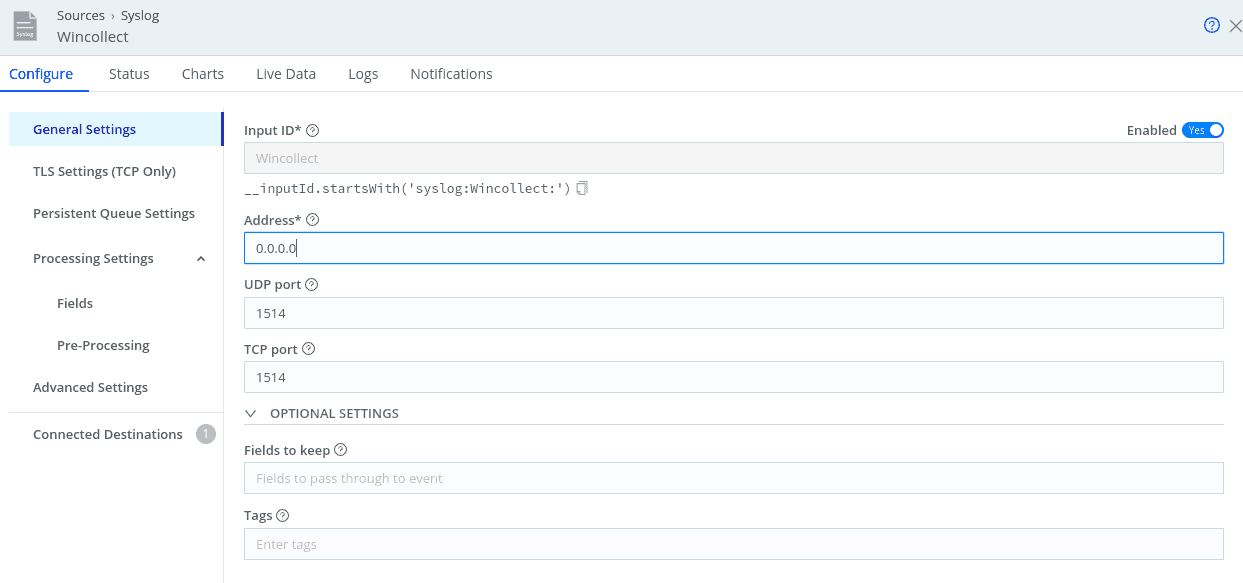
Setting up your WinEvent Source in Cribl Stream
Configure a Syslog Source and name it WinCollect
Be sure to use the correct port for your environment. In my lab, I’m using port 1514
Click SAVE.
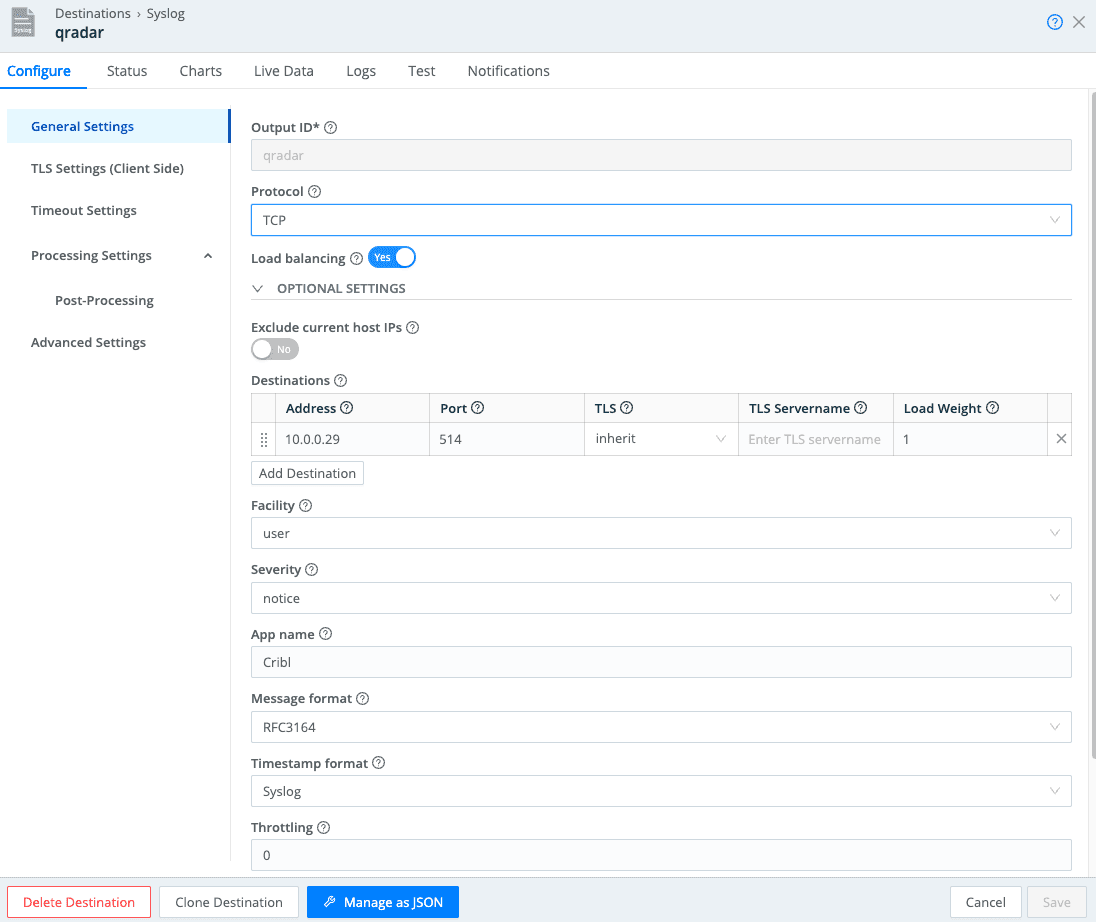
Setting up your QRadar Destination in Cribl Stream
Configure a Syslog Destination and name it QRadar
Use the proper IP address and port for your Event Collector. I’m using 10.0.0.29 and port 514.
Click SAVE
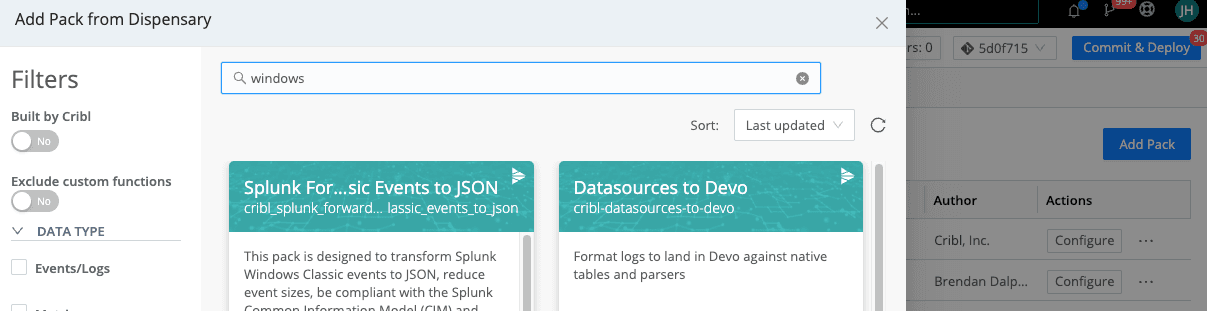
Add the QRadar Pack for Windows
Navigate to Processing > Packs > Add Pack
Search for Windows
Download the “QRadar Pack for Windows”
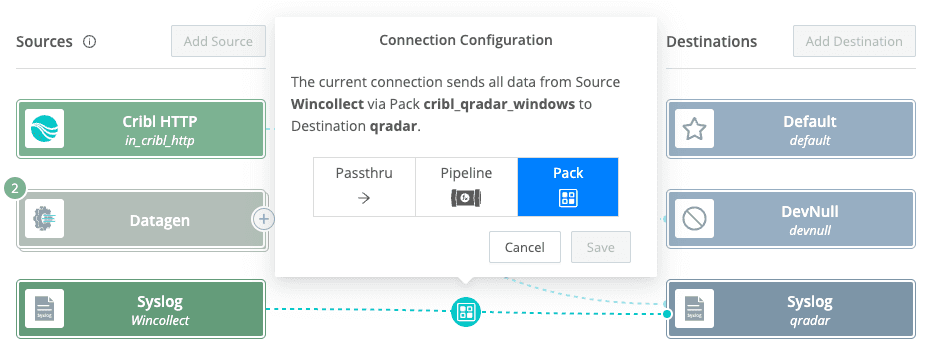
Connect Your Source and Destination
Navigate to Data > Quick Connect
Click Add Source (select your WinCollect Syslog source)
Click Add Destination (select your QRadar Syslog Destination)
Connect your Source and Destination, choose Pack > “QRadar Pack for Windows”
Click Commit and Deploy
✅ Cribl Config Complete!
QRadar Configuration
Configure the WinCollect Agent
NOTE: I’m using the Standalone MSI installer for this guide. However, a Managed deployment will utilize a similar configuration.
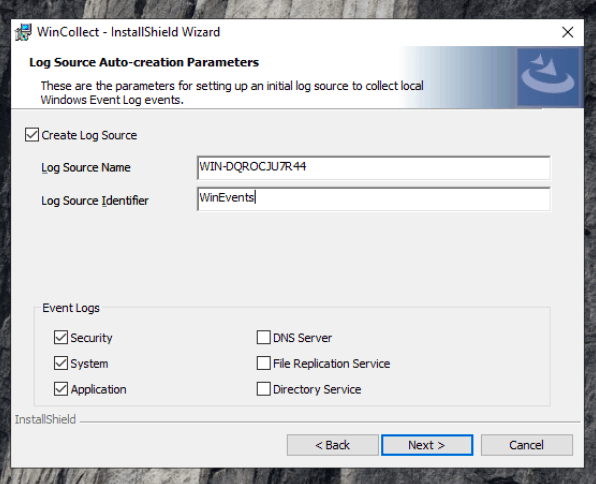
Select Event Logs in Scope (Security, System, and Application)
Click Next
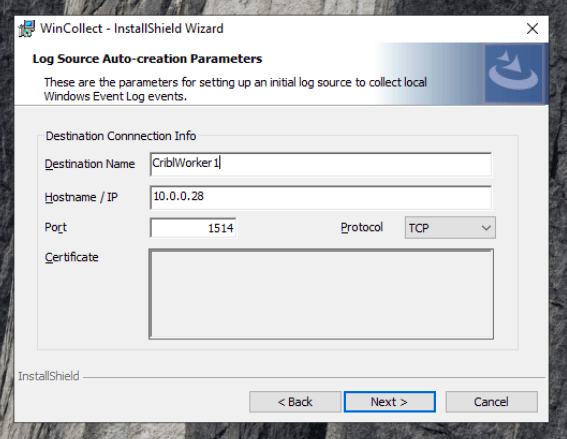
Configure the WinCollect Agent to Route Events to Cribl
Insert the IP address and Port for your Cribl worker, click Next
In my lab, my Cribl worker is 10.0.0.28, and Port 1514
Verify Configuration and Finish Install
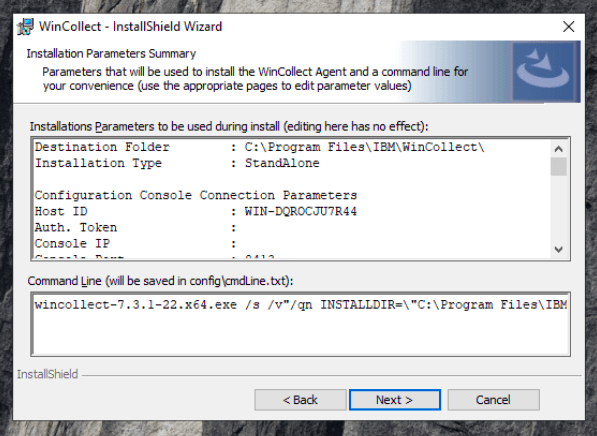
Follow the remaining prompts till you reach “Installation Parameters Summary”
Validate the configuration and Click NEXT to finish the installation.
Let’s Make Sure Everything Is Working!
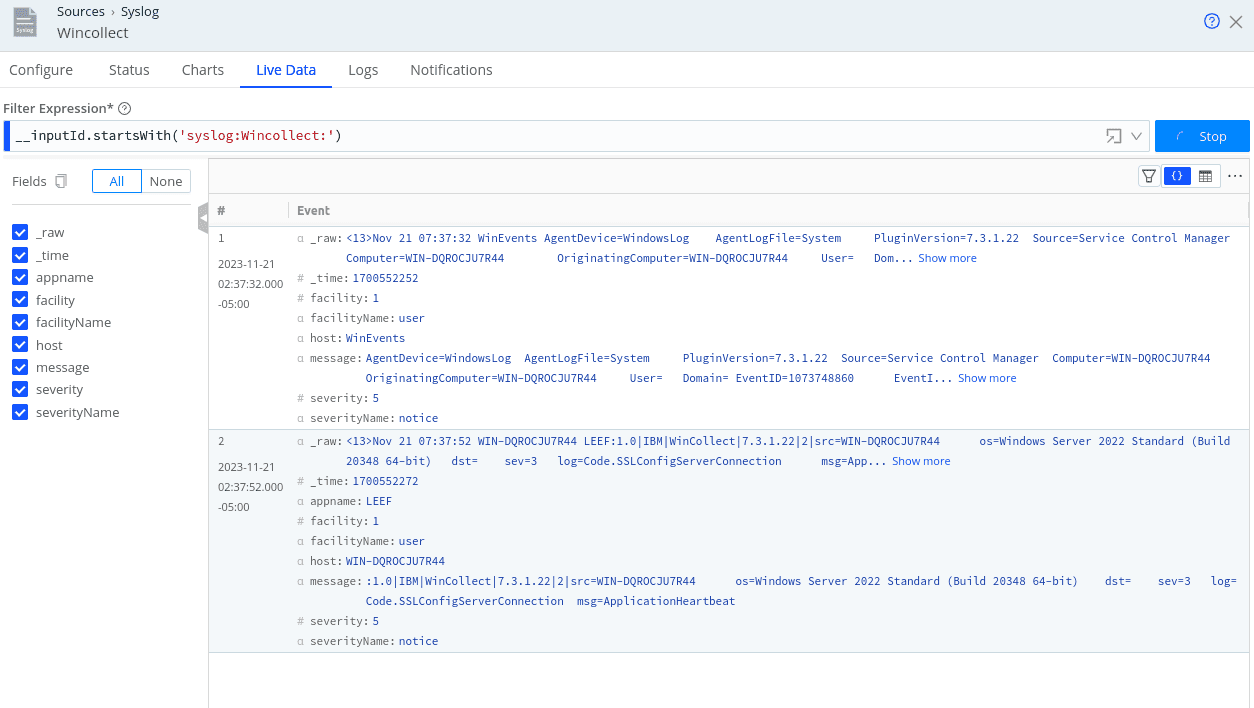
Check Cribl’s Live Capture to ensure events are flowing
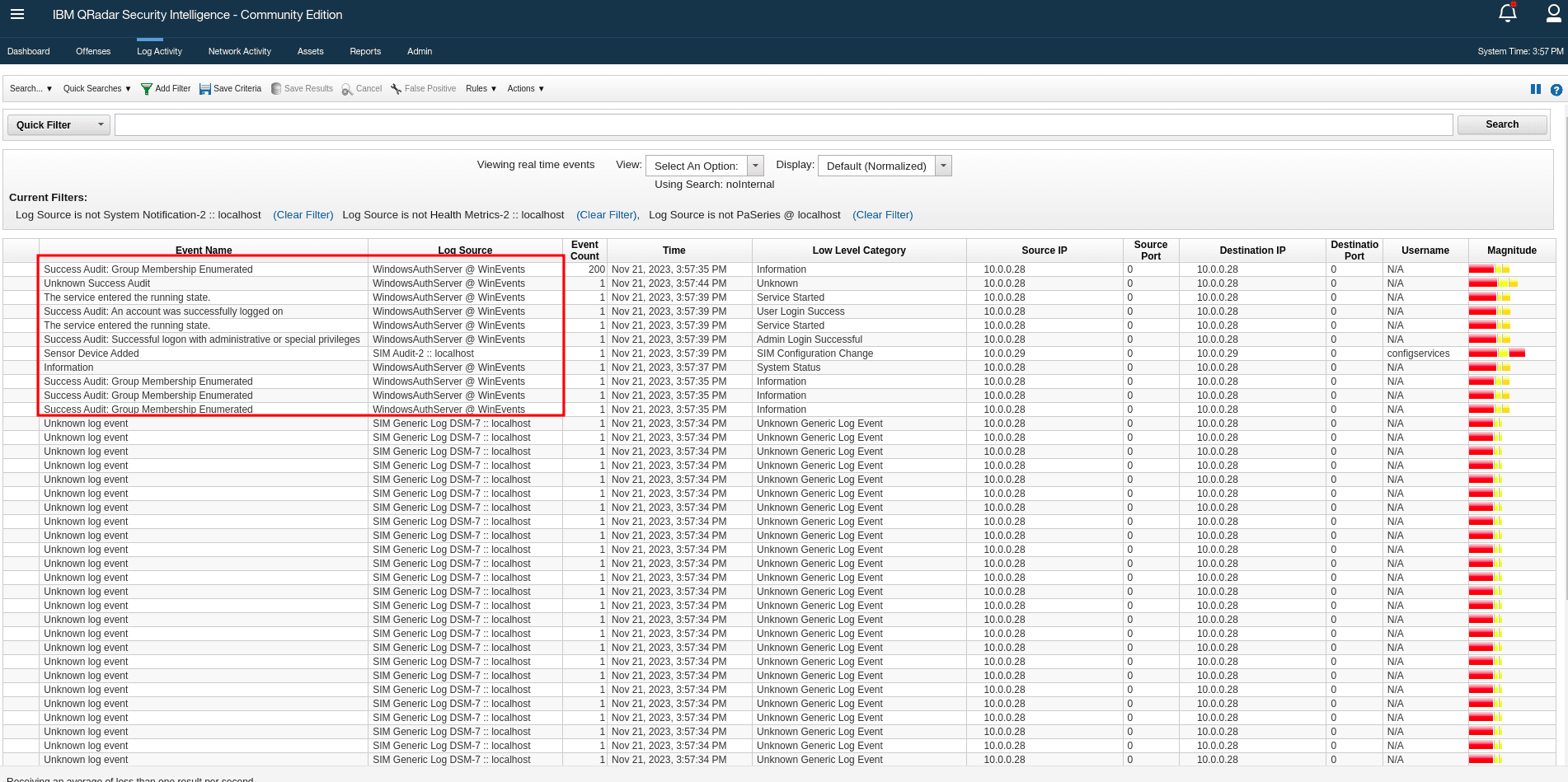
Check QRadar Log Activity to ensure events are received.
Controlling Events
DONE!

Wrapping up our journey through integrating Windows Events into IBM QRadar, with the aid of Crib Streaml, reveals a path to more efficient and effective security management. We’ve looked at how to harness the power of Windows Events, a critical resource in security analysis, and tackled the challenges of managing their volume and relevance. Ready to try it for yourself? Check out Cribl.Cloud, where we’ll give you free access to Cribl Stream to get started.







