Cribl Packs are, in my opinion, our most exciting feature. Packs encapsulate the deep log processing capabilities and enable sharing of the best practices with customers, Worker Groups/Fleets, and the Community. Ease of sharing enables consistent configurations across distributed deployments of Cribl Stream or Cribl Edge. All users can leverage Packs–and should! If you collect Microsoft Windows Logs, use Palo Alto Networks or share logs via Syslog, Packs are for you. New Packs are consistently added to the Cribl Packs Dispensary. We encourage you to share your pack creations as well–there are even some prizes on the line!
You’ll see many community members contribute their creativity to Packs. Creating a Cribl Pack involves four (4) steps:
Create and save the initial Pack.
Build, test, and refine Routes, Pipelines, Knowledge Objects etc.
Export the Pack file
Publish to Cribl Packs Dispensary
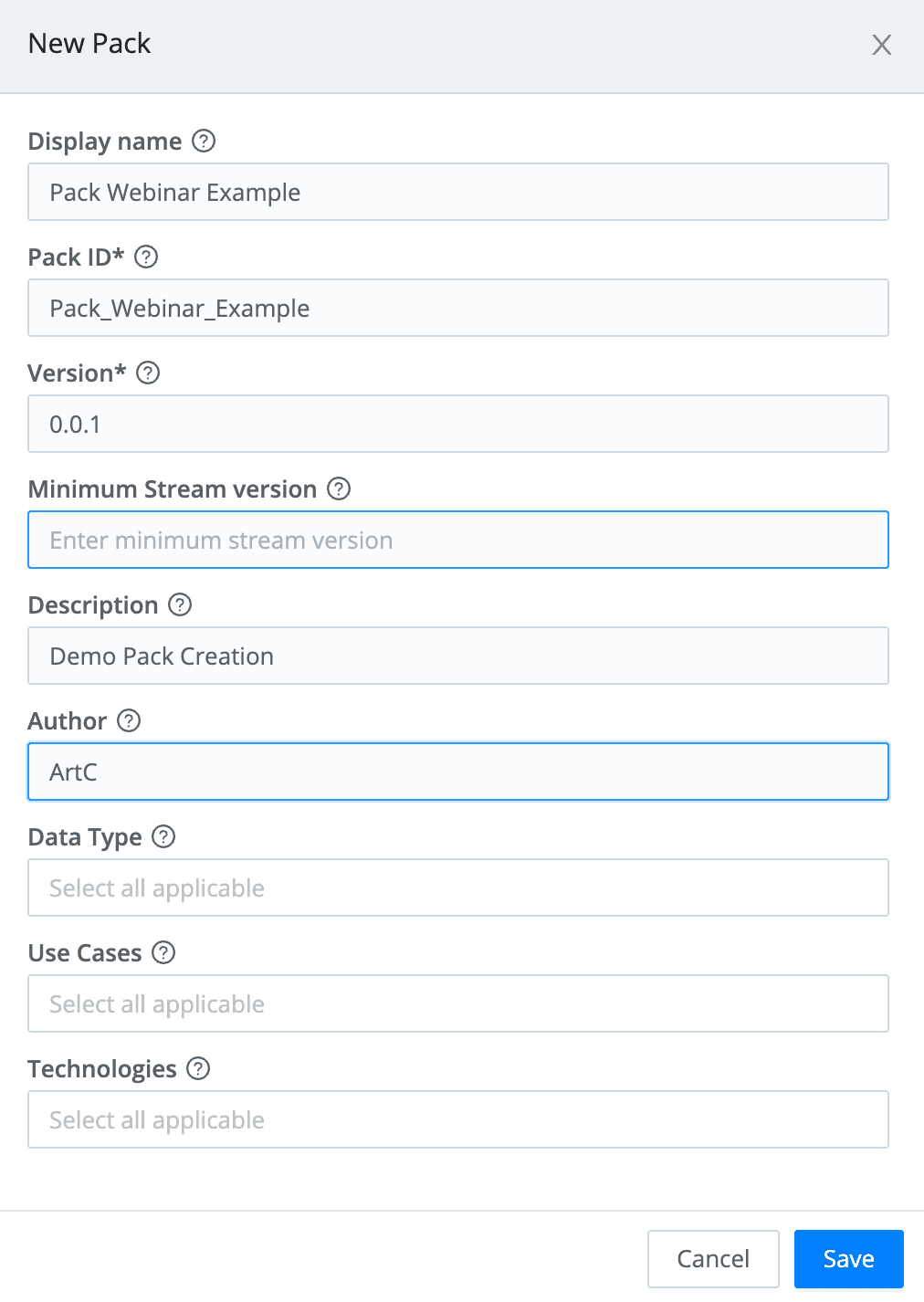
Step 1: Create and Save the Initial Pack
The first step is to create the base Pack structure. The mechanics are detailed in our excellent documentation here. Here’s the example I included in the video.
Now we’re ready to build out the Pack.
Step 2: Build, Test and Refine Routes, Pipelines, Knowledge Objects, etc.
Foundational Pack elements include Routes, Pipelines, and Knowledge Objects. You will invest most of your creativity and craftsmanship in this step. We’ll discuss each of these elements.
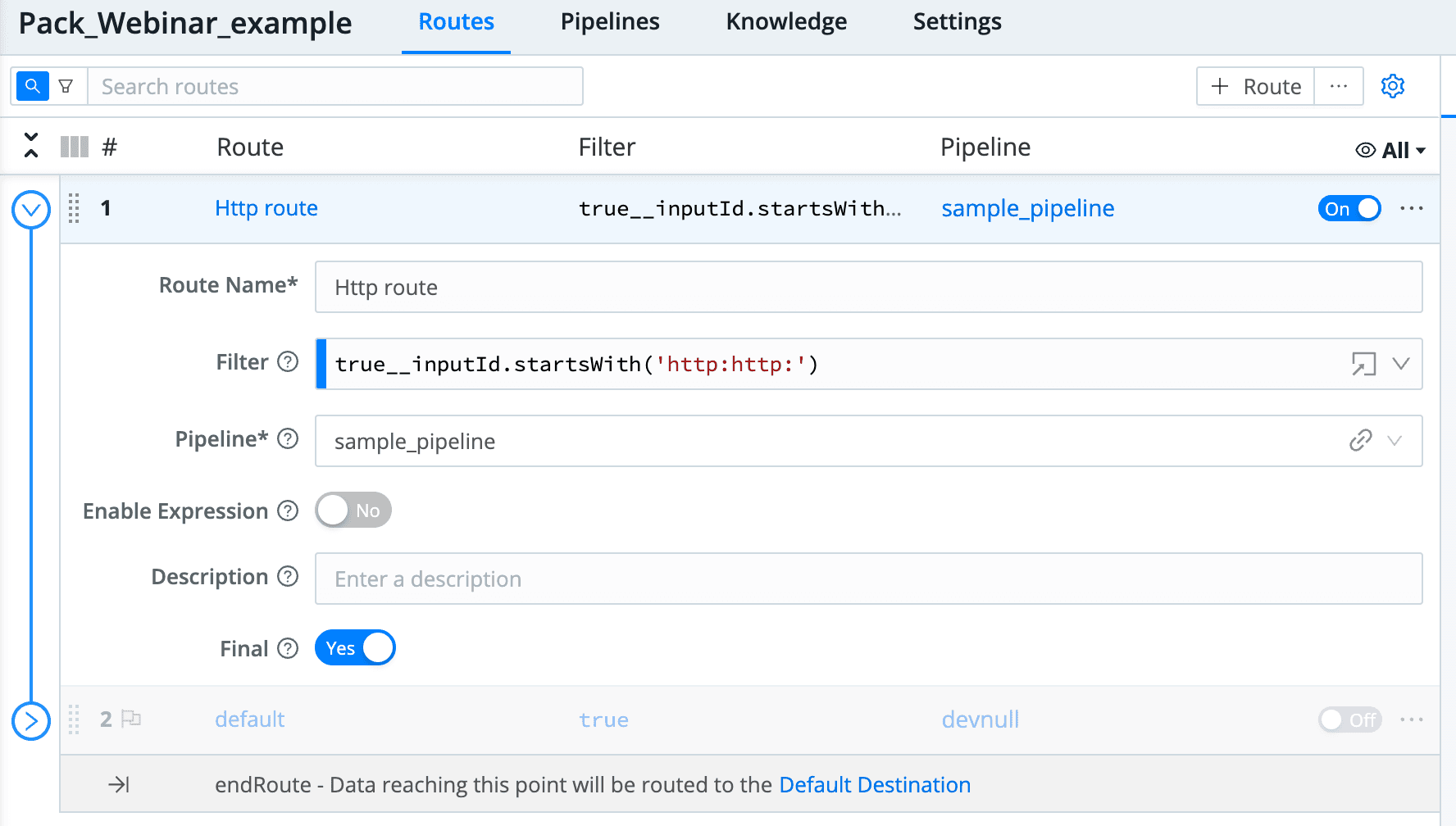
Routes direct specific data types, depending on the applied filter, to a Pipeline. In the screenshot, HTTP traffic is ‘Filter’ed, and routed to the ‘sample_pipeline’. Filters support Javascript expressions (similar to Regular Expressions) and are powerful means of identifying specific data types. Cribl Expression Syntax is detailed in our documentation.
Pipelines are the processing workhorses. This is where the heavy lifting happens. Pipelines are a collection of Functions executed in the top to bottom order. In the video, I explained the Parser and Lookup functions.
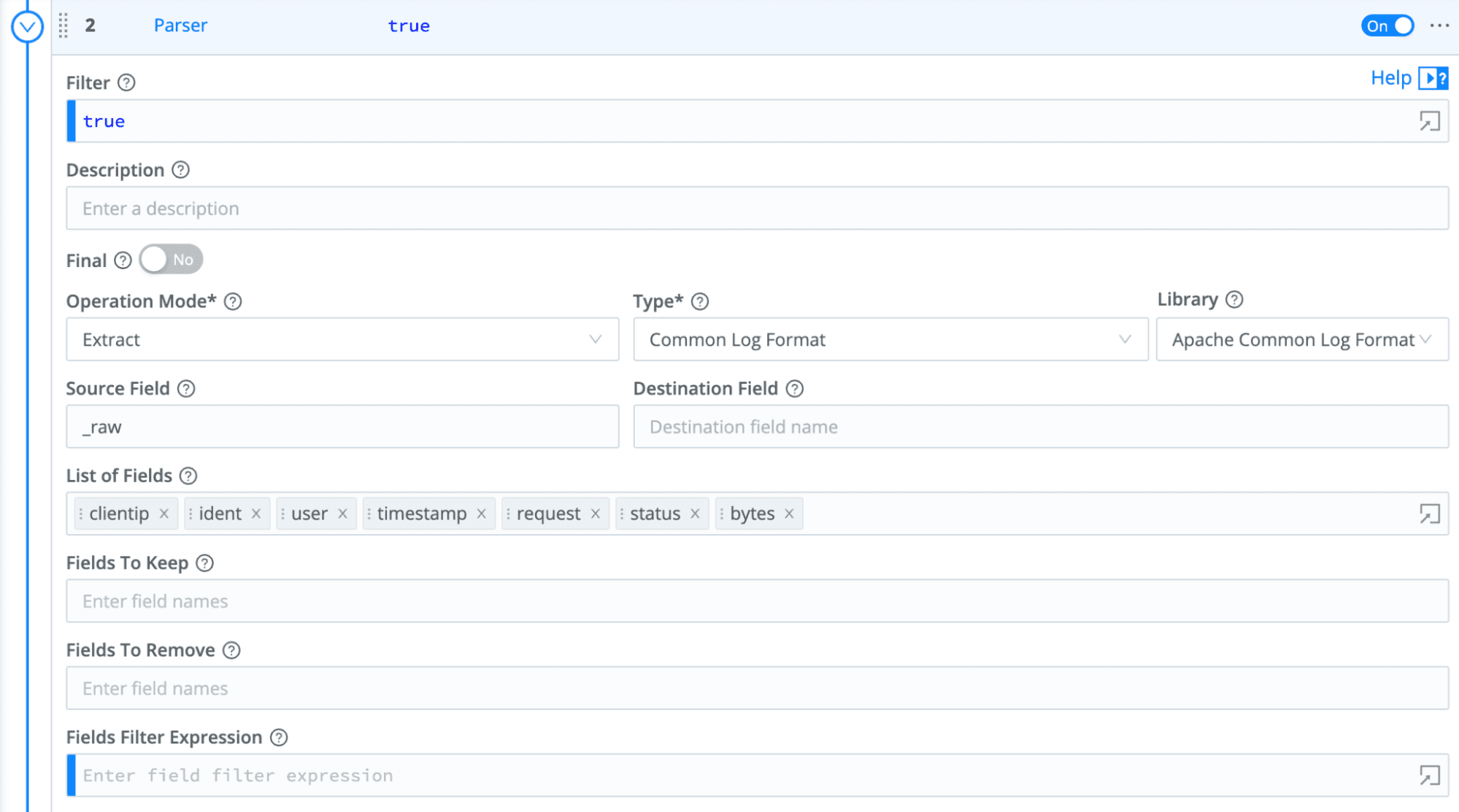
These are just two (2) Function examples. A full list of Functions to shape, reduce and transform is at your fingertips. The Cribl Docs explain the full list of Functions here.
If you’ve created Routes and Pipelines, you are just a couple of steps from creating your first Pack.
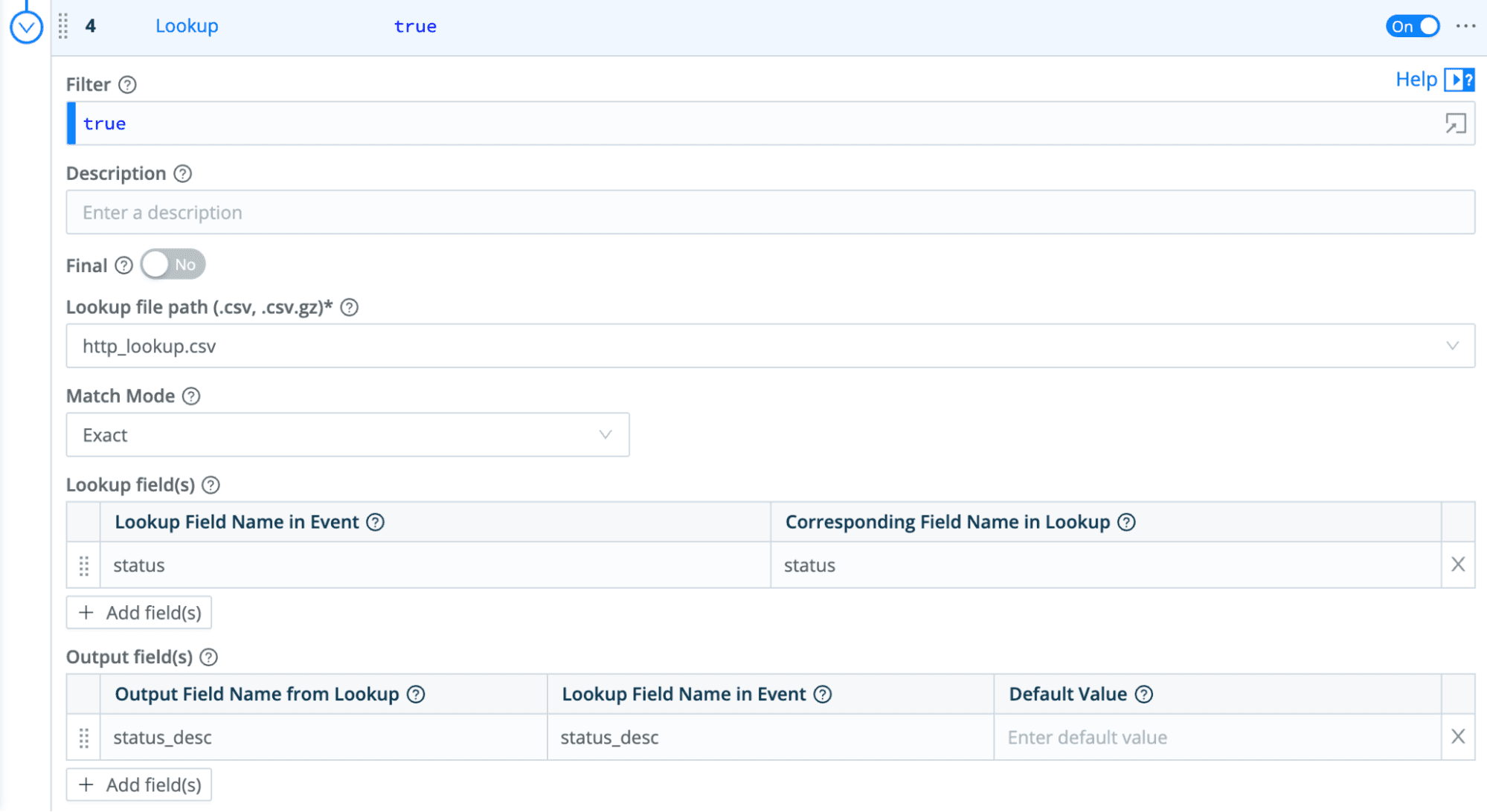
Cribl Stream ships with a Regex Library, a Knowledge Object example, that contains a set of pre-built common RegEx patterns. The video highlighted the use of a Lookup table Knowledge Object. Here, the Lookup table was used to enrich events, adding human-readable descriptions to HTTP Response codes for example. With the human-readable status descriptions added, the user of the SIEM can search the status descriptions and/or the HTTP codes, finding what they need.
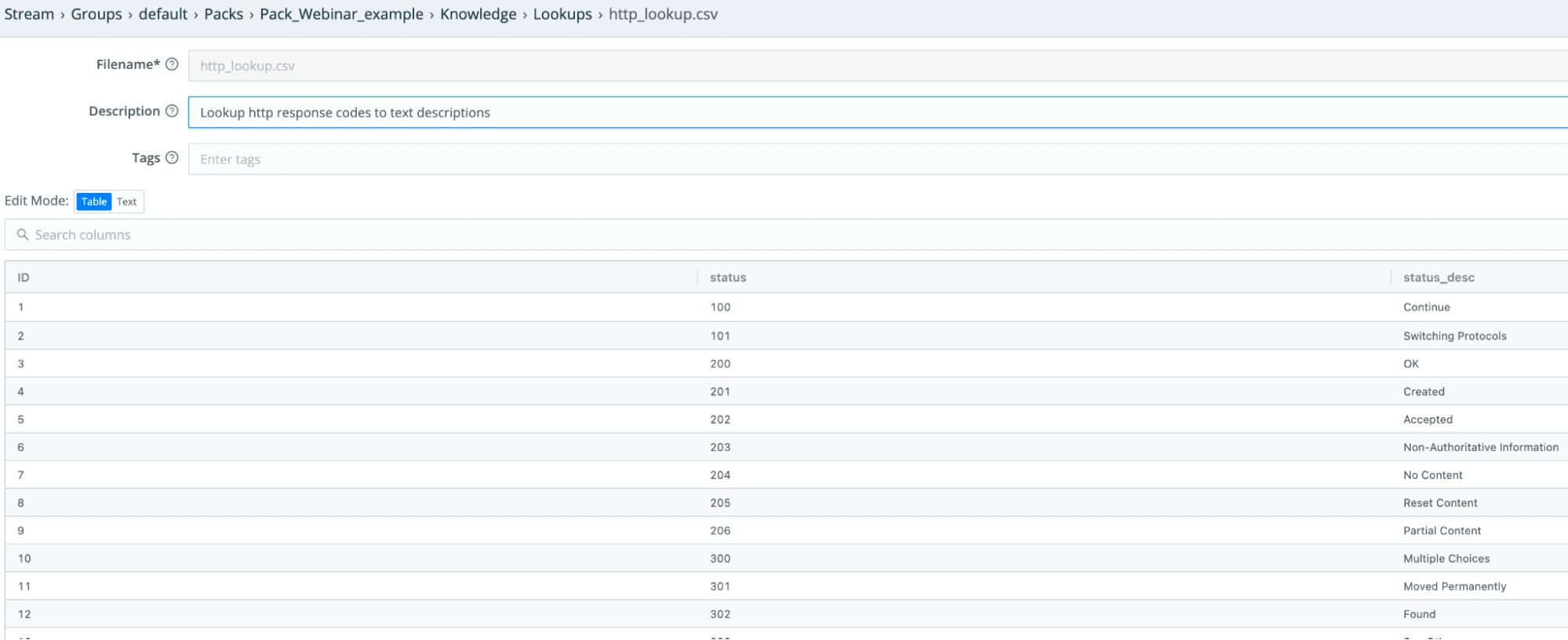
See here for more details on the power of Lookups. Collections of Events Breakers and a Parsers Library are among the Objects included. Explore all the Knowledge Objects.
You can add your own Knowledge Objects as needed. For example, the Palo Alto Network Pack includes PAN traffic Parsers right in the Pack.
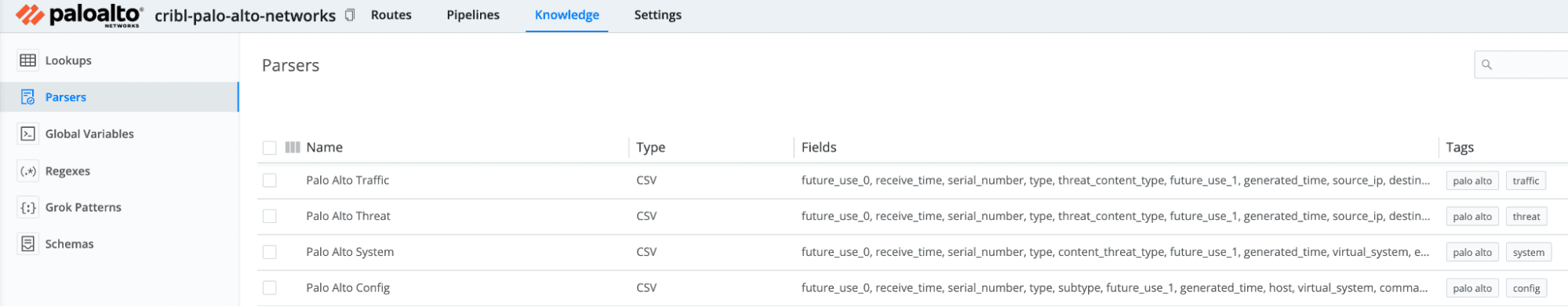
The README is your opportunity to educate the user and include answers to questions like:
What does the Pack do, and why was it created? Here, you can state what value the Pack provides.
What technologies, data sources, and data destinations does the Pack interact with?
What other dependencies does the Pack have?
Inclusion of a README is required, per the Packs Publication Standard.
Once you are confident of the processing capabilities, you can share the Pack.
Step 3: Export the Pack file
Now we are ready to share the Pack with Community or Worker Groups.
On the Manage Packs page:
Select the Pack
Click the Export button
Click Export
The resulting .crbl file can be imported into a Worker Group or published to the Cribl Packs Dispensary. The Cribl Pack Dispensary was introduced in April ‘22. It is the authoritative location for Packs. In less than 2 months, we’ve registered 800+ downloads.
Click on the Publish button to share the expertise captured in your Pack, but don’t stop there, earn prizes and recognition via the Community Packs contest. We all get by with help from our friends.
Got a question as you build your Pack? Join us in the #Packs Community Slack channel.
Happy Packing!






