This blog post explores Cribl.Cloud‘s approach to Identity Governance (IG), a crucial strategy for securing access to critical systems and data. Learn how Cribl.Cloud leverages IG to ensure security, compliance, efficiency, and customer trust, while also tackling the challenges of managing custom SaaS APIs within an IG framework.
What Is Identity Governance?
Identity Governance is the process of managing and controlling access to resources within an organization’s IT infrastructure. It encompasses the policies, processes, and technologies used to ensure that only Authorized Operators (Cribl Employees) have access to specific systems, applications, and data.
Identity Governance is crucial for maintaining security, regulatory compliance, and operational efficiency within an organization. By accurately defining and managing user roles, permissions, and access rights, Identity Governance helps mitigate the risk of unauthorized access, data breaches, and insider threats while enabling smooth operations and adherence to regulatory requirements.
Why Is It Important?
Identity Governance is integral to Cribl.Cloud’s success and sustainability. It ensures security, compliance, efficiency, customer trust, and accountability. Here’s how:
Security: By regulating access, it protects sensitive data, reducing risks like unauthorized access and breaches.
Compliance: It helps meet regulatory standards like GDPR and HIPAA through precise user access management and audit trails.
Operational Efficiency: Streamlining access management processes improves efficiency and minimizes errors.
Customer Trust: Demonstrating robust security measures and compliance builds confidence and loyalty among customers.
Auditability and Accountability: It logs access activities, aiding in investigations, internal reviews, and compliance demonstrations.
How Does Cribl Approach Identity Governance?
We initiated Proof of Concept (POC) engagements with a number of vendors to begin problem solving. After all POCs completed, our chosen solution was to utilize Okta Identity Governance to manage the Access Requests and Escalation Approvals along with Okta Workflows to implement the custom steps to integrate all components.
We then addressed the remaining problems with a three-pronged approach.
Federate with Corporate Okta
The first problem we needed to tackle was the fact that all identities of Cribl.Cloud Operators were not federated through our Corporate Okta. Since launch, we have been using Auth0 as the Cribl.Cloud Identity Provider (IDP) for both customers and employees. The requirement to control access to Cribl.Cloud through Okta meant that we needed to federate our Okta instance through our Auth0 tenant for anyone logging in with a cribl.io email address.
Federated Identity, also known as Single Sign-On (SSO), is a feature that we provide to Cribl.Cloud Enterprise customers. Any Cribl Organization Admin can configure SSO for their Organization so that all member’s identities are federated through their own OpenID Connect (OIDC) or Security Assertion Markup Language (SAML) IDP.
We used very similar mechanisms here for our Operator access. By federating our Okta IDP at a global level as opposed to individual Organizations, we achieved SSO for all Cribl Organizations for all Operators.
Reduce All Operator’s Privileges to Zero Standing Access or Read-Only Access
In order to implement a system whereby Operators can request elevated access, we needed to set up the base case where all Operators had their access reduced to Zero Standing Access or Read-Only. Throughout the lifetime of the service not having this functionality, some Operators had been permanently elevated to higher levels. Resetting the baseline opens the door for access elevation requests to be acted upon integrally.
Enable Operators to Request Elevated Access
The Cribl.Cloud service segregates customers in their own boundary using a Cribl Organization. Each Cribl Organization is assigned a dedicated AWS Account to house the Infrastructure, Control Plane, Data Plane and Search Services for all of its workloads.
The two key resources for which we must control access are the Cribl.Cloud APIs and AWS Accounts that are assigned to Cribl Organizations.
The API service can be further broken down into two functional areas:
The Admin API, used for configuring the overall system.
The Organizations API, which allows configuration of each individual Cribl Organization.
For all use cases, there is a configurable timeout period, after which access is revoked. After approval is granted, a de-provisioning workflow is scheduled to revert the elevated privileges and return the Operator to Zero Standing Access.
Whenever we need access to a Cribl Organization’s Workspace configuration or data, we adhere to strict SOC2 compliance controls and other contractual requirements to access those resources in a manner that ensures customer consent and privacy.
Use Cases
Grant Elevated Access to Cribl.Cloud Admin API
Cribl.Cloud API uses OIDC for authentication, and Auth0 FGA for its authorization layer. There is no out-of-the-box solution for Auth0 FGA. This means we will support this use case with a custom Okta Workflow to enact granting and revocation of privileges.
We want to elevate an Operator’s privileges so that they can administer the overall system but not affect any individual Organization. When approval is granted, the Okta Workflow makes a change in the Auth0 FGA database to grant elevated privileges to the Admin portion of the API. This can be seen in the workflow diagram below, after approval and validation of the request.
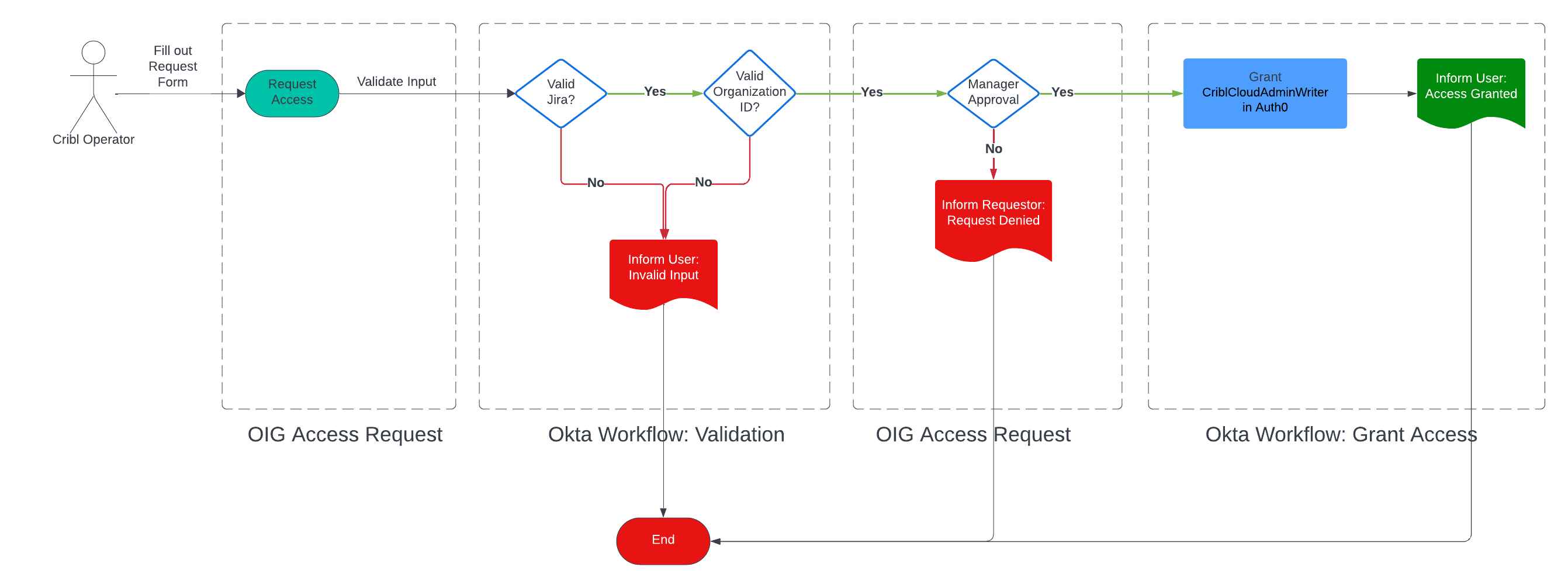
A Cribl Employee Can Request Elevated Access to “Cribl Organization Operations Admin” Role For an Organization
In this scenario, we want to elevate an Operator’s privileges so that they can administer any aspect of a single Cribl Organization. When approval is granted, the Okta Workflow needs to make a change in the Auth0 FGA database to grant elevated privileges to the operator for the Organization’s portion of the API and grant access to the Organization’s AWS Account. In this workflow, after approval and validation, both of those changes are made in their respective systems.
Granting access to the AWS Account (or Azure, or GCP equivalent in some future world) means the Operator is granted access to the infrastructure resources within (via the identity tied between the Cloud Provider and Cribl’s Okta instance). The Operator is granted access only to resources necessary to troubleshoot the issue at hand. Access can be utilized via the AWS/GCP/Azure web console or CLI commands. This even ties all the way up to our internal typescript CLI tool (named Typhon) which can enable Operators to backfill databases, manage user data and much more.
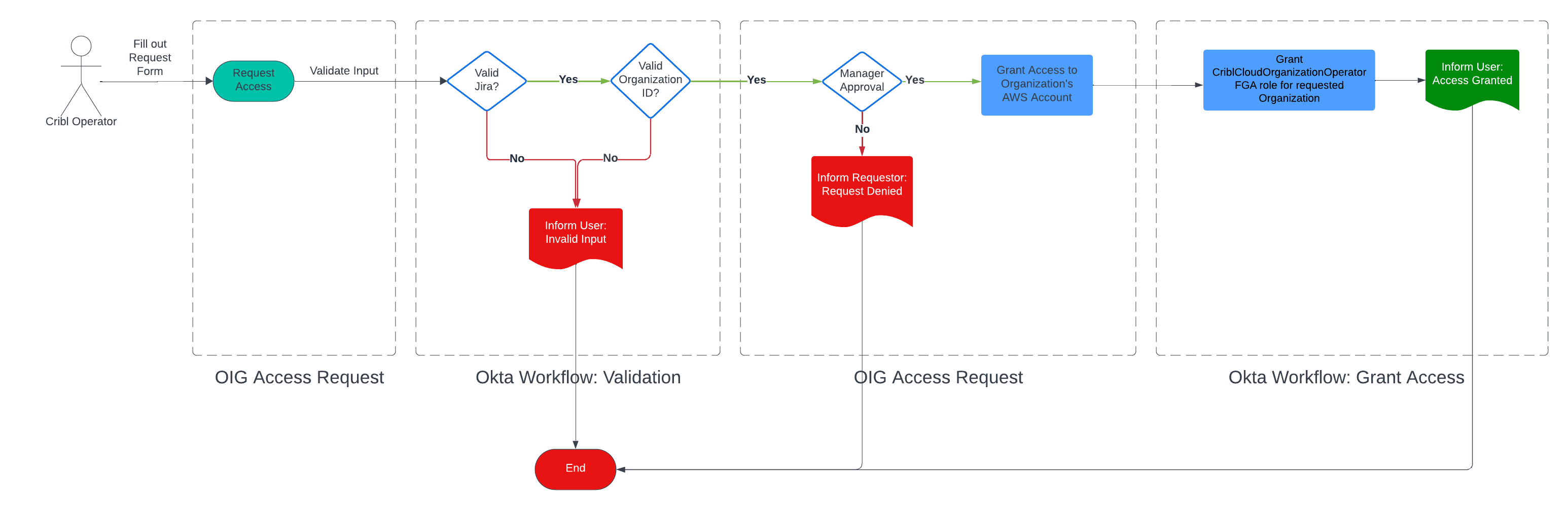
Wrap Up
Managing the diverse tools and services within Cribl.Cloud security is paramount. Implementing a single point of identity through our Okta IDP streamlines access for actors like SREs and Service Developers. This enhanced security simplifies and automates permission management. A key challenge addressed was integrating Cribl.Cloud APIs seamlessly with our Okta IDP and Okta OIG workflows.
By enforcing least privilege access principles and implementing processes for granting elevated access, we align permissions with operational needs while minimizing security vulnerabilities. Integration of auditability and tracking ensures accountability and compliance. Overall, our approach strengthens security, enhances efficiency, and mitigates unauthorized access risks across our cloud infrastructure.






