In this blog series, we’ll explore how Corelight and Cribl Stream work together to improve observability in Security Operations Centers (SOCs). In today’s rapidly changing threat landscape, it’s crucial to efficiently monitor and manage data for effective security operations. Corelight provides exceptional network visibility, while Cribl Stream gives you control and the flexibility to optimize data pipelines and gain valuable insights.
In this first post, we’ll dive into the benefits of using Corelight in a SOC, such as its ability to provide comprehensive network visibility. Then, we’ll focus on Cribl Stream— an essential tool that perfectly complements Corelight, enabling SOC teams to take full control over their data and streamline their observability processes.
But that’s not all! We’re excited to introduce the Cribl Corelight Pack, a collection of pre-built configurations and best practices specifically designed to help you leverage the integration between Corelight and Cribl Stream. This Pack simplifies deployment and configuration, empowering SOC analysts and engineers to quickly unlock the full potential of these powerful tools working together seamlessly.
If you’re ready to enhance observability in your SOC, join us as we explore the advantages of Corelight, the control provided by Cribl Stream, and the exciting possibilities enabled by the Cribl Corelight Pack.
Corelight Overview
Corelight is a network security monitoring platform that captures and analyzes network logs, generating high-fidelity data that can be used by SOC teams to enhance their threat detection capabilities. By leveraging Zeek logs collected by Corelight, SOC teams can gain deep insights into network traffic patterns, identify suspicious behavior, and rapidly respond to security incidents.
Corelight provides rich network metadata that enables SOC analysts to understand network flows, identify anomalies, and conduct comprehensive investigations. Additionally, Corelight logs offer detailed protocol analysis, allowing for the detection of both known and unknown threats. Finally, the logs provide context-rich information about network traffic, facilitating faster incident response and reducing time to remediation.
Cribl Stream and Corelight
Cribl Stream is an observability data pipeline that helps organizations efficiently route, transform, and deliver data to multiple destinations in the format that they expect. It empowers teams to add value to their data by providing flexible and customizable data routing capabilities, enabling seamless integration with platforms like Corelight.
Corelight events can be sent to Cribl Stream in a number of different ways including through raw TCP JSON, Syslog, or Splunk HEC. Once the integration is complete, users can then preview their data through live captures, save sample files, and begin creating Routes and Pipelines to best optimize their incoming events. Furthermore, events can be filtered and routed to one or many destinations such as S3 object stores for long-term retention and systems of analysis for immediate investigations.
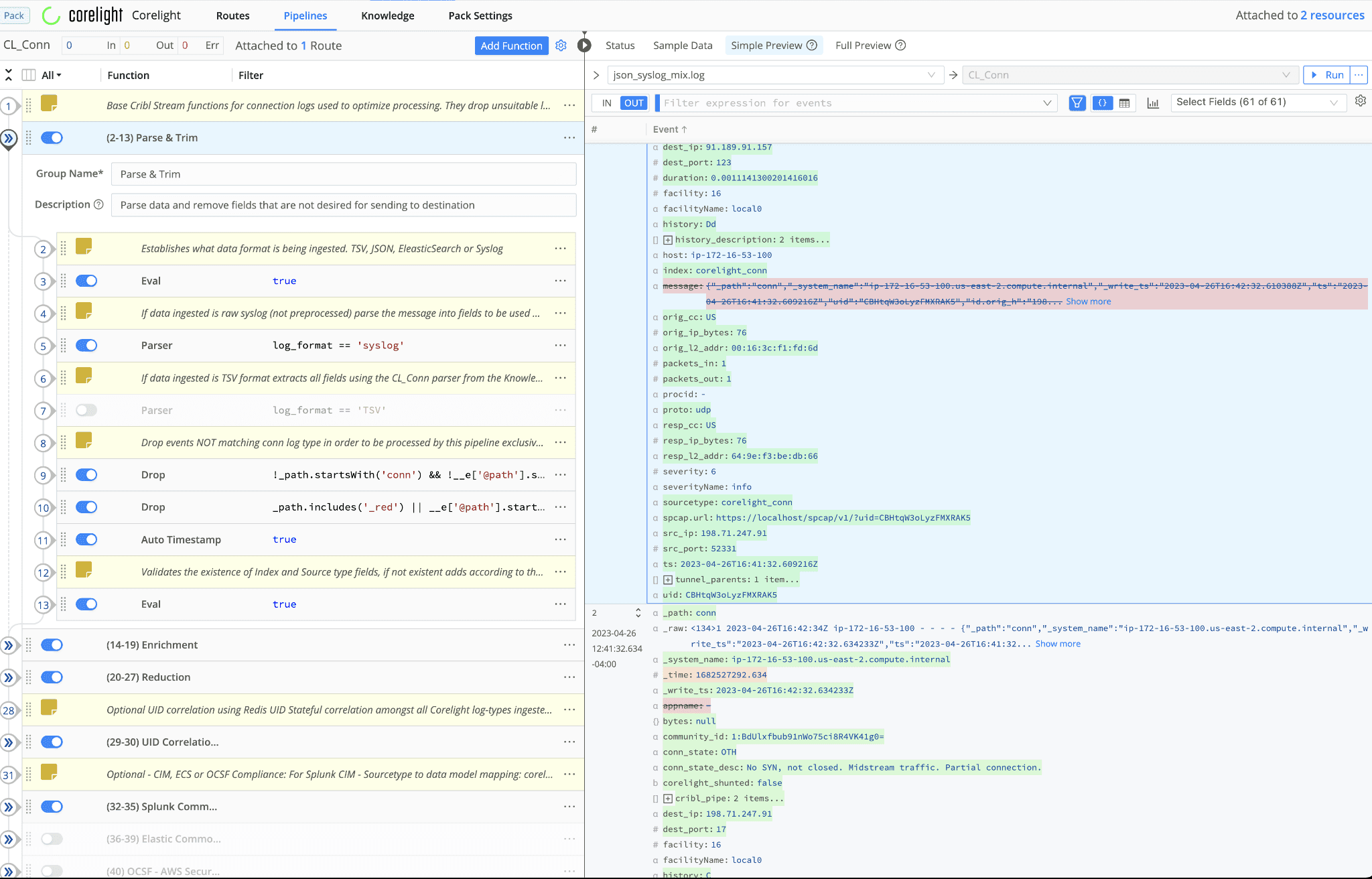
Several log-type formats are processed by the Corelight Pack (Syslog, JSON, Splunk HEC, TSV)
The Corelight Pack
Available now on the Cribl Pack Dispensary, the Corelight Pack offers Cribl Stream users and administrators out-of-the-box configurations and common use cases around more voluminous Zeek logs, like Conn and DNS. This content is fully customizable to meet a customer’s specific requirements and environment. Below is a high-level breakdown of the Pack’s components.
The Routes:
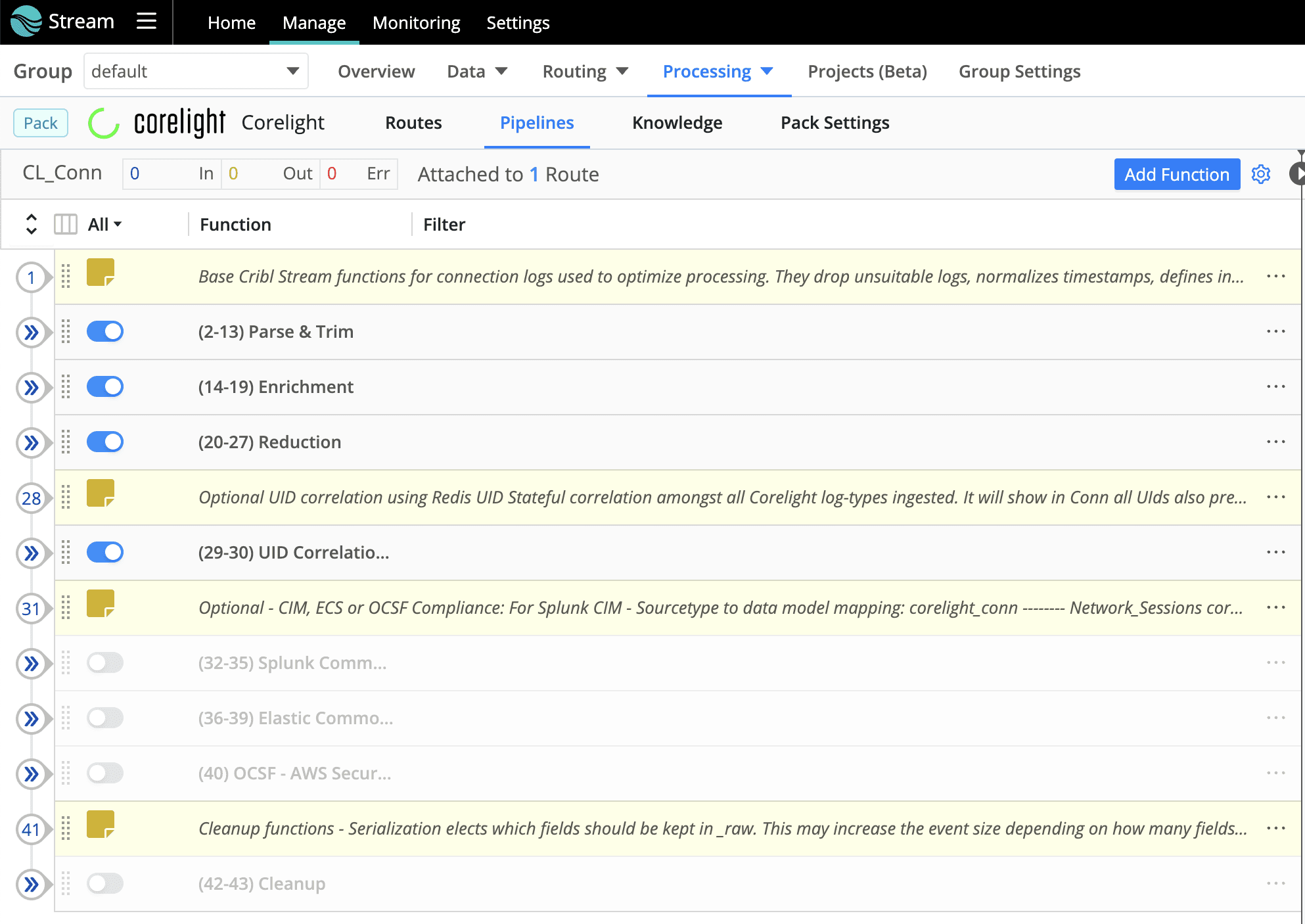
The Pack consists of Routes and Pipelines. While Routes play a crucial role in filtering data, ensuring that only relevant information is processed, Pipelines focus on four main log types: Conn, DNS, SSL, and HTTP logs. The structure of the Pack enables administrators to have control over the final outcome, with key groups such as Parse & Trim, Enrichment, and Reduction showcasing the core capabilities of Cribl Stream.
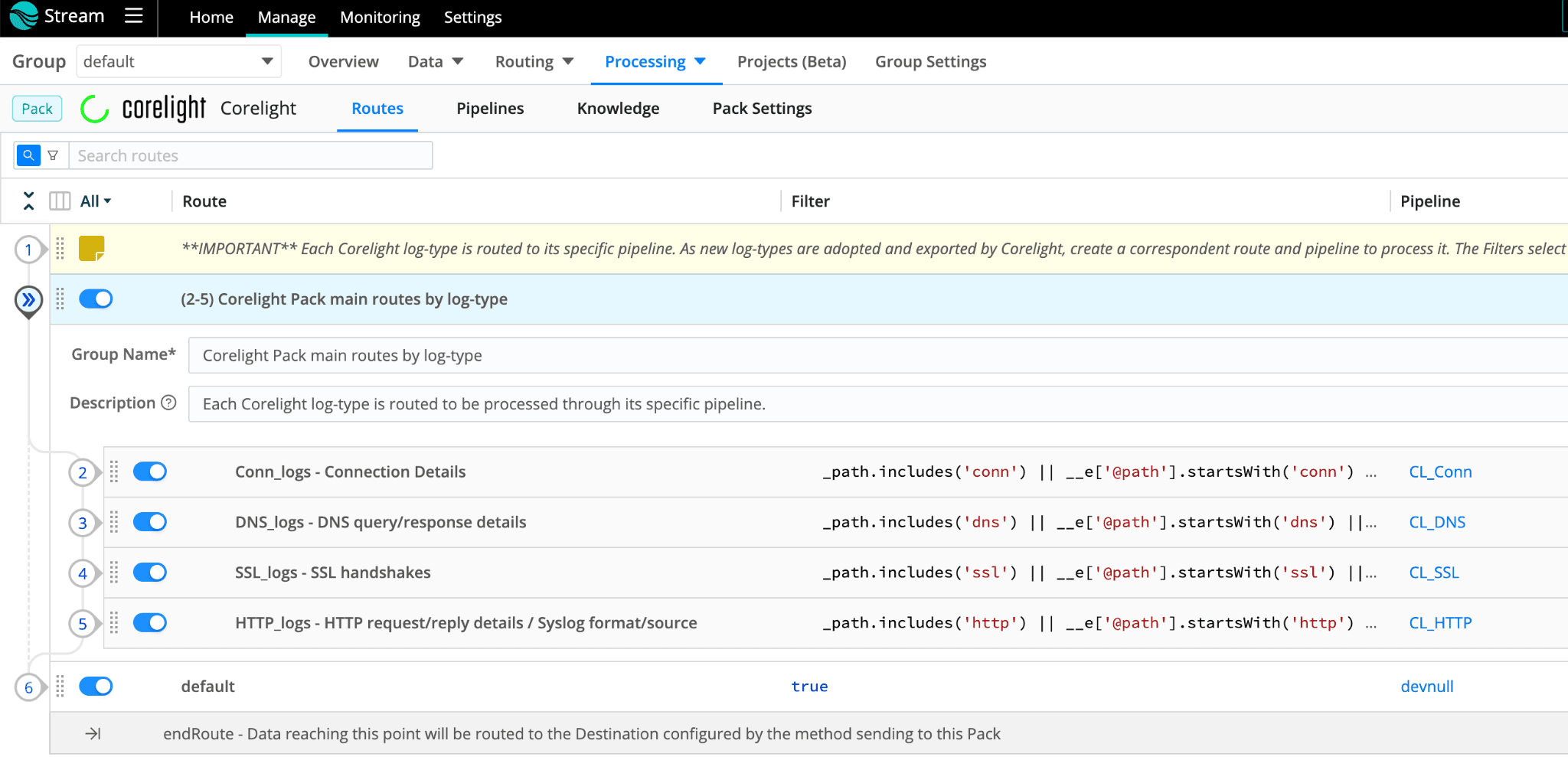
The Pipelines:
In this version (1.0.2) the Cribl Corelight Pack will cover 4 main log-types: Conn, DNS, SSL and HTTP logs. The Routes will send the data matching in their filters to each Pipeline correspondent to each log-type. Within these Pipelines, a collection of functions is designed to address common use cases observed in various SOC environments. The idea is to have a starting point that allows you to take this Pack in the direction you need based on your use cases.
The Pack incorporates a structured framework that organizes the functions into groups. These intentionally ordered groups provide you with total control over your final results. The top 3 groups are showcasing some core capabilities of Cribl Stream, they are:
Parse & Trim
Enrichment
Reduction
The remaining functions are optional and should be used sparingly. Please note that some of these functions require external components, such as Redis. Redis is an open-source, in-memory data store widely utilized by developers as a database, cache, streaming engine, and message broker. You can find more information about Redis at https://redis.io/.
There are also groups of functions in the Pipelines that normalize data in accordance to the Common Information Module (CIM) or The Elastic Common Schema (ECS) that map the fields in the stream to the respective Data Model (in Splunk) or to a common set of fields to be used when storing event data in Elasticsearch.
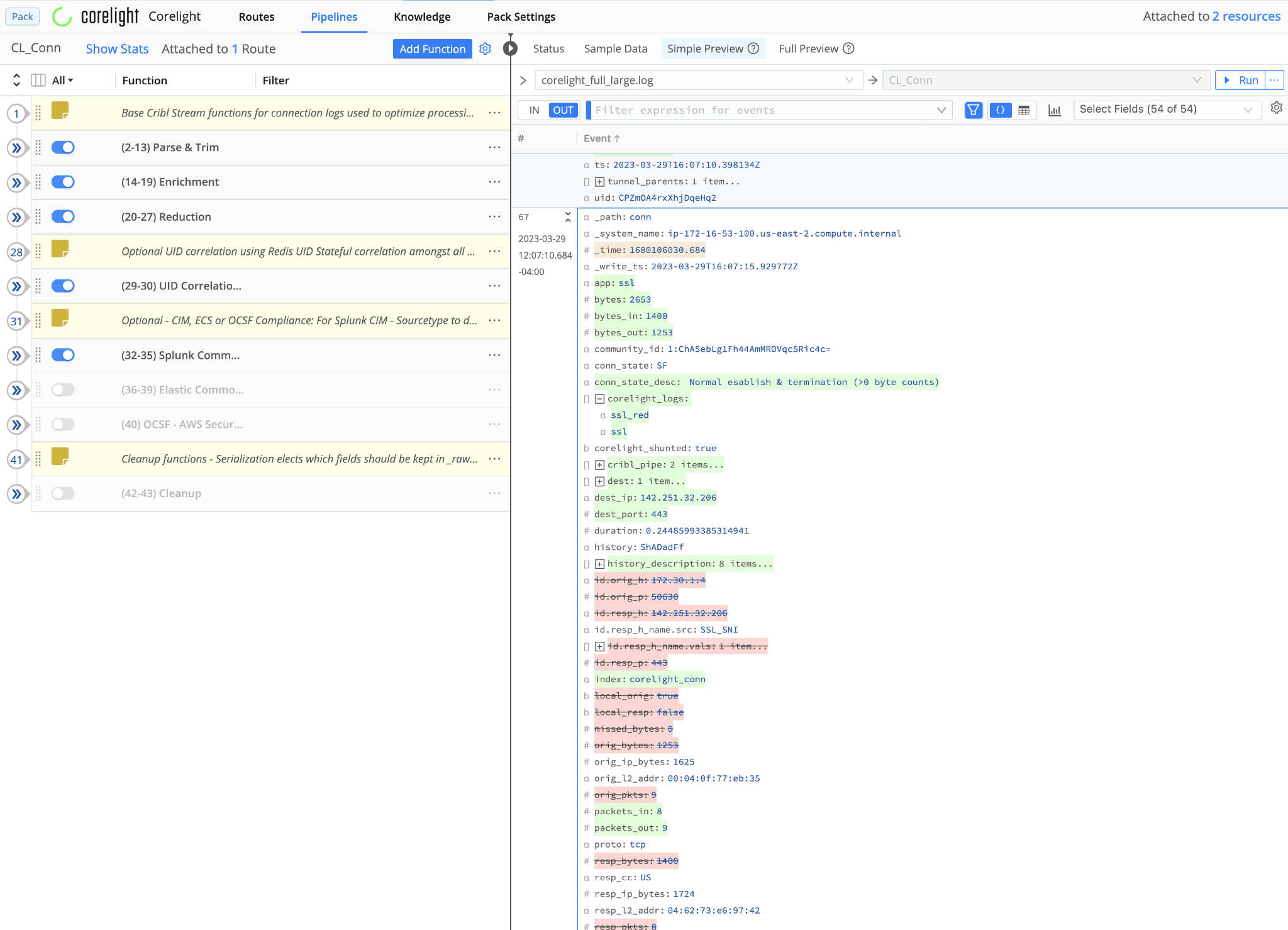
Enhanced, Reduced, and Correlated event sample (JSON)
Finally, the last set of functions in each Pipeline allows you to shape and clean up events so that they land in the destination of your choice in the format that it expects. The format choice may reflect organizations in different ways, JSON may be a better choice for some systems of analysis but CSV and Key Value Pairs are also options.
Download the Corelight Pack today to explore the included Pipelines and sample data. We’ve got some exciting blog posts coming up in this series, where we’ll highlight notable functions and capabilities in each Pipeline. We hope the Cribl Corelight Pack serves as a launching pad for additional use cases that can further enhance the SOC experience when observing Zeek logs.
We’re also hosting a webinar later this month with Corelight to show how our joint solution expands visibility, bolsters detection, and accelerates investigations while maintaining data fidelity. Register now!








