We see unfriendly customer practices all around in the SIEM space. For example, some major SIEM vendors use an Events Per Second (EPS) license model to monetize access to their tools. Typically, these vendors will drop data above the EPS license or stop data ingestion to incentive license compliance if you run over your EPS license. These license controls disrupt operations and risk enterprise security posture, which can cause chaos. The only option for most enterprises is to drop broad categories of data, such as an entire Windows event ID, since they don’t have reasonable options for being more selective. Unfortunately, this creates the risk of missing something important.
Enterprises need options for managing their EPS license. So they can own their security observability data and take control of how they use their tools instead of the vendors being in control. Cribl Stream offers enterprises the unique ability to manage their EPS license with surgical precision to minimize risk and get the most out of their existing license. Only Stream can provide this powerful capability with minimal effort due to Stream easy-to-use UI.
Details Around the Core Problem
It is super common for SecOps teams to be running over their SIEM EPS license. The usual reaction is to start dropping events such as Windows Security event id 4674. Most log shippers require you to drop the entire event from all servers with limited selective options or make changes to the endpoint OS with either method involving touching every endpoint. This is added risk and effort since they lose visibility to the entire event id. What if it makes sense to keep event id 4674, but only for certain users? SecOps teams have minimal options.
Let’s turn this idea around and consider event id 4624. This is a critical id, but when you need to drop events, you look everywhere. Event id 4624 comprises ten login types with different security values depending on your use case.
Event ID 4624 Logon Types
2. Interactive (logon at keyboard and screen of system)
3. Network (i.e. connection to a shared folder on this computer from elsewhere on the network)
4. Batch (i.e., scheduled task)
5. Service (Service startup)
7. Unlock (i.e., unattended workstation with password-protected screen saver)
8. NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with “basic authentication”)
9. NewCredentials such as RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials, see event id 4648. MS says, “A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections.”
10. RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance)
11. CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network)
What if you work in an enterprise where inbound file sharing is disabled? You do not need Logon Type 3. Stream makes it easy to drop only Logon Type 3 event ids and nothing else.
Selective Event Reduction for Event Id 4624 and Logon Type 3
Save your Windows events to the LogSteam UI using the Live Capture feature
Create a pipeline named “Windows_Event_Reduction”
Add the Regex Extract function to your pipeline to create your fields for “EventCode” and “Logon Type”
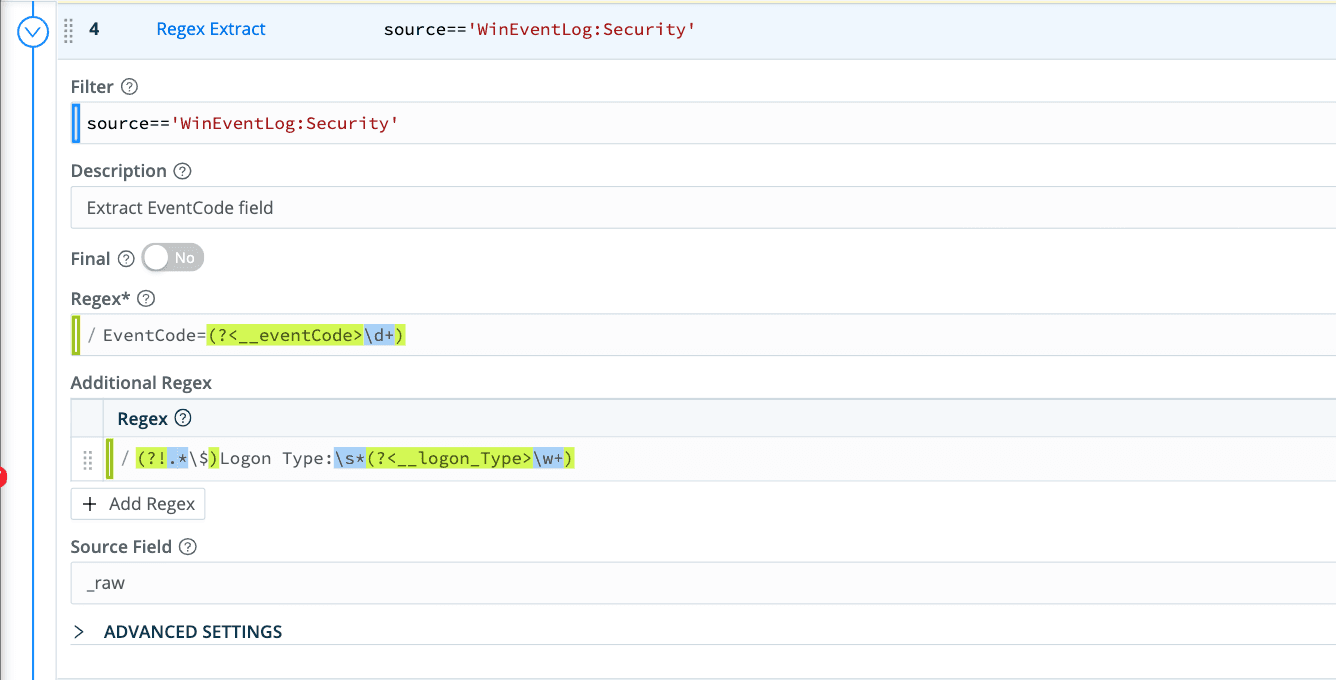
These fields will give you the foundation to build a filter only to drop these events.
Add the Drop function to your pipeline to tell Stream which events to drop using the below filter.
index=='endpoint' && source=='WinEventLog:Security' && __eventCode=='4624' && __logon_Type=='3'
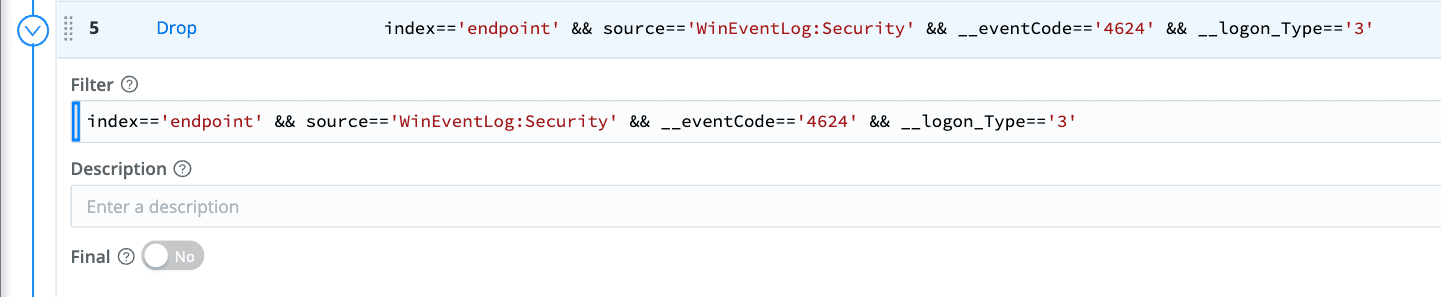
Apply this pipeline to your windows sources to start dropping only these events from your event stream. It is that simple to control your events and manage your EPS license.
Bottom Line
Stream enables SecOps teams to pick and choose each event it sends to its Security tools to get the most value and take the least risk. The Stream UI makes this quick and easy work to free up the SecOps teams for business value-focused work. Cribl Stream enables value and improves enterprise security posture.
Try Cribl’s free, hosted Stream Sandbox. I’d love to hear your feedback; after you run through the sandbox, connect with me on LinkedIn, or join our community Slack and let’s talk about your experience!
The fastest way to get started with Cribl Stream is to sign-up at Cribl.Cloud. You can process up to 1 TB of throughput per day at no cost. Sign-up and start using Stream within a few minutes.






