A security data lake is a central repository that allows you to store, manage, and analyze large volumes of security-related data long-term. This allows for effective threat hunting, fast investigations, and a foundation for exploring and analyzing data using various security tools.
What is a Security Data Lake?
A data lake is a centralized repository that stores raw data in its native format, without the constraints of predefined structures. Data lakes are a flexible and scalable solution that can accommodate massive amounts of data from various sources. A security data lake is specifically designed to handle large-scale data from various security sources such as firewalls, intrusion detection, endpoint security, and log files.
A security data lake is:
Centralized: Security data is scattered across different systems in an organization. A data lake brings it all together in one place, making it easier to find and analyze.
Scalable: Security data can grow massively. A data lake can handle this growth, allowing you to store years of security information.
Flexible: You can store all sorts of data in a security data lake, even if you don’t know exactly how you’ll use it yet. This lets you explore your data for new security insights.
The Rise of Security Data Lakes
The rise of security data lakes represents a significant advancement in the realm of cybersecurity, driven by the growing need to handle vast amounts of diverse data generated by modern IT environments. As traditional security tools struggle to handle the ever-increasing volume and complexity of security data, organizations have turned to security data lakes.
Security data lakes offer a solution by providing a central, scalable repository for all this information. This allows for improved threat detection, faster response times, and a more proactive security posture, making them a valuable tool in today’s evolving cybersecurity landscape.
Security Data Lake vs SIEM
Both Security data lakes and security information and event management (SIEM) solutions are essential for a comprehensive security strategy. They serve different purposes but are often used in complementary ways.
Security Data Lake
Purpose: Flexible storage for diverse datasets
Data Handling: Stores raw, unprocessed data
Data Volume: Capable of handling massive data volumes from a variety of resources
Data Ingestion: Collects data from various security tools, systems, applications – in any format
Scalability: Built to scale and accommodate growing data storage needs
Use Cases: Advanced threat detection, behavior analytics, historical data analysis
SIEM
Purpose: Specialized in security event management, real-time monitoring, and incident response
Data Handling: Collects, processes, and analyzes event data in real-time
Data Volume: Handles less data volume – focused on relevant security events
Data Ingestion: Collects data primarily from security tools and systems, ingests processed or semi-processed log and event data
Scalability: May have limitations compared to vast storage capacity of a data lake
Use Cases: Real-time monitoring, alerting, and incident response
Best Practices
When looking to implement a security data lake solution, there are a few best practices you can do to ensure you’re set up for success:
Define Clear Objectives: identify the specific goals and outcomes you want to achieve with a security data lake. This includes the types of data you need to collect and store, the threats you want to detect, and the compliance requirements you need to meet.
Data Integration and Centralization: Make sure your security data lake can integrate and centralize data from various sources, such as network logs, application logs, endpoint data, threat intelligence feeds, and cloud services. Having a central repository is crucial for comprehensive threat detection and analysis.
Data Tiers: Categorizing data based on access frequency and importance helps optimize cost and performance.
Security and Access Controls: Make sure data is secure, encrypted both at rest and in transit, and with strong access controls so only the right people on the right teams have the right access to the data.
Data Governance and Management: Establish robust data governance policies and procedures to manage the lifecycle of the data in the lake. This includes defining data retention policies, ensuring data quality, and maintaining an audit trail for data access and modifications.
Benefits of Using a Data Lake Dedicated to Security
Security teams using a dedicated security data lake can enjoy many benefits including:
Improved threat detection: By analyzing all your security data together, you can identify threats that might be missed by looking at individual systems.
Faster incident response: With all your data in one place, you can investigate security incidents more quickly and efficiently.
Better threat hunting: Security data lakes allow you to proactively search for threats that may not be yet known.
Stronger security posture: By understanding your security data better, you can make better decisions about how to protect your organization.
Real-World Use Cases
Security data lakes provide a scalable, cost-effective way to collect, store, and analyze vast amounts of security data from across the enterprise. They enable advanced threat hunting, historical investigations, and analytics while offloading expensive SIEM storage — improving detection, response, and long-term visibility.
Threat Hunting:
Leverage historical security data stored in the data lake to proactively search for indicators of compromise (IOCs) linked to newly discovered threats. Analysts can query vast amounts of past data,such as logs, traffic records, and event metadata,to identify traces of attack campaigns that went undetected at the time they occurred.Detection and Response:
Correlate security events across diverse data sources within the data lake to reconstruct attack timelines and understand incident scope. The centralized data repository enhances the ability to detect complex attack patterns, streamline investigations, and improve response times for both real-time and post-incident analysis.Security Analytics and Trend Analysis:
Utilize the security data lake as a scalable, cost-effective platform for long-term storage and advanced analytics. This supports trend analysis, threat pattern recognition, and continuous improvement of security operations by providing historical context for evolving risks and operational insights.SIEM Integration:
Extend SIEM capabilities by integrating it with the security data lake to offload long-term data retention and enable advanced querying. This allows SIEMs to focus on real-time monitoring while leveraging the data lake for deep-dive investigations, historical correlation, and the generation of alerts from enriched datasets.
The Challenges of Security and Governance for Data Lakes
With massive amounts of sensitive security data stored in data lakes, it makes it a prime target for hackers and bad actors to attempt to gain access to them.
Data Access Control
Ensuring proper access control is complex due to the vast and varied types of stored data. Implementing granular permissions to restrict access based on roles and responsibilities is essential but can be difficult to manage.
Compliance and Regulatory Requirements
Data lakes often store sensitive information that must comply with various regulations, such as GDPR, HIPAA, and CCPA. Ensuring ongoing compliance and maintaining audit trails is a significant challenge.
Data Encryption and Privacy
Protecting data in transit and at rest with robust encryption mechanisms is crucial but can be resource-intensive. Ensuring data privacy, especially for personally identifiable information (PII), requires meticulous planning and implementation.
Data Lifecycle Management
Managing the lifecycle of data, including retention, archiving, and deletion policies, is complex due to the sheer volume and variety of data. Effective lifecycle management is necessary to prevent data sprawl and ensure compliance.
Scalability and Performance
As data volumes grow, maintaining scalability and performance while ensuring robust security and governance can be difficult. Balancing these aspects requires continuous monitoring and optimization.
How to Build or Evaluate a Security Data Lake
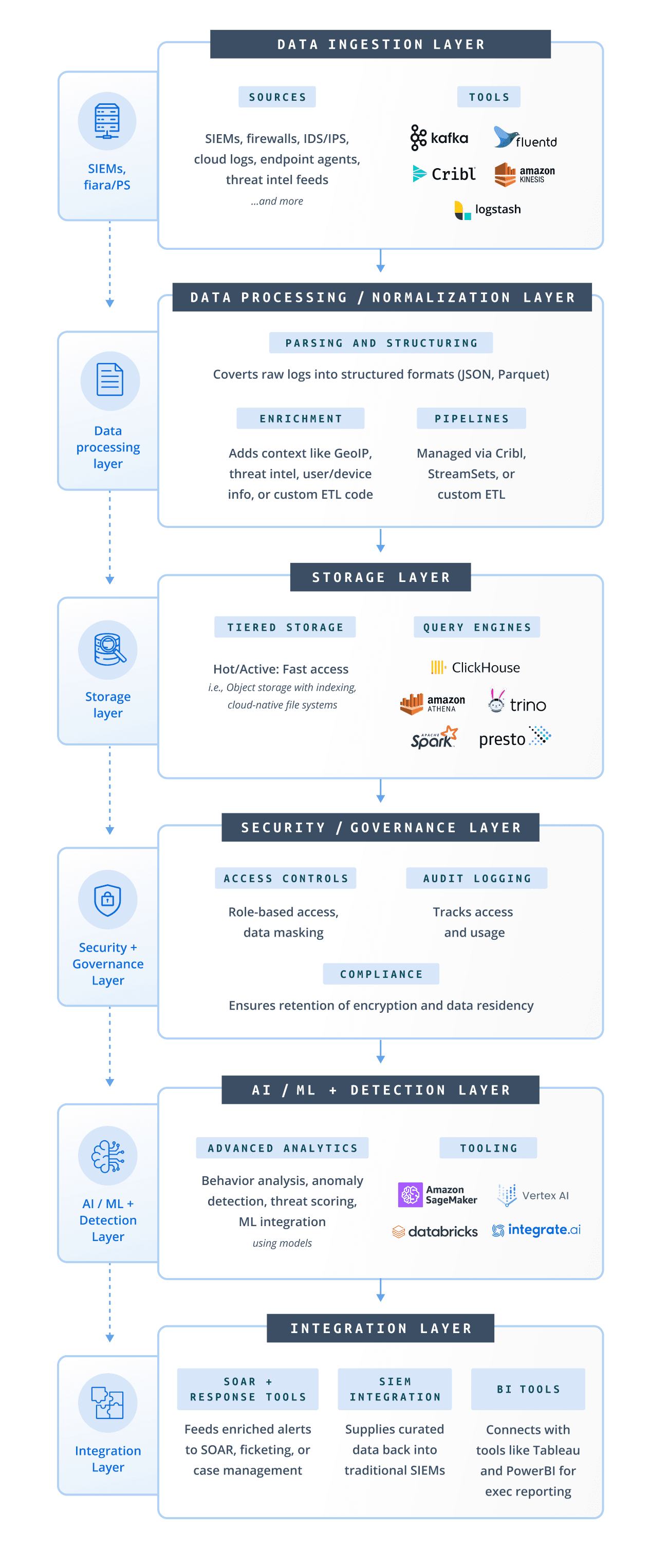
Building or specifying a security data lake requires a platform that can ingest large volumes of security data, such as logs from SIEMs, firewalls, and cloud services,in real-time or batches. The architecture should offer scalable, cost-efficient, and tiered storage with strong security, compliance, and governance features. Extensibility, analytics support, and operational simplicity are essential for long-term value and adaptability to evolving threats.
Key Points
Flexible Ingestion: Can it handle diverse, high-volume, real-time and batch data?
Scalable Storage: Does it offer tiered, cost-effective retention in cloud or hybrid settings?
Security & Compliance: Are encryption, RBAC, and logging built in? Is it compliant with relevant regulations?
Data Governance: Are metadata tagging, PII redaction, lifecycle, and lineage supported?
Analytics Ready: Are low-latency queries, ML, and integration with security tools possible?
Operational Ease: Is deployment, monitoring, and cost management straightforward?
Future-Proof: Is the design open, extensible, and adaptable to new technologies and threats?
Cribl for Your Security Data Lake Needs
Cribl Lake is a cost-effective storage solution that makes it easy to store, manage, and access massive volumes of security data. With this solution, you can store full-fidelity data long-term. In addition, you can use Cribl Search to run powerful queries on data stored in Cribl Lake, all data lakes, object stores, search APIs, and analytics solutions like OpenSearch. Having a dedicated data lake for security teams means there’s no cloud or data expertise needed to get started.
Speed: get up and running in minutes. Zero configuration with automated provisioning creates a fully usable cloud data lake in minutes, not months.
Ease: easily get data in, and get data out. Schema-on-need delivers the format you need when you need it. Unified security policies keep data safe and prevent unauthorized access.
Choice: store data where it makes sense and in open formats, no vendor lock-in. Your storage or ours, you decide.
SDL Trends & Future Outlook
Security Data Lakes (SDLs) are gaining significant traction among enterprises as they seek more scalable, cost-effective, and flexible solutions for managing ever-growing volumes of security telemetry. A major driver of SDL adoption is the rising cost and complexity of traditional SIEM platforms, which often struggle to keep pace with modern data demands.
In contrast, SDLs leverage schema-on-read architectures, allowing organizations to ingest and store raw data first, and apply structure only when needed,greatly enhancing agility and enabling deeper, more customizable analytics. The increasing need for unified telemetry across cloud, endpoint, network, and identity sources is also pushing organizations toward SDLs as a centralized repository for comprehensive visibility. Furthermore, the emergence of standards like the Open Cybersecurity Schema Framework (OCSF) and services like AWS Security Lake are accelerating adoption by promoting interoperability, reducing data silos, and simplifying integration across tools.
As these technologies mature, SDLs are poised to become foundational to modern security operations, offering a future-proof approach to threat detection, investigation, and response.
Frequently Asked Questions
What’s the difference between a security data lake and a SIEM?
A SIEM is a security analytics platform that collects, normalizes, and analyzes log data—often with limited retention and high costs. A security data lake, on the other hand, stores raw, structured, and semi-structured data at scale, offering more flexibility for custom analysis and long-term retention.
What types of data can be stored in a security data lake?
Security data lakes can ingest and store logs, metrics, traces, network traffic, endpoint data, cloud telemetry, and threat intelligence feeds—essentially any machine data relevant to security operations.
Is a security data lake secure?
Yes—when implemented with strong controls. Security data lakes rely on encryption, role-based access control, data masking, and audit logging to protect sensitive data and meet compliance requirements.
How does a security data lake improve threat detection?
By storing large volumes of diverse data for longer periods, a security data lake enables deeper correlation, anomaly detection, and retrospective analysis—leading to faster detection of advanced threats and root cause investigation.