Cybersecurity professionals use threat management to take down cyber threats, prevent cyberattacks, and handle security incidents effectively. It helps organizations proactively manage risks, protect sensitive data, and ensure operational continuity. Effective threat management reduces the impact of security incidents, safeguarding both the organization’s assets and its reputation.
What is Threat Management?
Threat management is the process of identification, protection, detection, response, and recovery from security threats. It’s a crucial aspect of cybersecurity. It’s designed to protect organizations from potential threats that could compromise their data, operations, and overall security posture.
Why is threat management important?
Threat management is vital because it helps organizations proactively manage and mitigate risks, protecting sensitive data and ensuring operational continuity. When done effectively it reduces the risk of data breaches and other security incidents.
By implementing strong threat management strategies, businesses can stay ahead of evolving threats and maintain trust with their stakeholders. Security teams rely on these strategies to prevent cyber attacks and ensure the safety of critical assets. Proactive threat management also helps in maintaining compliance with industry standards like the NIST cybersecurity framework.
How does Threat Management work?
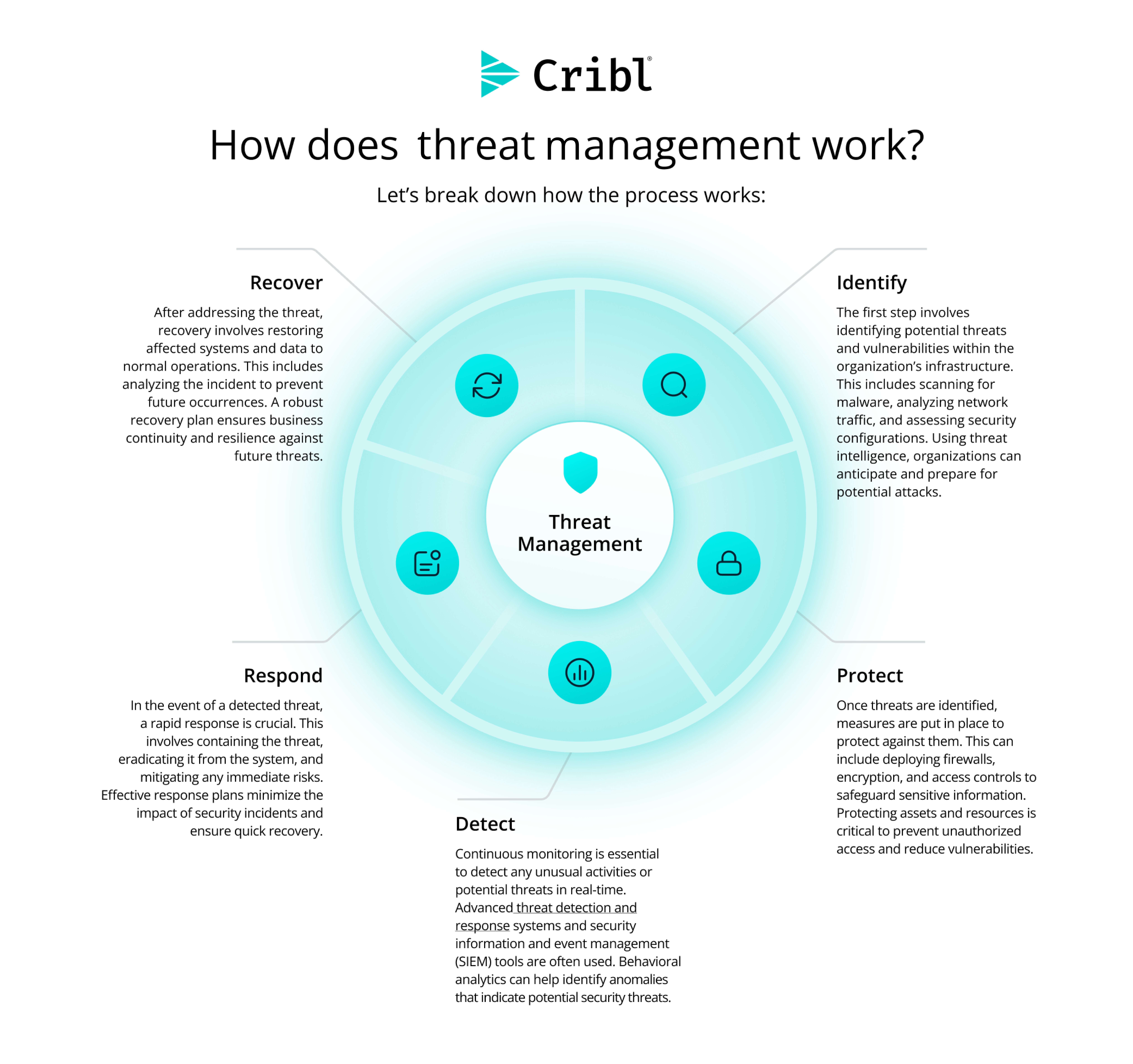
Let’s break down how the process works:
Identify
The first step involves identifying potential threats and vulnerabilities within the organization’s infrastructure. This includes scanning for malware, analyzing network traffic, and assessing security configurations. Using threat intelligence, organizations can anticipate and prepare for potential attacks.
Protect
Once threats are identified, measures are put in place to protect against them. This can include deploying firewalls, encryption, and access controls to safeguard sensitive information. Protecting assets and resources is critical to prevent unauthorized access and reduce vulnerabilities.
Detect
Continuous monitoring is essential to detect any unusual activities or potential threats in real-time. Advanced threat detection and response systems and security information and event management (SIEM) tools are often used. Behavioral analytics can help identify anomalies that indicate potential security threats.
Respond
In the event of a detected threat, a rapid response is crucial. This involves containing the threat, eradicating it from the system, and mitigating any immediate risks. Effective response plans minimize the impact of security incidents and ensure quick recovery.
Recover
After addressing the threat, recovery involves restoring affected systems and data to normal operations. This includes analyzing the incident to prevent future occurrences. A robust recovery plan ensures business continuity and resilience against future threats.
Types of Threat Management
There are two main types of threat management: Unified and Security. Let’s break them down.
Unified Threat Management
This approach integrates multiple security functions, such as firewalls, antivirus, and intrusion detection systems (IDS), into a single platform for streamlined management. UTM simplifies security operations and enhances the efficiency of threat management systems.
Security Threat Management
Focuses specifically on identifying and mitigating threats that target the organization’s security infrastructure, including network and endpoint security. Security threat management solutions are critical for defending against sophisticated cyber attacks.
What's the difference between a threat, risk, and vulnerability?
Threat
A potential cause of an unwanted incident that may result in harm to a system or organization. Threats can come from various sources, including cyber attacks, data breaches, and insider threats.
Vulnerability
A weakness in a system that can be exploited by threats to gain unauthorized access or cause damage. Effective vulnerability management involves regular assessments and patching to minimize risks.
Risk
The potential for loss or damage when a threat exploits a vulnerability. It’s measured by the likelihood and impact of the threat. Organizations need to manage risks by implementing comprehensive threat management solutions.
What are some effective ways to detect threats?
Effective threat detection involves using a combination of technologies and methodologies, such as:
Intrusion Detection Systems (IDS) - Monitor network traffic for suspicious activities and potential threats. IDS can detect threats and vulnerabilities in real-time, providing early warnings to security teams.
Security Information and Event Management (SIEM) - Aggregates and analyzes log data from various sources to identify patterns indicative of security incidents. SIEM systems enhance threat intelligence by correlating data from multiple security tools.
Behavioral Analytics - Uses machine learning to detect anomalies in user behavior that could signify a threat. This approach helps identify evolving threats and provides deeper insights into potential security risks.
Cribl Threat Management Solutions
Effective threat management relies heavily on the efficient collection, processing, and analysis of security data. Observability pipelines, like those enabled by Cribl solutions, play a significant role in managing security data flows and preparing data for security use cases. These capabilities can assist organizations in enhancing threat detection, streamlining investigations, and optimizing data handling for security tools.
Supercharge Security Insights
Enhance the visibility of security data, enabling better threat identification and analysis. This helps security teams stay ahead of potential threats and make informed decisions.
Shape and Enrich: Normalize disparate data formats, parse complex logs, and enrich events in-flight with crucial context like GeoIP details, user information, asset data, or threat intelligence lookups.
Improve Signal-to-Noise: Filter out redundant or low-value events at the source, reducing analyst fatigue and ensuring your team focuses on the alerts that truly matter.
Faster Detection: Enhanced visibility and cleaner data pipelines mean quicker, more accurate threat identification and analysis, helping your SecOps team stay ahead and make confident, informed decisions.
Immediate Access to Archived Data
Quick access to historical data is essential for investigating security incidents and understanding past threats. Cribl’s solutions ensure that archived data is readily available for threat analysis and incident response.
Search Low-Cost Storage Without Moving It First: Query data archives in cost-effective object storage (like Cribl Lake, AWS S3, Azure Blob, or a telemetry Lakehouse without the need for time-consuming and costly rehydration.
Accelerate Investigations: Conduct historical threat hunting, investigate security incidents, and understand attack timelines in minutes, not hours or days.
Reduce MTTI/MTTR: Drastically cut down Mean Time to Investigate (MTTI) and Mean Time to Respond (MTTR) by making all relevant data readily accessible for your incident response teams.
Reduce Log Volume & Pay Less for Infrastructure
Efficient log management reduces the volume of data that needs to be processed, lowering infrastructure costs and streamlining threat detection processes.
Intelligent Reduction: Filter noisy data, sample strategically, aggregate similar events, and route full-fidelity logs to low-cost storage — all to reduce the volume sent to expensive analytics tools.
Maximize SIEM Value: Improve the signal-to-noise ratio in your SIEM, making actual threats easier to spot and reducing license-straining ingestion volumes.
Reallocate Resources: Lower infrastructure and licensing costs associated with data handling, freeing up budget and valuable team resources for higher-impact security initiatives and tools.
Route From Any Source To Any Destination
Flexibility in routing data ensures that all relevant security information is available where needed, enhancing the overall effectiveness of the threat management system.
Unify Your Stack: Collect data once from any source (agents, syslog, APIs, cloud platforms) and route it simultaneously to multiple destinations in the required format.
Enable Best-of-Breed: Send enriched alerts to your SIEM, full logs to a cost-effective data lake or archive, specific Indicators of Compromise (IoCs) to your SOAR platform, and key metrics to monitoring tools—all from one central control plane.
Break Silos & Avoid Lock-In: Maintain flexibility in your security architecture, easily swap tools in or out, and ensure every component gets precisely the telemetry data it needs, when it needs it, without being locked into proprietary formats or collection tools and methods.
By leveraging Cribl’s threat management system, organizations can better protect against cyber threats and ensure compliance with standards set by the National Institute of Standards and Technology (NIST). Cribl’s solutions help reduce the risk of security incidents and improve overall threat landscape visibility.