Only last month, Cribl added Snowflake to its growing list of accessible data stores it can search. Using Cribl Search, admins can now leverage Cribl’s search-in-place capability to query data located in Snowflake’s data warehouse.
Boy, did we have the timing right? Today, Snowflake customers and other incident response teams are still determining the nexus of the incident. Cribl’s focus is providing a simple way to audit your Snowflake internal tables to identify any potential threat activity in your Snowflake accounts.
In Snowflake’s post, they have identified specific source IP addresses of concern and malicious traffic from clients with unique characteristics. Cribl Search allows users to quickly define queries to identify if any of those source addresses and/or client characteristics exist in their accounts. These queries can be done ad hoc or, as Cribl recommends, on a scheduled basis. If a scheduled search detects any identified IOCs, notifications can be automatically generated, alerting administrators, SOC teams, or others about immediate issues.
Cribl Search Notifications allow administrators to send messages in multiple formats, including Email, PagerDuty, Slack, AWS SNS, or even a Webhook, which may be used to automate actions launched by your SIEM. Additionally, depending on the type of notification used, you can customize the priority and subject of message information.
How to Use Cribl Search to Query Snowflake Account Usage Tables
Query your Snowflake account for login history, IP addresses, or suspected clients in easy to follow steps.
Note: For these searches, Snowflake ACCOUNTADMIN privileges are required.
Alternatively, you can create a view that has appropriate privileges using this technique from Snowflake:
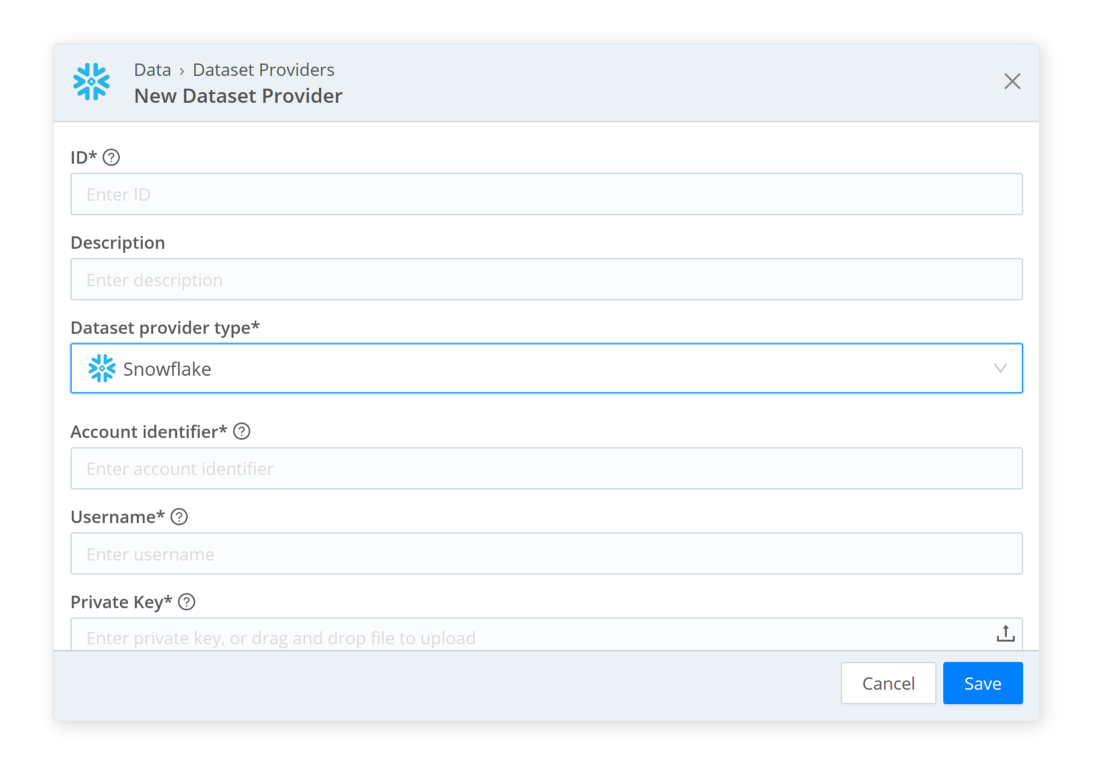
First, create a Snowflake Dataset Provider – this tells Cribl Search where to look
- Provide a unique identifier (name), add a description, and provide your account credentials. Then, follow the procedure in our docs or the previous blog to connect your Snowflake instance to Cribl Search.
Next, create a Snowflake Dataset. This is used to identify what data to search for within your Snowflake account.
This will require creating two datasets: (You will need to supply their Warehouse name, as usual)
- Dataset Name:
snowflake_account_access for the query below
- Identify the Database/Schema/Table:
Snowflake | Account_Usage | login_history
- Dataset Name:
snowflake_sessions for the query below
- Identify the Database/Schema/Table:
Snowflake | Account_Usage | sessions
For each Dataset, provide the name, description, and the Snowflake destination to target. Note that your Snowflake admin will have to provide the name of your Warehouse.
Check out our docs for a full, step-by-step guide configuration for your Snowflake account.
Now, we configure Cribl Search for what to look for based on Snowflake’s instructions.
- This requires separate query configurations, one for each Snowflake table being searched:
snowflake_account_access dataset now points to Snowflake.Account_Usage.login_history (for IP addresses)snowflake_sessions dataset now points to Snowflake.account_usage.sessions (for client)
- Query dataset
snowflake_account_access for suspicious IP addresses:
- This query looks for a
client_ip that matches the information provided by Snowflake.
- Cribl recommends including a known source IP address in the query to confirm proper operation. In the example below, we show Xs and comment (//) it as the test bad guy.
- Complete list of problematic addresses from Snowflake docs
dataset="snowflake_account_access"
| where CLIENT_IP in
('104.223.91.28',
'198.54.135.99',
'184.147.100.29',
'146.70.117.210',
'198.54.130.153',
<many addresses omitted> ,
‘195.160.223.23’,
'XX.XX.XX.XX') // test bad guy
Note: The Snowflake blog above list identifies ~ 300 IPs; you can paste all in the query or optionally create a separate lookup table with IPs and reference that in the search.
- Query dataset snowflake_sessions for suspicious clients.
- This query examines the
Client _Environment field for a specific value.
- Cribl recommends including a known application and OS in the query to confirm proper operation; see the example below. As shown below, we comment (//) it as a smoke test.
- List of problematic clients from Snowflake docs
dataset="snowflake_sessions"
| extract type=json source=CLIENT_ENVIRONMENT
| where APPLICATION == 'rapeflake'
or
( APPLICATION == 'DBeaver_DBeaverUltimate'
and OS == 'Windows Server 2022' )
// or (APPLICATION == 'xx' and OS == 'yyyy') // smoke test
With any luck, neither query will return results = which means no potential malicious clients.
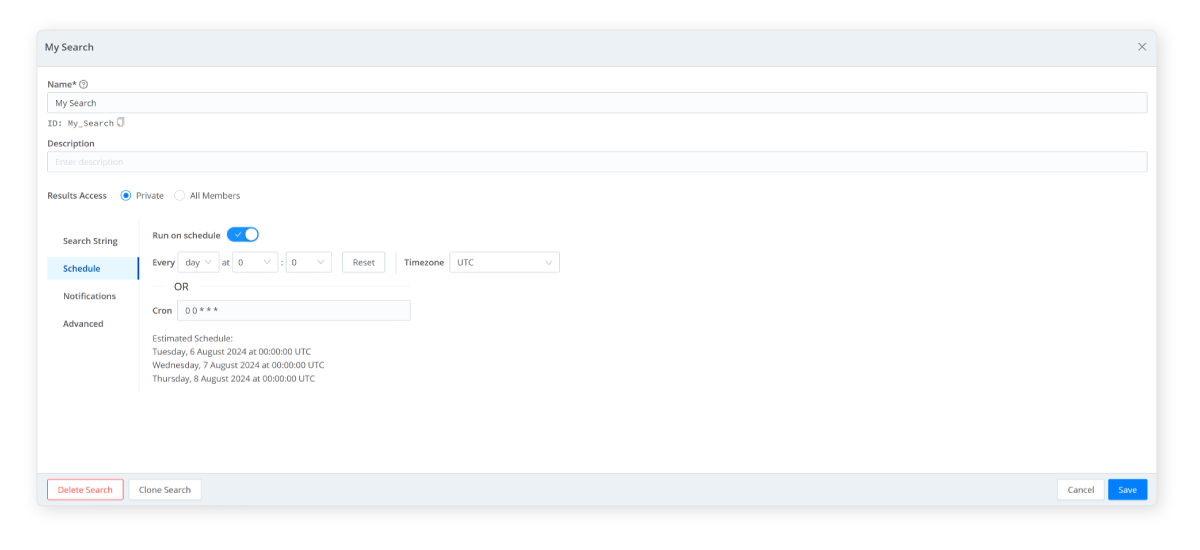
- These queries can be launched as ad hoc searches or on a defined schedule, such as hourly or weekly.
- Scheduled searches allow administrators to automate data analysis and save valuable time. By scheduling saved searches, you can effectively monitor systems, optimize workflows, and send notifications if malicious users are detected.
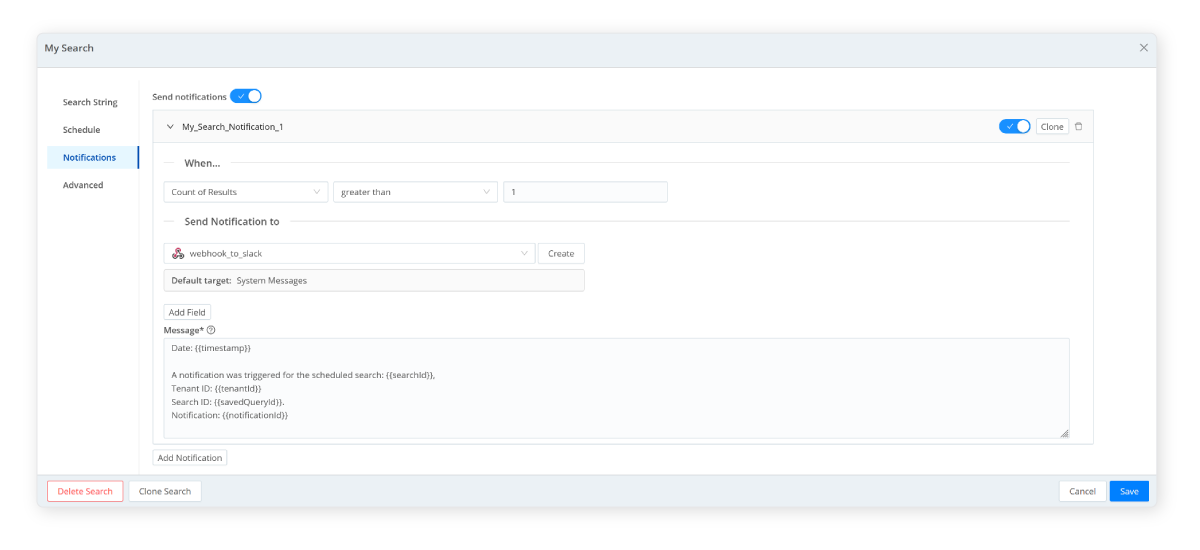
- The notification process alerts Cribl Search admins about issues that require their immediate attention. When a boolean condition is triggered, you can define when, where, and what to send. Notifications can be sent to various targets, including Webhook, PagerDuty, Slack, Amazon SNS, or Email.
- You can also create a dashboard; these customizable dashboards offer a variety of visualizations in the form of panels that you can tailor to fit your needs. Visualization panels are discrete units of display data that you can organize, interact with, and modify.
We dogfooded this in-house first and identified no suspicious IPs or clients. We also set a scheduled search with notifications and dashboards to monitor the accounts. If you want some more information or even have one of our teams provide a guided demo for your environment, then reach out to Cribl at: sales@cribl.io
Wrap up
As the Snowflake incident response analysis develops, Cribl will offer a way to easily and quickly identify any threat activity within your Snowflake account and provide peace of mind. If you are already a Cribl.Cloud customer, you can follow the instructions above and quickly better understand potential threat activity in your network. If you are new to Cribl, create a free account. It only takes 2 minutes, and you can search your Snowflake account in 10 minutes!
Cribl Search is designed to meet the unique requirements of IT and security data. It allows administrators to easily access and explore almost any system, storage type, or API endpoint from a unified interface using a single, intuitive query language.
Cribl, the Data Engine for IT and Security, empowers organizations to transform their data strategy. Customers use Cribl’s suite of products to collect, process, route, and analyze all IT and security data, delivering the flexibility, choice, and control required to adapt to their ever-changing needs.
We offer free training, certifications, and a free tier across our products. Our community Slack features Cribl engineers, partners, and customers who can answer your questions as you get started and continue to build and evolve. We also offer a variety of hands-on Sandboxes for those interested in how companies globally leverage our products for their data challenges.
Use Cases
Initiatives
Technologies
Industries
RouteOverview
Products
Services
Customer Stories
Customer Highlights






Cribl
Partners
Find a Partner










































