In today’s digital-first world, most security problems are data problems, and data volumes are outpacing organizations’ abilities to handle, process, and get value from it. You’ll have 250% more data in five years than you have today, but the chances of your budget increasing to match that are slim.
The challenges of managing the rise in enterprise data volume directly affect your ability to adequately address cybersecurity risks. Optimizing your SIEM and existing tech stack will better position your organization to handle the increasingly complex threats headed your way. These are the top three things you can do to get there.
Why Is SIEM Tuning Essential for Your SIEM Optimization Strategy?
Managing a SIEM system comes with its unique set of challenges. From overwhelming volumes of alerts to ensuring each notification is relevant and actionable, these issues can significantly impact the effectiveness of a SIEM system. Below, we delve into some common data management challenges and explore strategies to address them effectively.
Tackling the Overload of Alerts
Security Information and Event Management (SIEM) systems are critical for maintaining network security, but one of the most prevalent challenges they face is the overload of alerts. This issue arises from the system’s hypersensitivity to potential threats, leading to a barrage of alerts, many of which may be false positives. This situation strains IT resources and risks important alerts being overlooked in the deluge.
Organizations should focus on refining alert configurations and employing advanced analytics to tackle this challenge. This involves setting more precise criteria for alerts and integrating machine learning algorithms to analyze patterns and reduce false positives. Regularly updating and tuning the SIEM’s rules and parameters is essential to keep pace with evolving threats and changing network environments.
Minimizing the Noise in Alert Systems
Minimizing noise in SIEM alert systems is crucial for efficient security management. “Noise” in this context refers to irrelevant or non-critical alerts that clutter the system, making it harder to identify genuine threats. High volumes of such noise can desensitize IT staff to alerts, potentially leading to missed detections of actual security incidents.
Organizations should focus on enhancing their alert filtering and prioritization processes. This can be achieved by integrating contextual information into the alert system, such as user roles, network segments, and the assets’ criticality. Additionally, employing correlation rules that distinguish between isolated events and patterns indicative of a genuine threat can significantly reduce noise.
Ensuring Alerts are Significant and Relevant
The significance and relevance of alerts are paramount in a SIEM’s efficiency. An alert is only as useful as the action it prompts. If the alerts are insignificant or relevant to the organization’s specific security needs, they can lead to wasted efforts and overlooked vulnerabilities.
To ensure alerts are meaningful, organizations should conduct regular reviews of their SIEM settings and the underlying threat intelligence. Aligning the SIEM’s operation with the organization’s specific risk profile and security policies is essential. Furthermore, incorporating feedback from IT staff on the ground can lead to continuous improvement in the alerting process, making sure that the system is both responsive and precise in its threat detection capabilities.
In summary, tackling these challenges involves a combination of technological refinements and strategic management of the SIEM system, ensuring that it remains an effective tool in the organization’s cybersecurity arsenal.
How to Optimize Your SIEM?
Optimizing your Security Information and Event Management (SIEM) system is essential to enhance its efficiency and effectiveness in threat detection and response. The key lies in fine-tuning its settings and procedures to align with your specific security needs and the dynamic nature of cyber threats. Here are some crucial steps to optimize your SIEM system:
Tuning Detection Rules
The heart of a SIEM’s functionality lies in its detection rules. By regularly reviewing and updating these rules, you can ensure that they accurately reflect the latest threat landscapes and your organization’s specific security concerns. This process involves removing outdated rules, adjusting existing ones, and adding new rules to detect emerging threats, thereby maintaining the relevancy and effectiveness of your SIEM system.
Adjusting Alert Thresholds
Alert thresholds are critical in determining what constitutes a potential security incident. Fine-tuning these thresholds helps in reducing false positives and focusing on genuine threats. This requires a balance between sensitivity and specificity – setting thresholds too low might overwhelm you with alerts, while setting them too high could mean missing critical incidents. Periodic adjustments based on current threat intelligence and past incident data are essential.
Add Context to the Data in Your SIEM
Enhancing the data in your SIEM with additional context can significantly improve its effectiveness. This means integrating information about your network architecture, asset criticality, and user behavior patterns. Such context helps in accurately interpreting the significance of alerts, aiding in quicker and more effective decision-making while reducing the chances of overlooking critical alerts amidst false positives.
Improve Data Quality With Normalization
Normalization of data fed into your SIEM is vital for accurate analysis and correlation. This process involves transforming disparate data formats from various sources into a standardized format. It ensures consistency in processing and interpreting data, leading to more reliable detection capabilities and facilitating easier cross-referencing of data from different sources.
Testing Your SIEM
Regular testing of your SIEM system is crucial to validate its effectiveness. This involves simulating various security scenarios to see how the system responds. Testing helps identify any gaps in detection capabilities and provides insights into potential areas for improvement, ensuring that the system remains robust and responsive to evolving threats.
Ongoing Performance Monitoring
Continuous monitoring of the SIEM’s performance is essential for its long-term effectiveness. This includes tracking key performance indicators like the number of alerts generated, response times, and the rate of false positives. Regular monitoring helps quickly identify and address any performance issues, ensuring that the SIEM operates optimally.
Regular SIEM Audits
Conducting regular audits of your SIEM system is critical for maintaining its health and efficacy. Audits comprehensively review the system’s configurations, rules, and procedures. They help identify outdated practices, compliance issues, and areas where the system can be optimized for better performance. Regular audits ensure that the SIEM is in line with the evolving security needs of the organization.
Optimizing a SIEM system is an ongoing process that requires regular attention and adjustments. By following these steps, organizations can significantly enhance their SIEM’s efficiency and reliability, making it a more powerful tool in their cybersecurity arsenal.
Improve Data Quality With Normalization
Each source of security data tends to come in its own format — if you have a dozen sources feeding data into your SIEM, it wouldn’t be crazy for one user to have completely different field names across each source.

If this happens for each user — across multiple fields and events — the extra noise created quickly adds up. The vast sea of extra data makes creating security rules, correlation rules, alerts, and dashboards in your SIEM problematic, so you end up with gaps in visibility that make threats impossible to detect.
Events that don’t meet formatting requirements may be dropped by a SIEM altogether. The variations in data can also appear anomalous, causing the SIEM to send unnecessary alerts, also known as false positives. It’s easy to go from missing threats you can’t see to losing them in a list of alerts that will never see the light of day. Reducing false positives free up analysts to triage actual security issues.
Add Context to the Data in Your SIEM
Although they come in multiple formats, usernames have all the context you need — but things like IP addresses are a different story. You can see a couple of IP addresses in this simple log entry from Cisco SA, but all we really know is that one is a private address, and the other one is public.
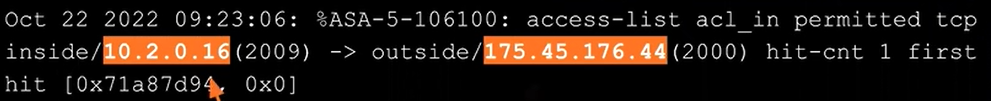
GeoIP information for these IPs is critical for investigations, but jumping between different tools to figure out a location for each log takes up valuable time. It can also be troublesome because you could potentially attach current GeoIP information to an IP address from a couple of years ago. In the example above, the external IP address is from North Korea, but it might not be a North Korean IP address a year from now.
Strike the Right Balance Between Data Quantity and Quality
Data volume is an issue with most environments when it comes to SIEM tuning and optimizations — chances are that you’re a part of the significant percentage of organizations that don’t even ingest all the data they need in their SIEM. If you don’t collect everything you need to because of infrastructure, network traffic, or license costs — or the desire to control the load on all the agents you need to get all the necessary information — you’ll likely have some significant security vulnerabilities.
In many cases, voluminous data sources like network flow logs are the most valuable from a security perspective. You should also collect DNS traffic and endpoint logs, but in a way that allows you to afford to run all the services you need. The more unnecessary data you collect, the more you distance yourself from more real-time alerts.
In our recent webinar, we discuss how Cribl Stream enables your existing set of tools to handle increases in data volume and improve your organization’s security posture. Data normalization, enrichment, and reduction are just the tip of the iceberg. Stream allows you to use data lakes to take advantage of deep analytics, reporting, and searching without causing resource contention with your SIEM. You can hold onto a much smaller, more intentional portion of data, dump the full-fidelity copies of data into object storage, and use the replay feature to put a session back through your SIEM if needed.
You probably have all of the right tools in place already — making sure that you’re feeding them the proper data will help ensure your organization is as secure as possible. Check out the presentation for more information, including a live demo of Cribl Stream and answers to some great questions, like why it’s better to do enrichment in the pipeline as opposed to your SIEM, and much more.